Adding Connectors to Gateway Environments
When it comes to recording API traffic on API Proxies in environments, you can set where the relevant logs should be stored with the following settings.
The following connectors can be used to send API traffic in gateway environments to other environments:
- Database Connector
- Elasticsearch Connector
- Kafka Connector
- RabbitMQ Connector
- ActiveMQ Connector
- Syslog Connector
- Webhook Connector
- Logback Connector
You can take a look at this document to examine the structure of the data to be sent to these connectors.
The picture below shows the adding connectors to gateway environments:

- Querying and analytically visualizing the relevant API Traffic in the Apinizer API Manager is only possible by adding the Elasticsearch Connector to the relevant environment.
- If more than one Elasticsearch Connector is defined, the data from the first added Elasticsearch Connector can be viewed in the Apinizer API Manager.
- If the Elasticsearch Connector has never been added, the following pages/menus are completely disabled:
- All analytics-related screens and menus
- API Proxy's Trace, API Traffic and Analytics tabs
- Anomaly Detector in the monitor menu
- Analytics section of the Overview in the Administration menu
- OAuth2 policy
- Log tab in the test console
- Token Requests in the control menu
- Report generator menu
- Dashboard and API Traffic in the Portal
Common Areas in Connectors
When creating a connector, there are some input fields that are the same for each type. This information is in the selected fields in the image below.
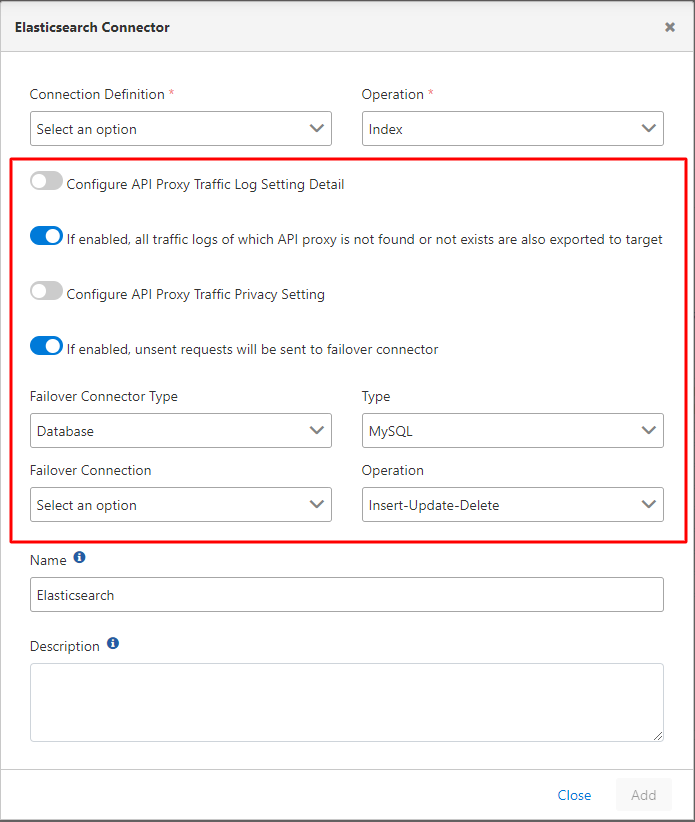
The fields used for configuring common information in the connectors are shown in the table below.
Field | Description |
|---|---|
Configure API Proxy Traffic Log Setting Detail | When this setting is activated, the areas to be logged are selected. If long texts are among the fields to be sent for logging, size limits can be set for these fields. |
If enabled, all traffic logs of which API proxy is not found or not exists are also exported to target | With this setting, if desired, all traffic logs where API Proxy is not present or not available are also transferred to the target. |
Configure API Proxy Traffic Privacy Setting | When this setting is activated, data that is not explicitly intended to be accessed in the log records can be prevented from being displayed as is. Detailed information about this section is explained below. |
If enabled, unsent requests will be sent to failover connector | If the connector is offline or inaccessible, then a new failover connection can be defined for log records that cannot be sent. |
Failover Connector Type | The type of failover connector to be defined is selected. |
Type | This field becomes active if the failover type is selected as Database. Database type is selected. |
Failover Connection | The failover connection to be defined is selected according to the selected failover type. |
Operation | This field becomes active if the failover type is selected as Database. The operation type is selected. |
Configure API Proxy Traffic Log Settings Details
When the “Configure API Traffic Log Setting Detail” option is enabled, you can customize how API traffic logs are recorded. Apinizer logs are divided into four different zones according to the traffic flow in the system.
API Traffic Log Zones
Apinizer logs API traffic in these four zones:
- Request from Client to Apinizer
- Request from Apinizer to Backend
- Response from Backend to Apinizer
- Response from Apinizer to Client
When the "Configure API Traffic Log Setting Detail" option is enabled, logging for each of these zones can be customized.
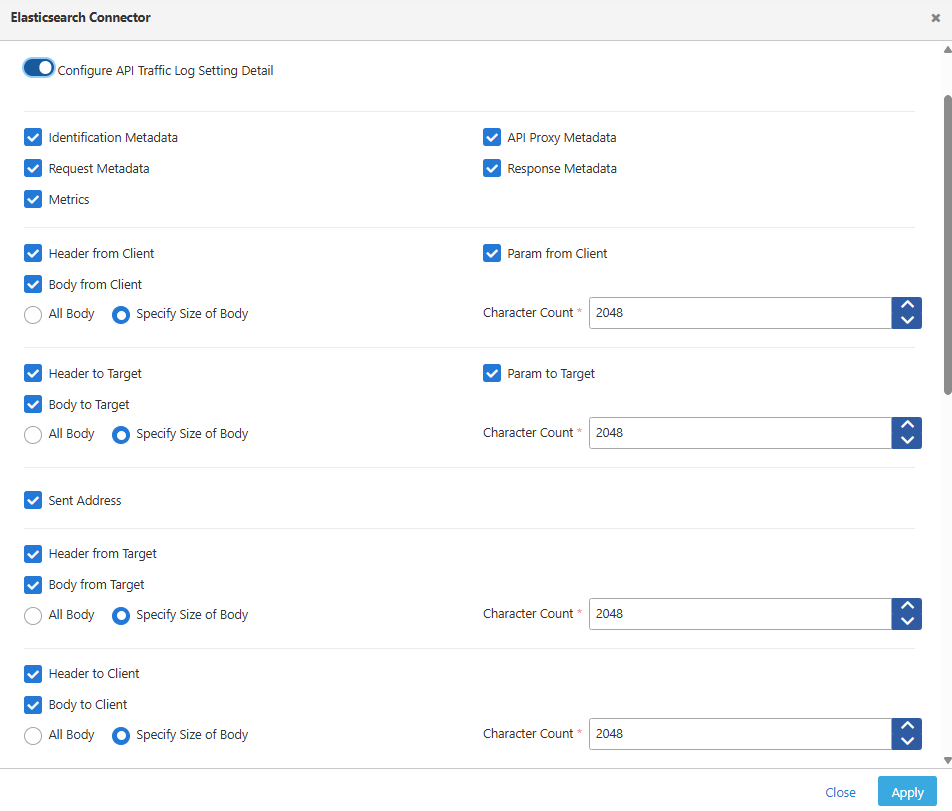
The fields that can be customized in API traffic log settings are given below.
Customizable Log Fields
| Field | Description |
|---|---|
| Identification Metadata | Records system identification information |
| Request Metadata | Captures request-specific metadata |
| API Proxy Metadata | Logs proxy-related metadata information |
| Response Metadata | Records response-specific metadata |
| Metrics | Captures performance and timing metrics |
| Header from Client | Records all headers received from the client |
| Body from Client | Captures the request body from client |
| Param from Client | Logs parameters received from client |
| Header to Target | Records headers sent to the backend |
| Body to Target | Captures the request body sent to backend |
| Param to Target | Logs parameters sent to backend |
| Sent Address | Records the address information for the request |
| Header from Target | Records headers received from the backend |
| Body from Target | Captures the response body from backend |
| Header to Client | Records headers sent to the client |
| Body to Client | Captures the response body sent to client |
Configuring API Proxy Traffic Privacy Settings
It keeps records of message traffic (request and response) flowing through Apinizer.
Any part of the messages (header, parameter, body) may contain sensitive or personal data such as credit card information, password, phone number.
In cases where it is not desired to openly access these data in the log records, the following operations can be applied to the sensitive/confidential fields in the log records with the Apinizer "API Proxy Traffic Privacy Settings", preventing the data from being displayed as it is:
- Masking: A mask with * is applied to the value of the field.
- Delete: The value of the field is deleted while logging.
- Encryption: The value of the field is encrypted with the pure code generated on the basis of the application.
- Hashing: The value of the field is hashed and logged.
API Proxy Traffic Privacy Settings is only about storing the data in the log records kept on Apinizer. It is not related in any way to data going to the Backend API or data returning to the Client! You can use policies to act on this data.
Implementation of Privacy Management
At the time of creation of the log record, element names defined and "header, parameter and body" fields of request and response messages are scanned. For the element names found, the operation (masking, deletion, encryption, hashing) defined specifically for the element name is applied.
To search for the element name on the request or response body, the body value must be XML, JSON or Form data (form-data, x-www-form-urlencoded).
If the data is XML or JSON (recursive), the value of "sensitive data element name" is searched in all element names, if it is form data, in all keywords. The suffix "-PA" is added to the end of the relevant element/key name on the data to indicate that the operation is also performed. PA: stands for Privacy Applied.
In order to apply "API Proxy Traffic Privacy Settings" per a defined area, all the following areas are scanned:
- Header, Query Parameter and Body of the Message From the Client
- Header, Query Parameter and Body of Message Outgoing to Backend
- Header and Body of Message Returned from Backend
- Header and Body of the Message Returned to the Client
As can be seen from the scanned areas, API Proxy Traffic Privacy Settings is a costly process in terms of performance.
Since logging operations are performed asynchronously, although it does not have an effect on API Traffic, if it will be used intensively, system configuration should be done considering its effect on processor power.
Definitons
To enable "API Proxy Traffic Privacy Settings", the Enabled option must be enabled.
The picture below shows the screen that appears when API Proxy Traffic Privacy Settings is activated:
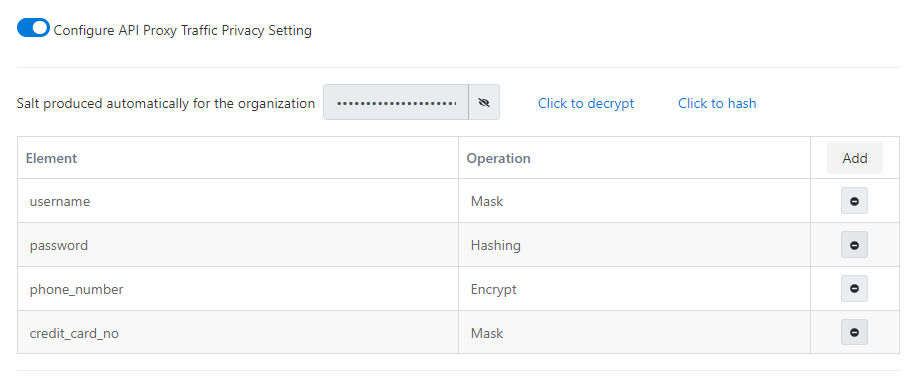
The "element name" and what to do with that description ("operation" information) binaries are defined. It is added to the definition list with the Add button.
An element name and related operation defined here applies to all API Proxies.
When a definition is created it is automatically added to all API Proxies. When a definition is deleted, this setting is removed from all API Proxies.
If an API Proxy is not available, all definitions are applied to incoming requests.
What is the Salt?
One of the API Proxy Traffic Privacy Settings processes is hashing.
When the hashing method is selected, it is ensured that the data is hashed with an algorithm in a way that is not reversible. The hashed data is one-way and cannot be retrieved. Only hash data can be reproduced.
By choosing the hash algorithm with Salt, the output that would normally be formed is created differently, thus preventing the hash value from being found by comparison.
When API Proxy Traffic Privacy Settings is first activated, Apinizer creates a pure value and hash the data with it.
Normally, it seems more correct to hash each value with different salts, but in some cases, it may be necessary to find the data by searching or to know that the value of the data is correct, so this salt is kept secretly without being changed by Apinizer. The user is allowed to create the same hash data on the screen by entering a value.