Applying Plain-Text Authentication Policy to REST API via Database Provider
In this scenario, we will test the implementation of a Plain-Text Authentication policy in a REST architecture API called Swagger Petstore.
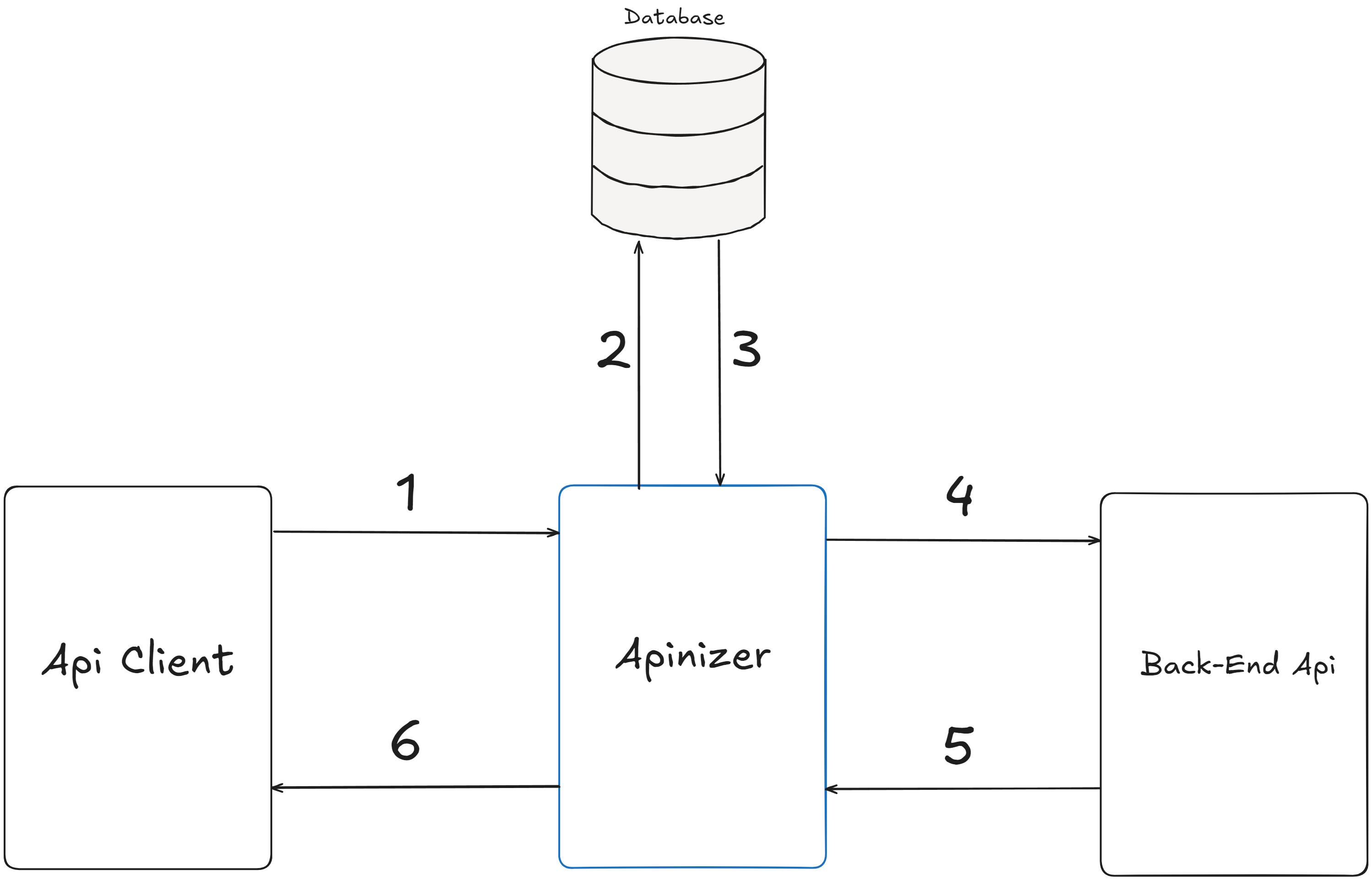
The numbering in the graph below refers to the order in which the operations are carried out.
- Security Manager in Apinizer waits for security information in Plain-Text type from API Client.
- Authentication information is sent to the database to be checked.
- The Apinizer receives a response from the database with authentication information. If this authentication cannot be verified, Apinizer interrupts the request and returns an error message by skipping to step 6. If the authentication can be done, the flow continues.
- Apinizer makes a request to the Backend API.
- Backend API responds to Apinizer.
- The Apinizer forwards the response to the API Client.
Creating the API Proxy
The REST API named Swagger Petstore can be accessed from https://petstore.swagger.io/.
First, this address needs to be defined as API Proxy.
For this, click on API Proxies under the Development menu.
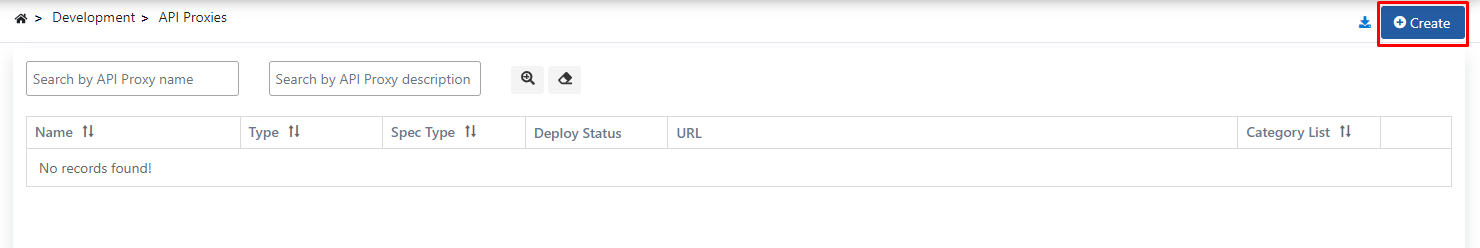
On the page that opens, there may be the text No records found! because no proxy definition has been made before.
Click on the Create button in the upper right corner and start creating a new proxy.
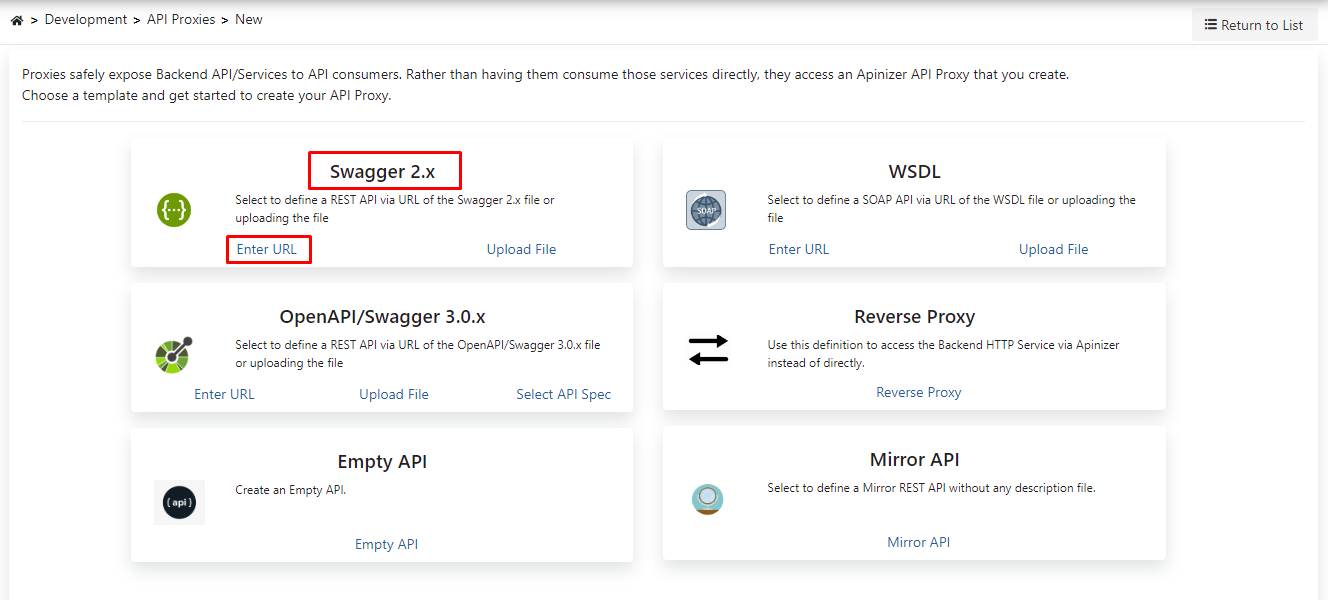
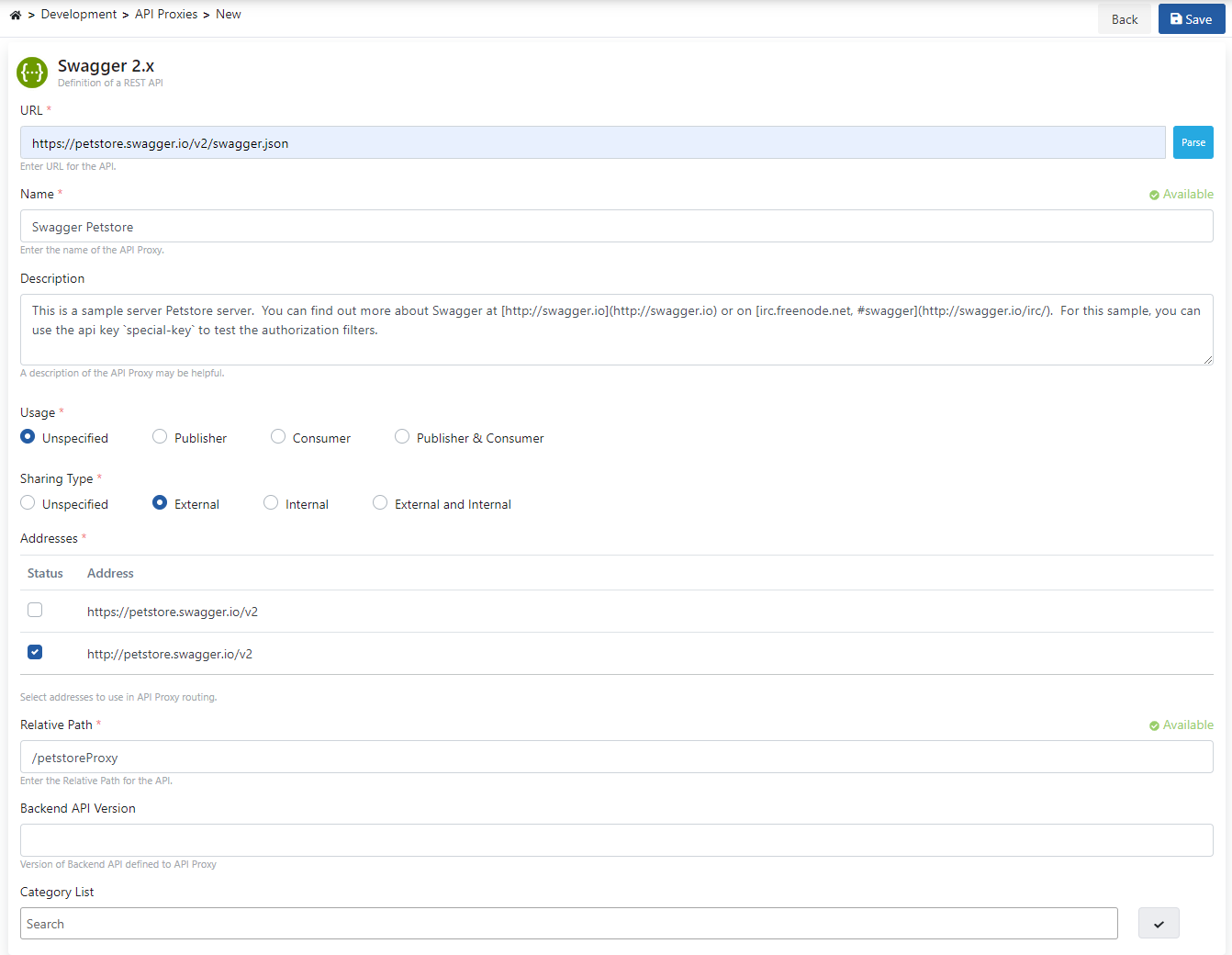
In this section, it is necessary to select the type of API Proxy to be created.
Since the type of API to be used in this scenario will be Swagger 2.X, this type is selected.
Click on Enter URL to switch to the screen where the address of the API to be used will be entered.
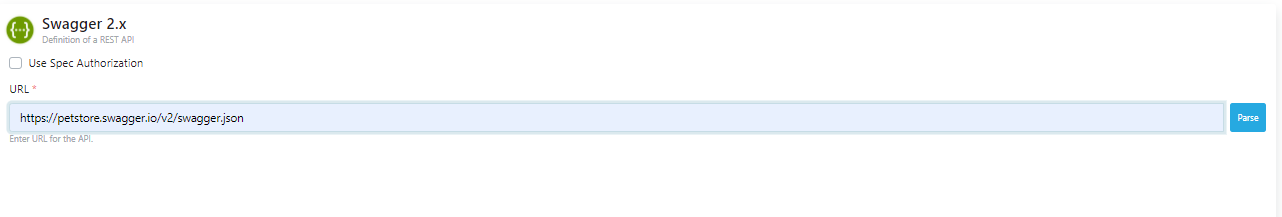
As seen in the image below, enter the end address of the document to be accessed in the URL section and click the Parse button.
After the parse process is done, the screen in the image below appears.
Settings for API Proxy can be made on this screen.
- The Usage field specifies who will use the API Proxy created. There are options such as publisher, consumer, publisher and consumer.
- Sharing Type field specifies the sharing type of the API Proxy created. There are options such as external, internal, external and internal.
- One or both of the two API addresses under the Addresses tab can be selected, if both addresses are selected, Apinizer will perform the Load Balance process itself.
- Relative Path is the address of the API Proxy to be accessed.
- The Category List field also allows the categorization of the created API Proxy.
- After these adjustments are made, the API Proxy is registered.
After saving, click on the Develop tab on the page that opens.
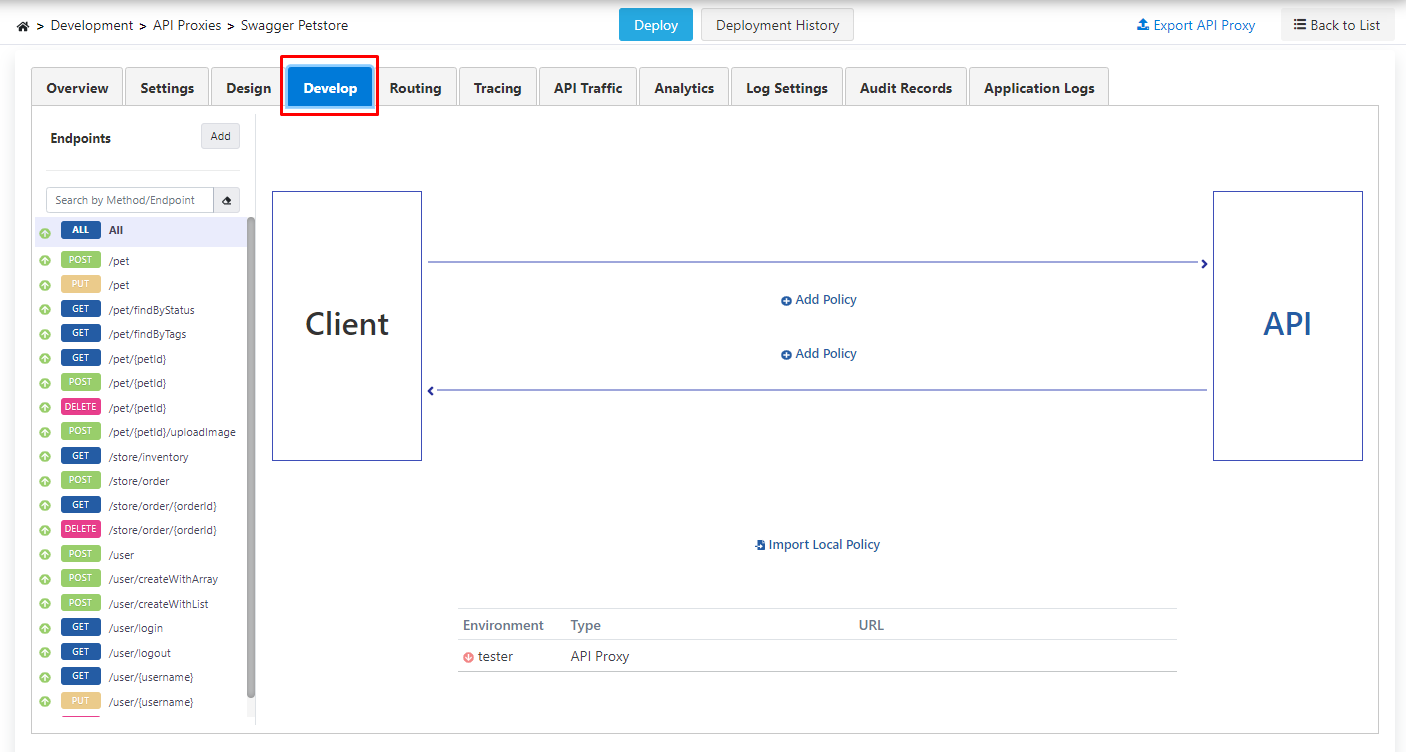
This lists the methods (endpoints) of the REST API.
- Policies to be added with the All statement above these endpoints can be applied to all methods.
- The created API proxy is deployed. For this, click on the Deploy button in the middle above.
- The next step is to define the database connection that should be used in this process as per the scenario.
- If an example of the username and password pair to be checked in the Plain-Text Authentication structure to be added as a policy is known, the flow can be tested at the end of the operations.
- First, the database connection is made and then Authentication with Database settings are made.
Realization of Database Connection
- Click on the Database menu under the Connection Management menu.
- If no database definition has been performed before, No records found! can be seen on this page.
- Click on the Create button in the upper right corner to create the database connection.
If the statements on this screen are examined one by one,
- The name of the connection created with the Name field.
- A description can be added to the link created with the Description statement.
- With the JDBC URL field, the JDBC address required to connect to the database to be connected is written. This information can be obtained from the database team.
- Username field is used to enter the username to be used during the connection and Password field is used to enter the password to be used during the connection.
- This section is edited by getting information from the database administrator or team about the most appropriate values for the connection information on the right side.
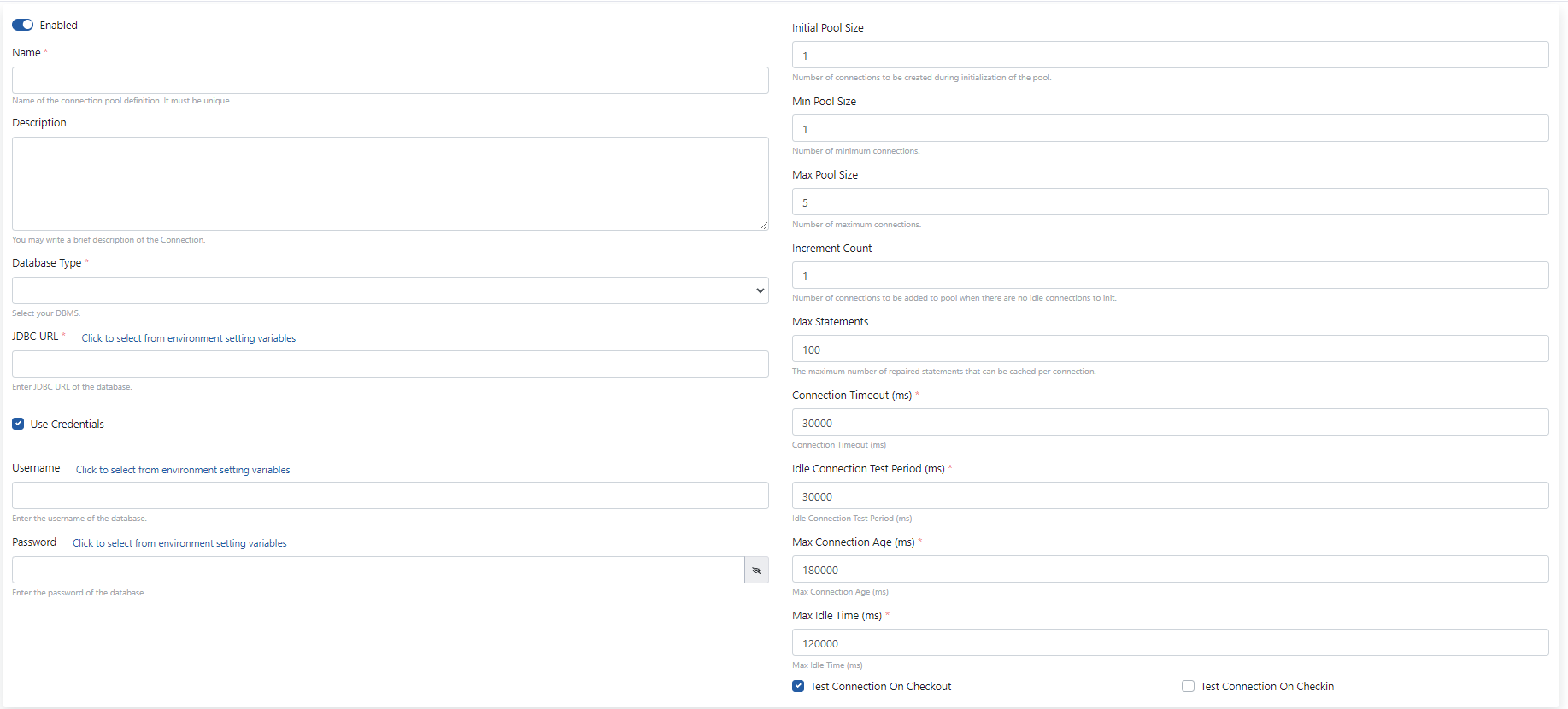
The fields above are filled in as they will be used in the scenario.
Click on the Test Connection button to perform the test and click on the Save and Deploy button to save the process.
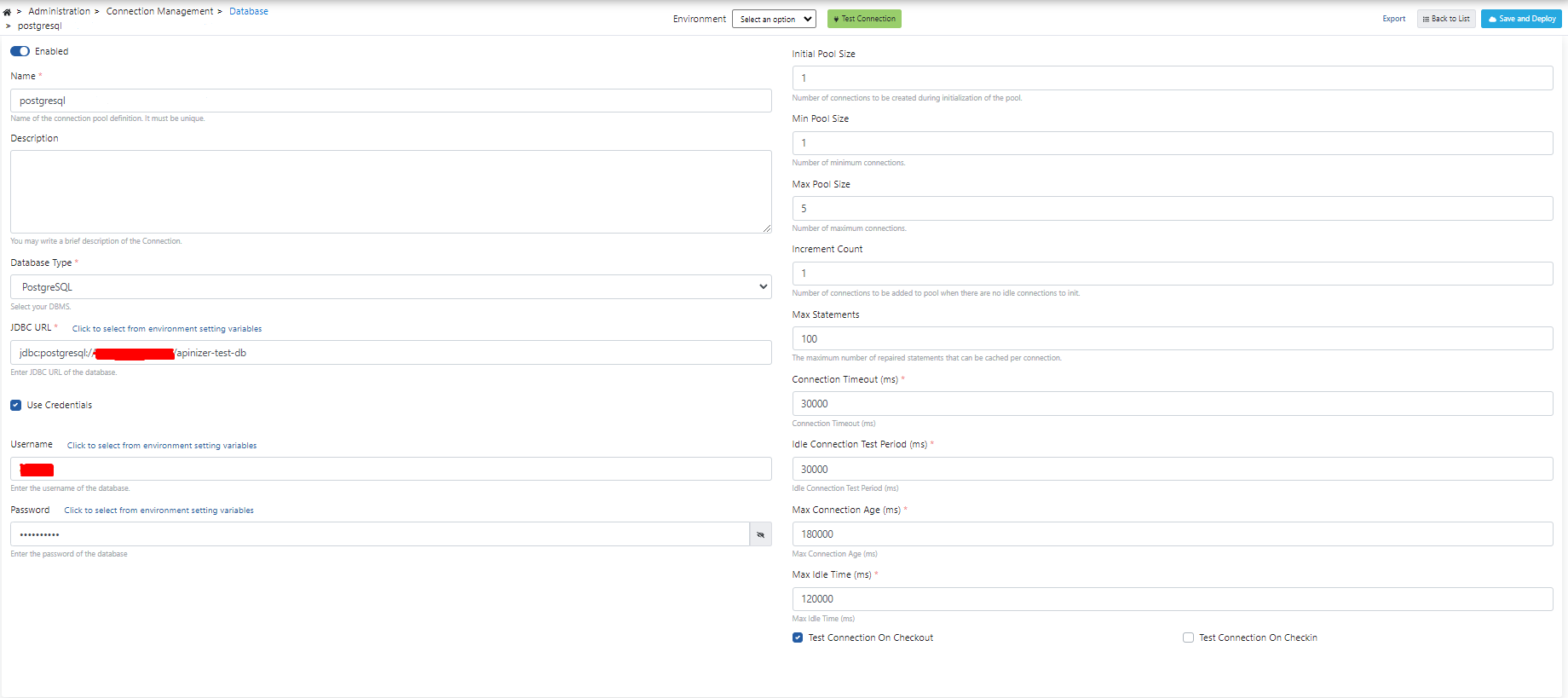
After the registration process is completed, the link created is displayed as in the image below.

Adding Authentication Connections with Database
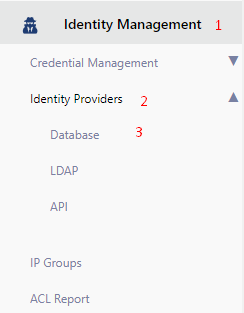
As you can see below, you can login from Identitiy Management > Identity Providers > Database section to add the authentication definition with the previously created database.
Authentication Connection with Database
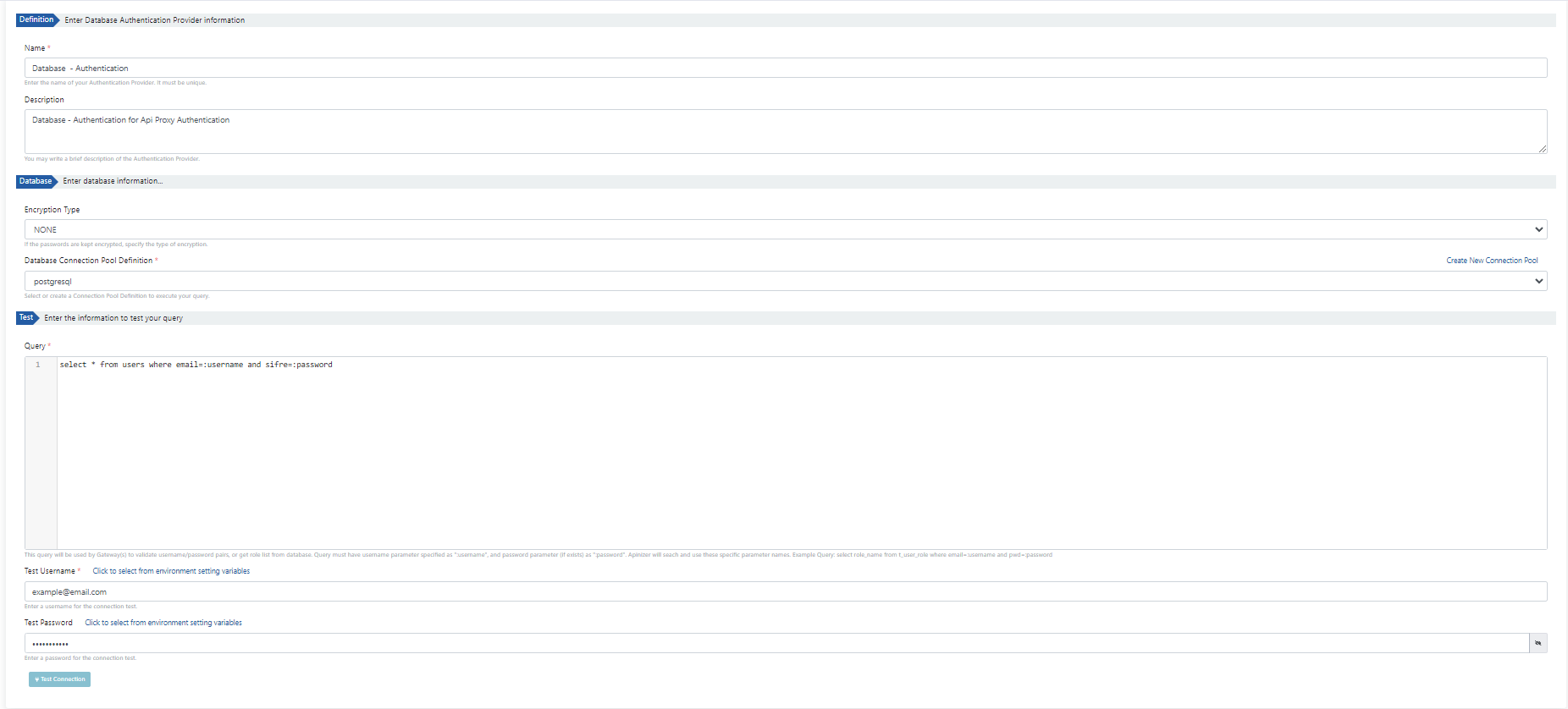
After logging in to the relevant page, press the Create button and enter the connection settings as shown in the image below.
- Enter a name and description for the link.
- If the password information is kept encrypted in the table to be used in the database connection with Encryption Type, the encryption type of the password kept in the table should be selected.
- Select the database prepared in the previous steps with the Database Connection Pool Definition field.
- A query is used to retrieve username/password pairs or role list from the database. In the query, the username parameter must be defined as “:username” and the password parameter as “:password”. The apinizer recognizes the colon character and acts accordingly, knowing that the parameter will be sent from outside.
- The Test Username and Test Password fields can be tested to see if the query works by filling in information from the database. It is recommended to clear these fields before saving the definition.
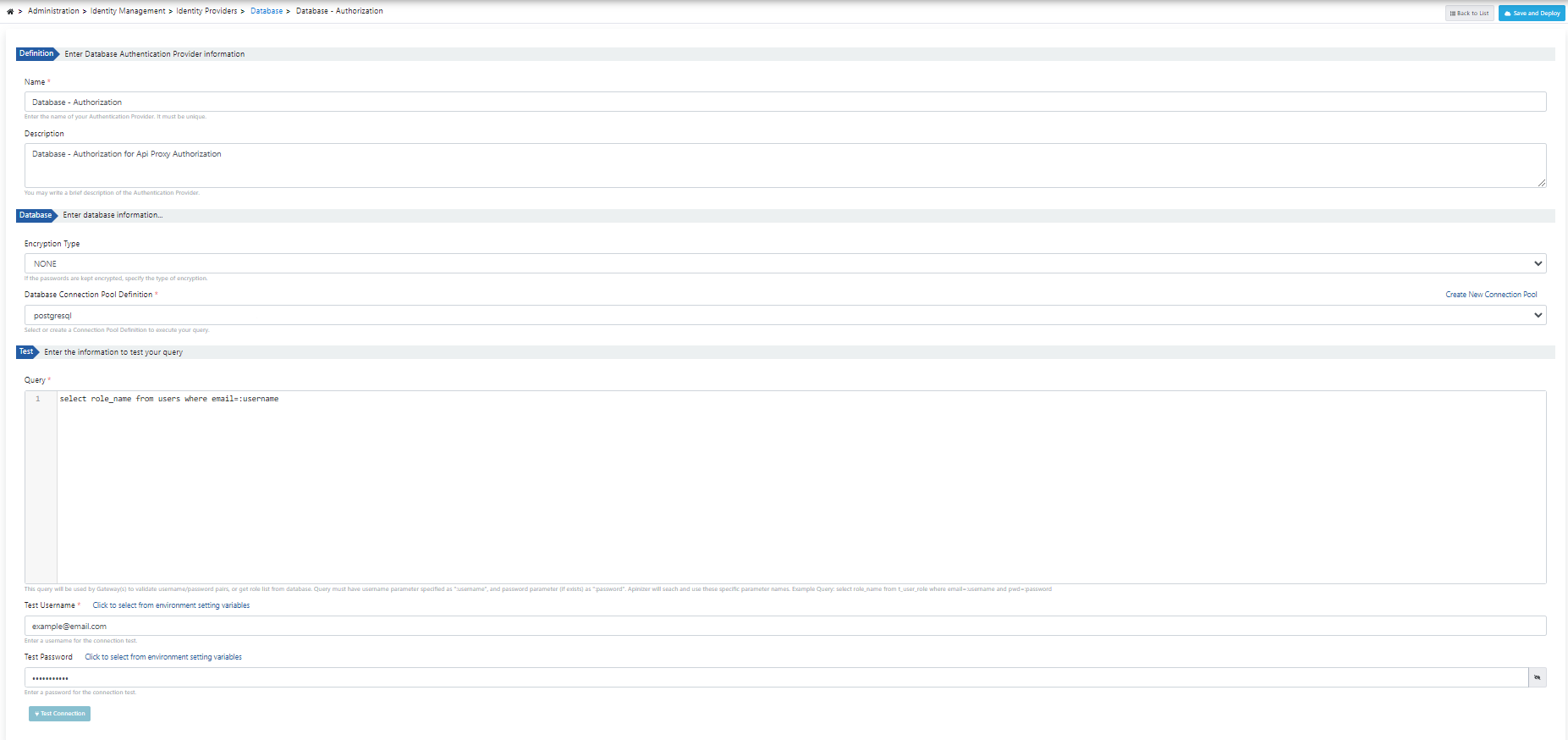
Identity Authorization Connection with Database
The only difference from the authentication link is the query entered, since the identity authorization process will be performed in this field, only the name of the relevant role is taken in the query section.
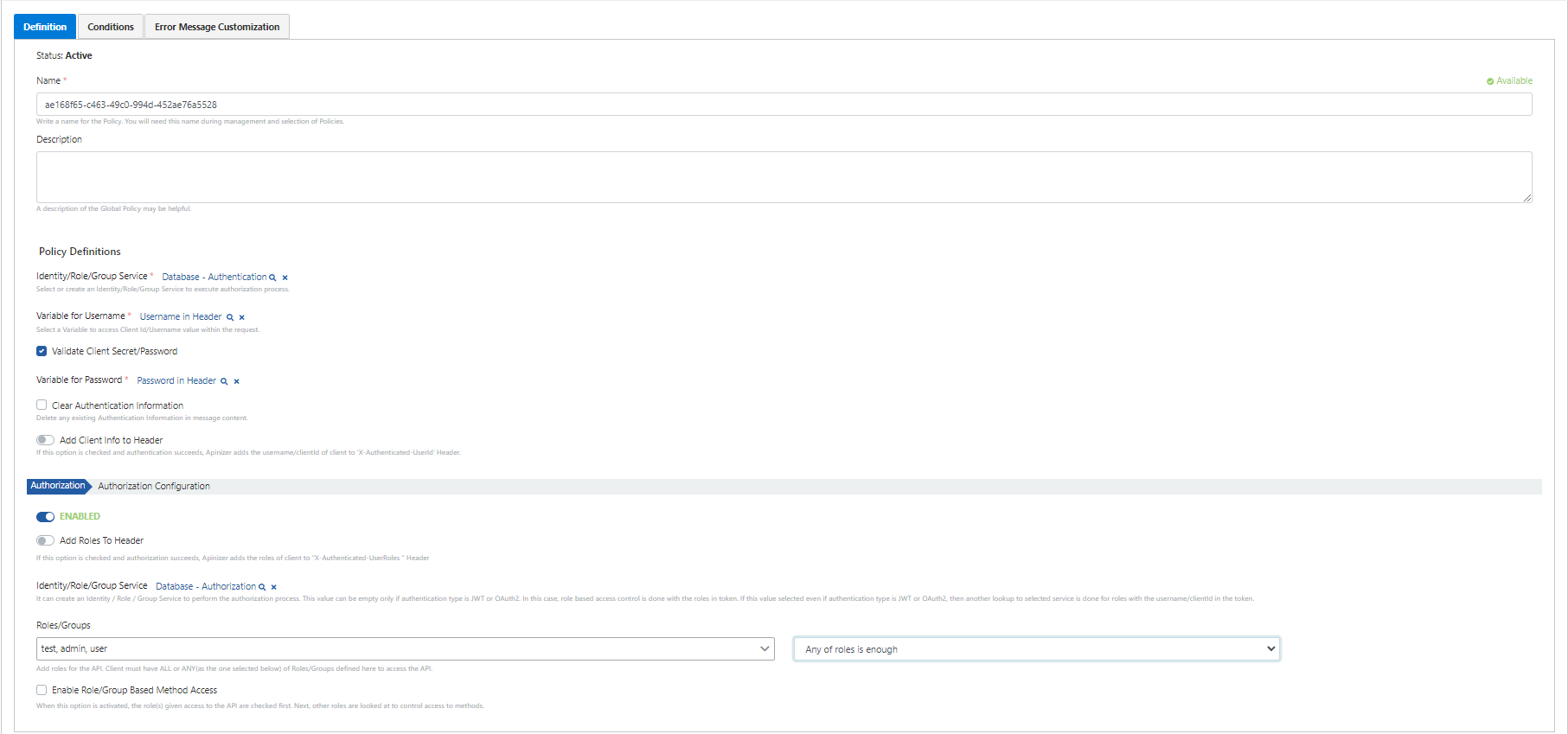
Creating Authentication Policy
Go to the page where API proxies are listed and select the proxy named Swagger Petstore.
Then go to the Develop tab and click on the Add Policy button.
Select the Plain-Text Authentication policy on the page that opens.
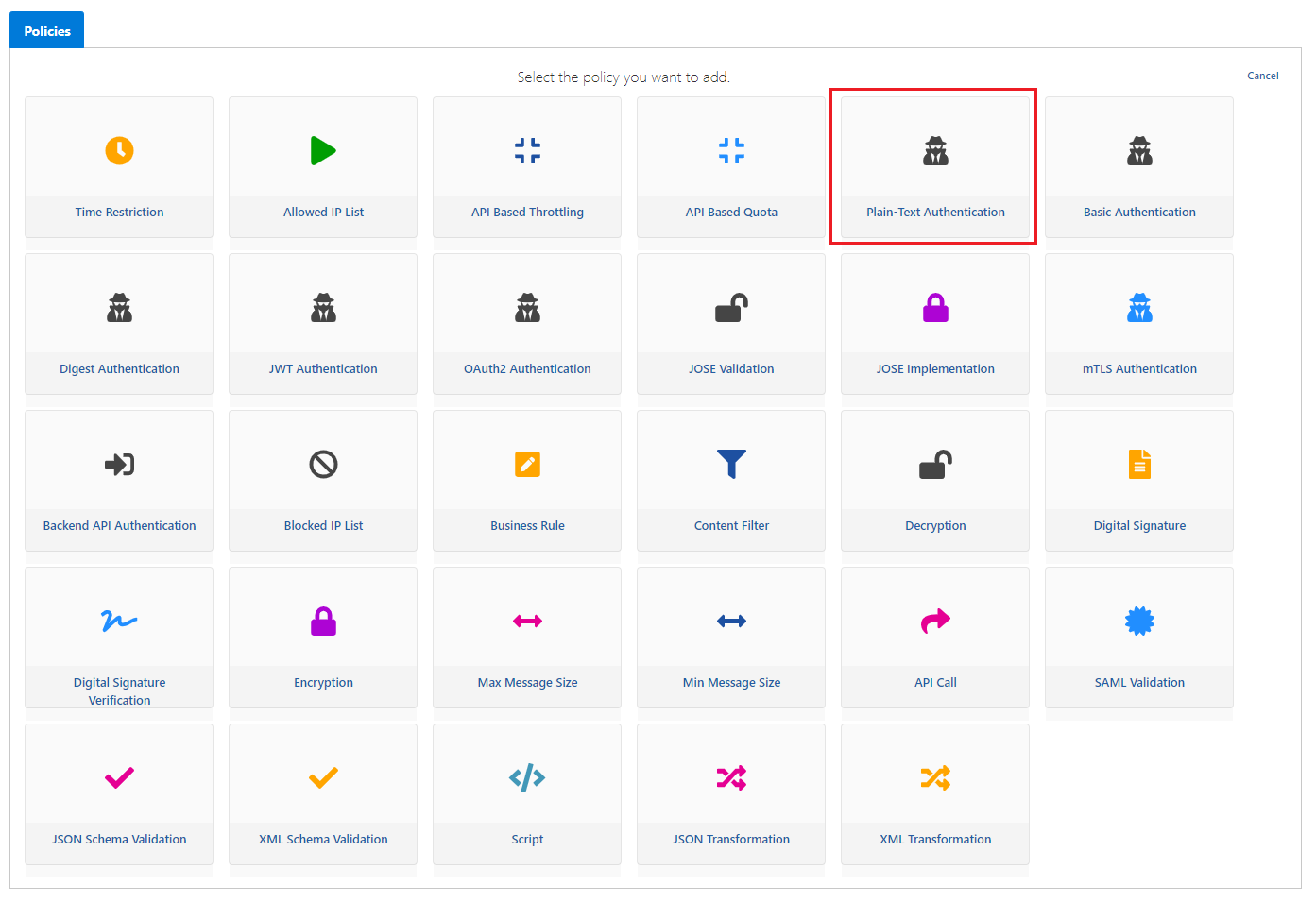
If the statements on the screen below are examined one by one,
- In the Identity/Role/Group Service field, select the database that will provide control from the database section.
- Variable for username and variable for password are used to select which variable to get the username and password information. In this scenario, these values will be expected and received in the username and password values in the header.
- If Clear Authentication Information option is selected, authentication information is cleared in the incoming message on the way to the backend API. Activating this setting is always recommended unless there is a special situation.
- Add Client Info To Header option allows the user name to be transmitted with a separate header value in the Header that will go to the backend API.
- This is the field where rules can be entered about the roles of people who are authenticated in the Authorization Configuration field.
- If the Add Roles To Header option is selected, it adds the client's roles to the “X-Authenticated-UserRoles” header if the authorization is successful.
- In the Identity/Role/Group Service field, the database containing the role information is selected from the database to be selected section. This is usually done with the same definition as the database that provides identity control.
- In the Roles/Group field, enter the roles for identity authorization.
- Set whether the client needs to have all or any of the roles/groups defined here to access the API.
- When Enable Role/Group Based Method Access is selected, the roles that are allowed access to the API are checked first. Then, other roles are checked to control access to methods.
When the policy is registered, the icon enclosed in a red rectangle is visible.
The proxy must be redeployed for the operation to be valid.
API proxy can be tested after redeploy operation.
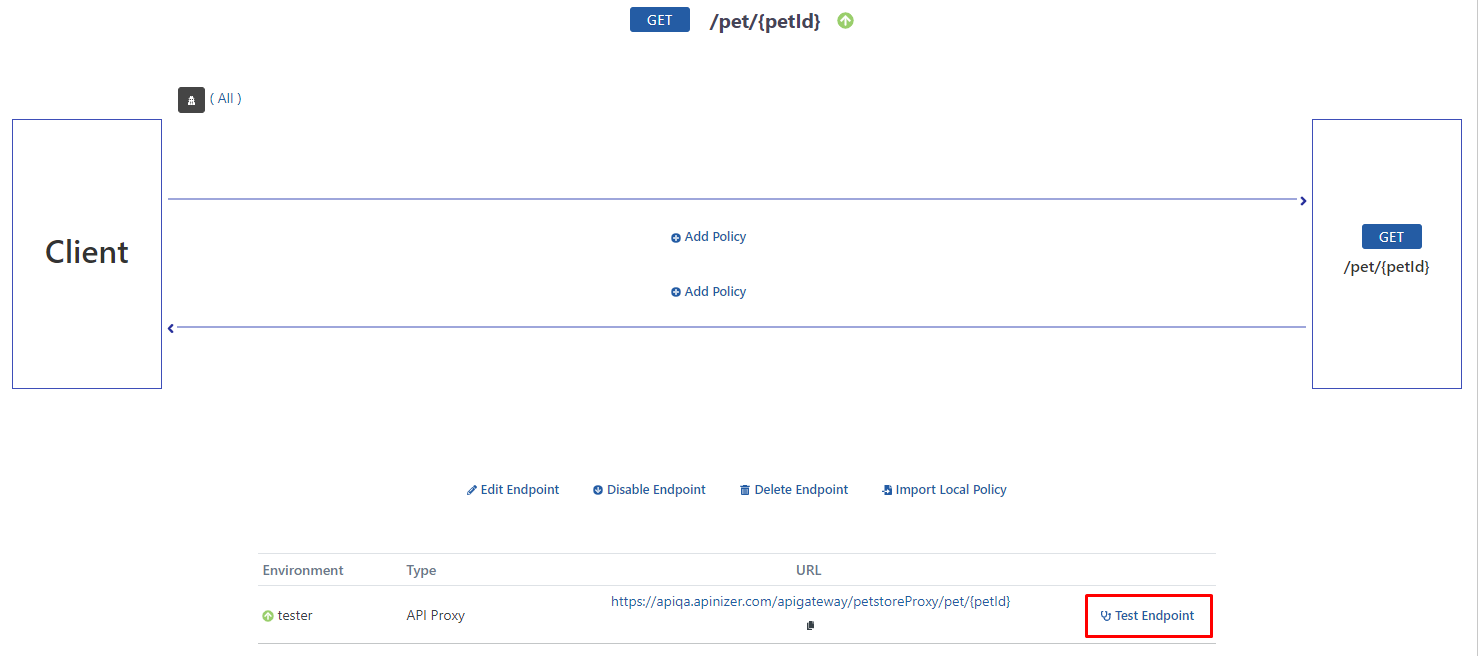
Testing the API Proxy
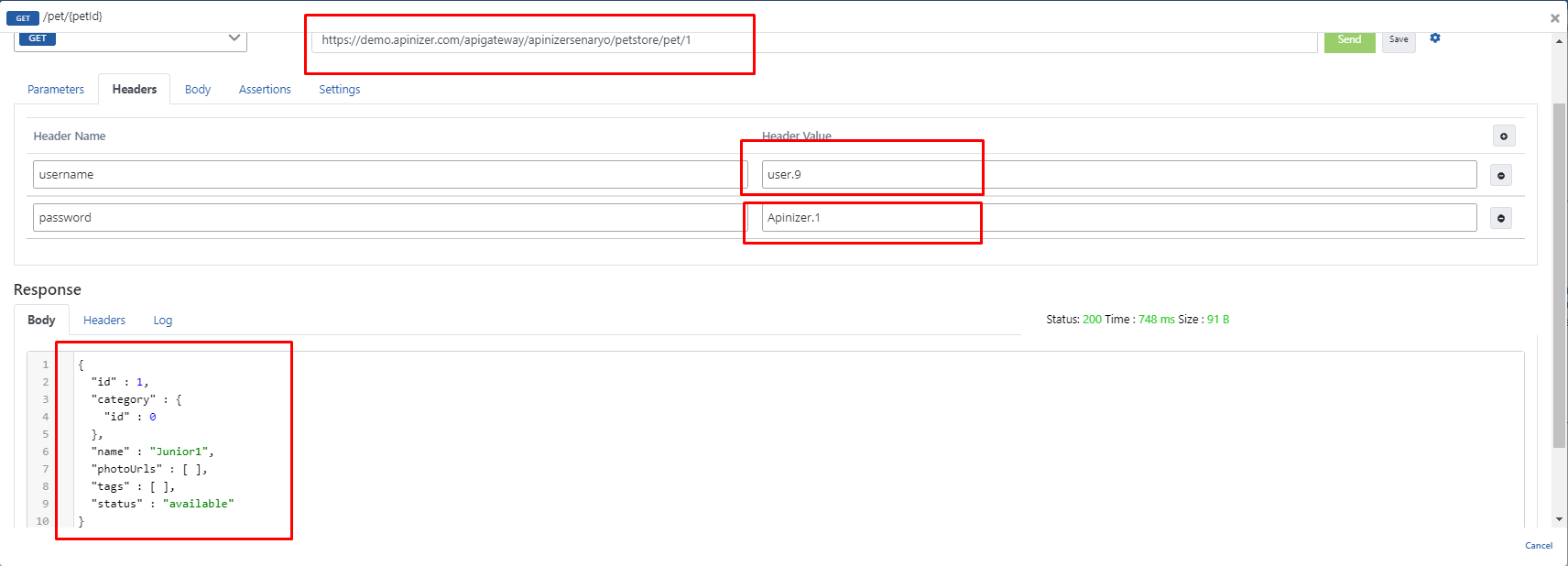
After selecting an endpoint such as /pet/{petId}, click on the Test Endpoint button.
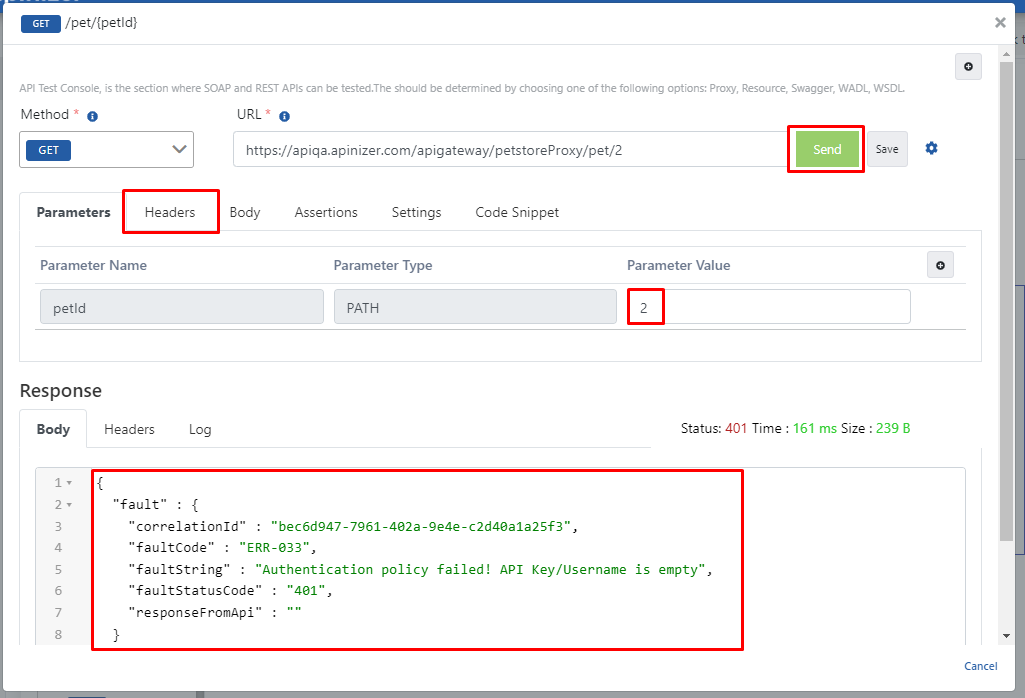
Enter the desired pet id value in the URL or in the parameter tab, when the Send button is pressed, the response returned will be an error message and it will be seen that this error is related to the Plain-Text Authentication implemented.
Because no authentication information has been placed in the headers yet.
In the headers to be sent to the Backend API, the test is repeated by entering the information of a user in the database in the username and password headers and a successful response is expected.