Manually Configure Simple Authentication on Elasticsearch
This document contains the necessary configurations to access Elasticsearch server on Apinizer with Simple Authentication method. Generally, this is done by activating the Elasticsearch security option and defining credentials through the Apinizer API Manager. If the Elasticsearch server is being created, operations are applied from the first step. If there is an Elasticsearch server, a user can be created and the identity information can be defined via Apinizer API Manager.
1.Checking Licence
Elasticsearch license must be Elastic Basic License. Apinizer uses the simple authentication method supported by the security plugin of X-Pack in this license. To check the Elasticsearch license information, the following request is made.
curl -X GET "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_xpack/license?pretty"
2. Enabling Security
By default, the Elasticsearch security setting is not enabled. To activate the security option, the following feature is added to this file located in the /config/elasticsearch.yml directory in the Elasticsearch installation file. If there is more than one node, this feature should be activated on all of them.
xpack.security.enabled: trueAfter this process, the Elasticsearch application should be restarted.
2.1 Encryption of communications of nodes in the cluster (TLS setting)
After Elasticsearch restarts, the following error is received or if there is more than one node, the settings in this section must be made. Also, when the security setting is enabled and it is running in production, it requests that the communication of Elasticsearch nodes with each other be encrypted. In addition, this communication takes place at the transport layer.
Transport SSL must be enabled for setups with production licenses. Please set [xpack.security.transport.ssl.enabled] to [true] or disable security by setting [xpack.security.enabled] to [false]If there is more than one node, this setting should be configured on all of them.
Other optional and important settings on the /config/elasticsearch.yml file for clusters with more than one node;
# Nodes must have a unique name to find the cluster.
cluster.name: ApinizerEsCluster
# When there is more than one node on the same machine, the location of the certificate can be determined on this node name, since they may have the same ip/host information.
node.name: <ELASTICSEARCH_IP_ADDRESS>
# If there is only one node, this setting can delay TLS error. But it should be deleted when there is more than one node.
discovery.type:single-node
# If there are multiple master-eligible nodes;
cluster.initial_master_nodes: ["<ELASTICSEARCH_IP_ADDRESS>:<PORT>"]2.2 Creating a Certificate
# To create certificate, use the code below. Securing these files with password is optional and can be skipped (Not recommended).
./bin/elasticsearch-certutil ca
./bin/elasticsearch-certutil cert --ca elastic-stack-ca.p12
# Certificates are moved under config/certs directory
mkdir config/certs
mv elastic-certificates.p12 config/certs/
mv elastic-stack-ca.p12 config/certs/
# Before continueing, be sure that these certificate files have same privileges as the files of ElasticsearchIf you encounter the error "could not find java in JAVA_HOME at /tools/java/home/bin/java", the following two commands can be used to set up the environment variables required for Java applications to work correctly:
export JAVA_HOME=/opt/elasticsearch/elasticsearch-7.9.2/jdk
export PATH=$JAVA_HOME/bin:$PATH
The following fields should be added to the /config/elasticsearch.yml file.
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: certs/elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: certs/elastic-certificates.p12After this process, the Elasticsearch application should be restarted.
The security enable status can be checked from the following request.
curl -X GET -u <USERNAME>:<PASSWORD> "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_xpack?pretty"
...
"security" : {
"available" : true,
"enabled" : true
},
... },
When this field is activated, every request without credentials will be rejected as follows.
curl -X GET "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>"
{
"error": {
"root_cause": [
{
"type": "security_exception",
"reason": "missing authentication credentials for REST request [/]",
"header": {
"WWW-Authenticate": "Basic realm=\"security\" charset=\"UTF-8\""
}
}
],
"type": "security_exception",
"reason": "missing authentication credentials for REST request [/]",
"header": {
"WWW-Authenticate": "Basic realm=\"security\" charset=\"UTF-8\""
}
},
"status": 401
}3.Built-in creating user passwords
Elasticsearch's default built-in username is elastic. But there is no password created for this user name.
While assigning a password, the passwords of all built-in users will be changed.
# Run the following command in the Elasticsearch installation file to automatically update passwords. ./bin/elasticsearch-setup-passwords auto
...
Changed password for user elastic
PASSWORD elastic = dd6mjMiemZlAKfOXkUAm
# Run the following command in the Elasticsearch installation file to manually update the passwords. ./bin/elasticsearch-setup-passwords interactive
This step is required to create a new user after Elasticsearch has activated security. The credentials here can also be defined in the Apinizer API Manager.
4. Adding a user
To add or update a new user, the following request is made. A new user with username apinizer_es_cluster, password apinizer and role superuser has been added to the request. If the user information is updated, "created" will return false.
# For Windows;
curl -X POST -u <USERNAME>:<PASSWORD> "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_security/user/apinizer_es_cluster?pretty" -H "Content-Type:application/json" -d "{\"password\":\"apinizer\", \"roles\":\[\"superuser\"\], \"full_name\":\"Apinizer Elasticsearch Cluster\",\"email\" : \"apinizer@mail.com\"}"
# For Linux;
curl -X POST -u <USERNAME>:<PASSWORD> "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_security/user/apinizer_es_cluster?pretty" -H "Content-Type:application/json" -d '{"password":"apinizer", "roles":["superuser"], "full_name":"Apinizer Elasticsearch Cluster","email" : "apinizer@mail.com"}'
{
"created" : true
}4.1 Password reset
To change the forgotten password
bin/elasticsearch-users passwd <USERNAME>If it does not work and if the password of the users in Elasticsearch has been lost, the cluster can be recovered by creating a new user from the command line below. It can update the existing user name and password information by using the credentials of the user it created.
bin/elasticsearch-users useradd <NEW_USERNAME> -p <NEW_PASSWORD> -r superuser
curl -X POST "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_security/user/<OLD_USERNAME>/_password?pretty" -H 'Content-Type: application/json' -d'
{
"password" : "<OLD_USERNAMES_NEW_PASSWORD>"
}
'In addition;
- When sending a request on an API test tool such as Postman, Authorization: Basic <base64 encoded username:password> information should be added to the header field of the request.
# For example;
Authorization: Basic YXBpbml6ZXJfZXNfY2x1c3RlcjphcGluaXplcg==- To perform user management via Kibana, go to Stack Management > Security > User from the menu, respectively. The following fields should be added to the Kibana setup file /config/kibana.yml.
elasticsearch.username: "apinizer_es_cluster"
elasticsearch.password: "apinizer"Additional commands;
# Find out the authenticated user's information
curl -X GET -u apinizer_es_cluster:apinizer "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_security/_authenticate?pretty"
# User can be activated or deactivated.
curl -X PUT -u apinizer_es_cluster:apinizer "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_xpack/security/user/apinizer_es_cluster/_enable"
curl -X PUT -u apinizer_es_cluster:apinizer "http://<ELASTICSEARCH_IP_ADDRESS>:<PORT>/_xpack/security/user/apinizer_es_cluster/_disable"
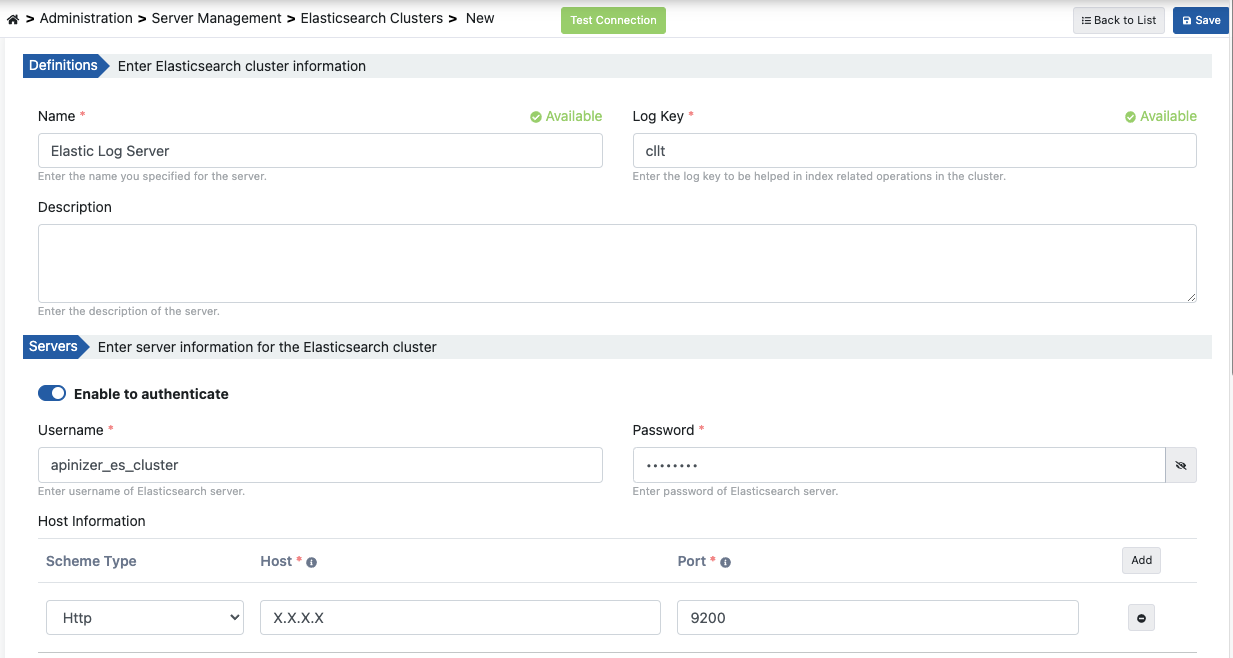
5.Apinizer configuration
The username and password of the identified user are made on the Elasticseach Clusters page in Apinizer Manager Console. Activate the authentication switch button and enter the credentials.