API Manager LDAP Integration
This document explains as an example how to add LDAPs login information to Apinizer and how to log in to Apinizer with your LDAP users.
1) Adding LDAPs Connection Information
Open the Connection Management → LDAP/Active Directory page and add your information.
In the Server Address field, the ldap domain should be added, starting with ldaps://, and then the 636 port.
An example image containing LDAPs connection settings is given below:
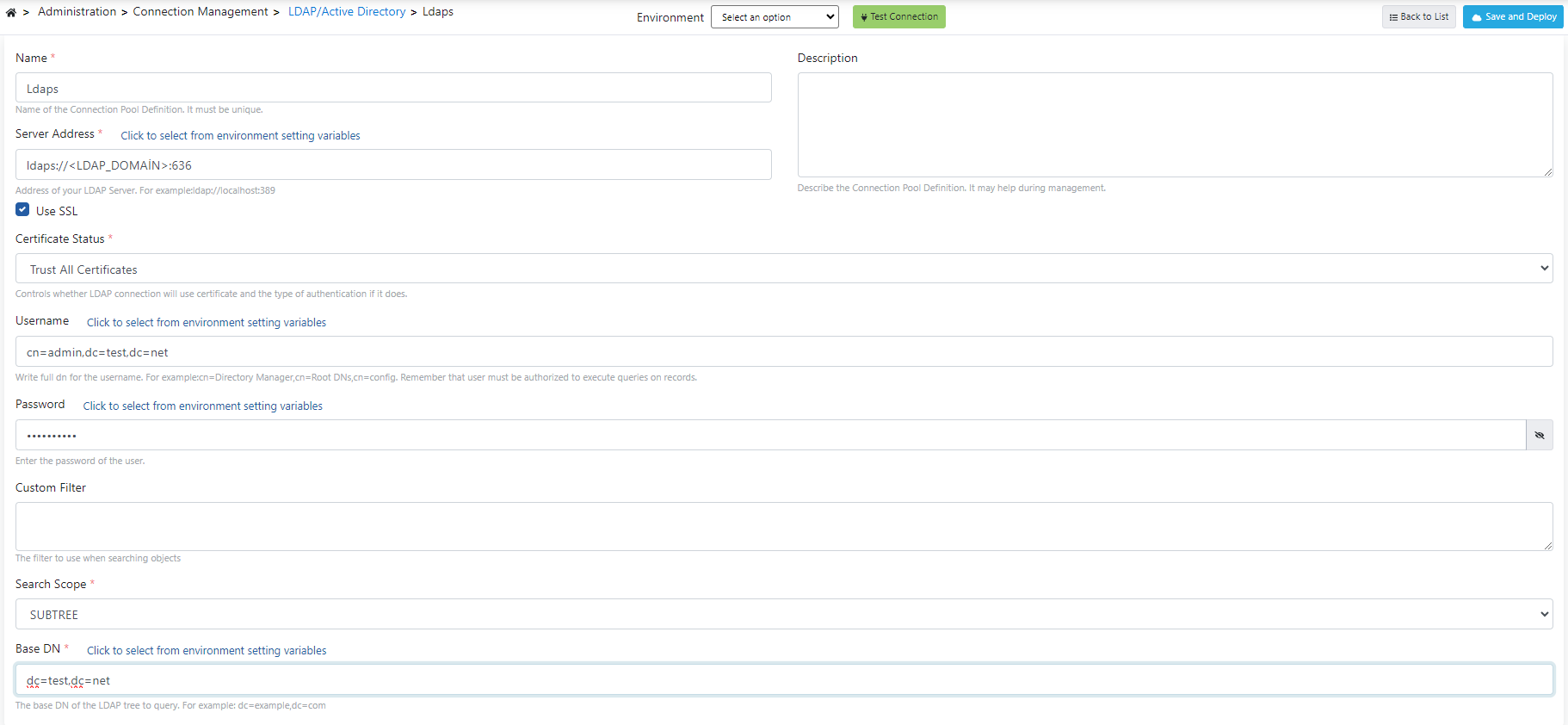
To use SSL, check the Use SSL button.
If Certificate Required is selected in the Certificate Status field, see here to add a certificate.
You can also limit the search by using the Custom Filter field.
For example (&(objectClass=inetOrgPerson)(mail=example@example.com)) this filter will work for users belonging to the "inetOrgPerson" class and whose email address is "example@example.com".
In LDAP, users and groups are often stored under different organizational units.
Therefore, different Base DN addresses can be given for users and groups:
- Base DN for users: ou=Users,dc=example,dc=com
- Base DN for groups: ou=Groups,dc=example,dc=com
After completing the entry of your LDAP information, select one from the Environment field on the same page and click on the Test Connection button. When the process is successful, you will see an output like the example image below.

You can complete the process of adding LDAPs information to your system by clicking the Save and Deploy button.
2) LDAPs Login Settings
This section contains LDAP connection configurations that will enable users to integrate into the identity management systems in their institutions that can be accessed via LDAP connection in order to log into Apinizer.
Open the Administration → System Settings → LDAP Settings page.

Give a name to the connection as in the image above and select the LDAP connection you added in the previous step from the LDAP Connection section. Enter the relevant information by clicking on the edit button marked with red fields.
An example usage for the User Object Class Definition pop-up page is shown in the image below:
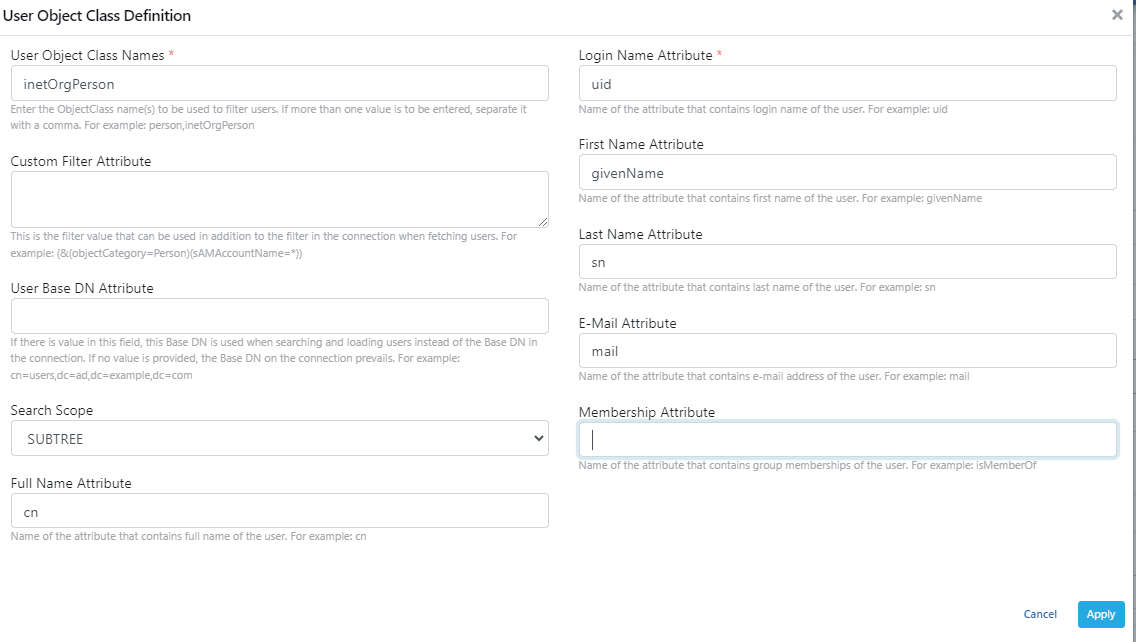
You can view how to fill in the relevant fields for User in the example image above by connecting to your existing LDAP application.
One of the parts that should be taken into consideration is the object class value is written in the User Object Class Name field.
In other fields specified as attribute, only the attribute expression is written.
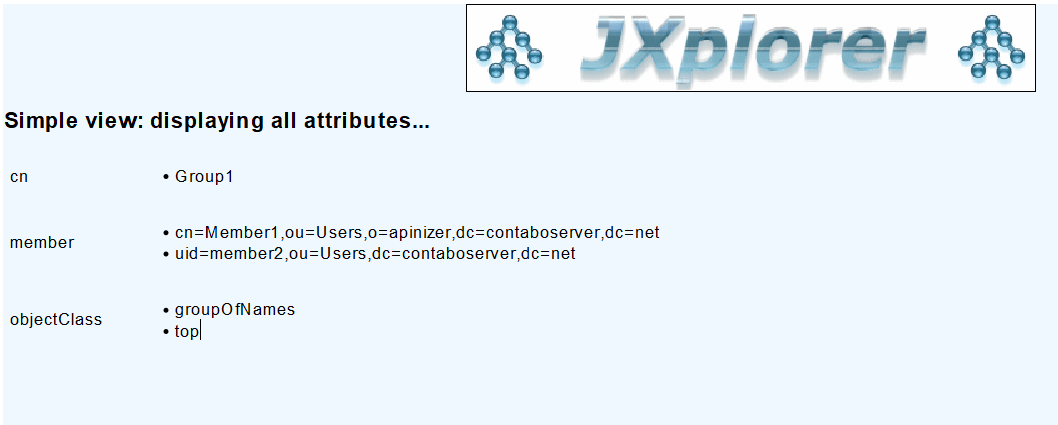
For this example, you can make an LDAP connection using the JXplorer application and see its use in the image below.
According to the example image above, you can see that the Object Class Name for the user is inetOrgPerson. This information may vary depending on your specific LDAP application.
An example usage for the Group Object Class Definition pop-up page is shown in the image below:
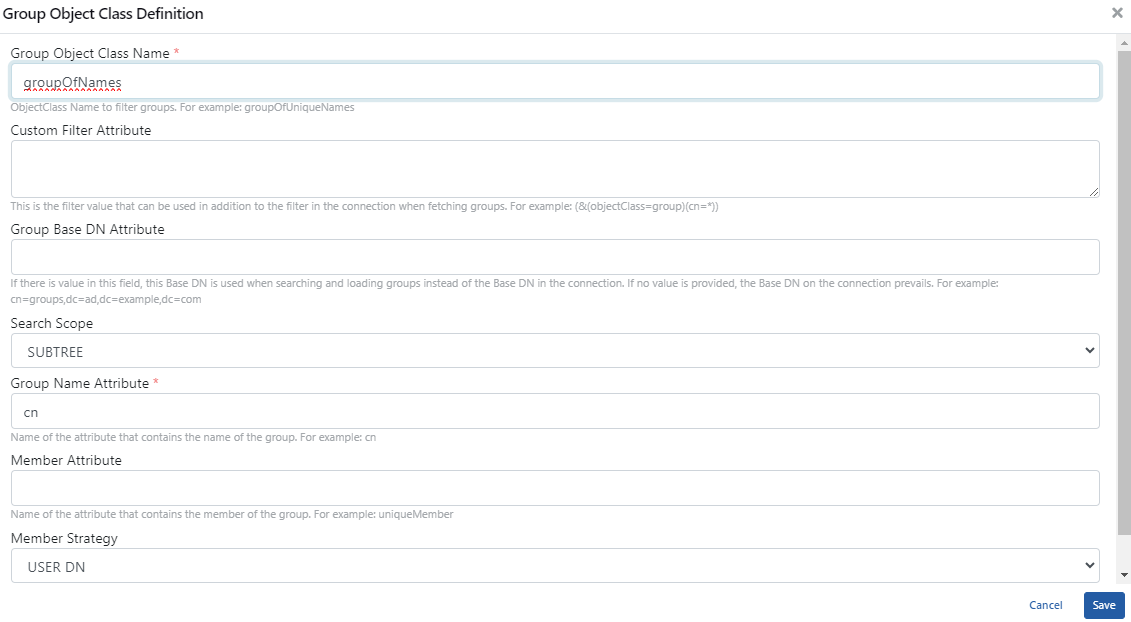
In the example image above, you can view how to fill in the relevant fields for the Group by connecting to your existing LDAP application.
One of the parts that should be taken into consideration is the object class value is written in the Group Object Class Name field.
After entering the information, click on the Test Configuration button in the upper right corner as shown in the image below.
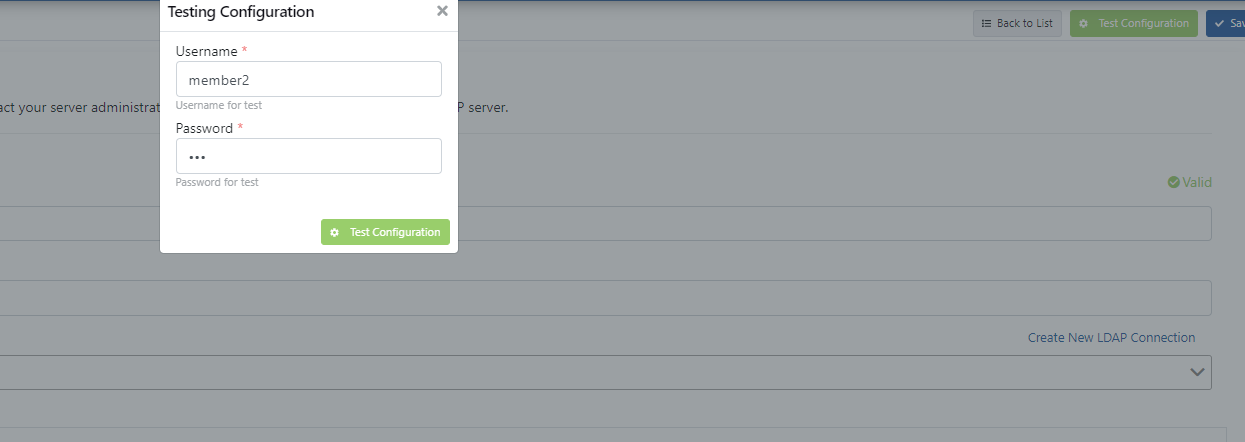
When you log in to the test page with the LDAP user whose uid value is member2 and the password specified in the sample image above as the login information on the page that opens, a Success response will be returned.
Test it with your user information in your LDAP application.
After seeing the successful response, save the information by clicking the Save button.
3) Authorizing LDAP Users or Group Members in the Project
This section describes the authorization process for LDAP users and groups on a project basis.
Select a project from the area where your projects are located, as shown in the image below.
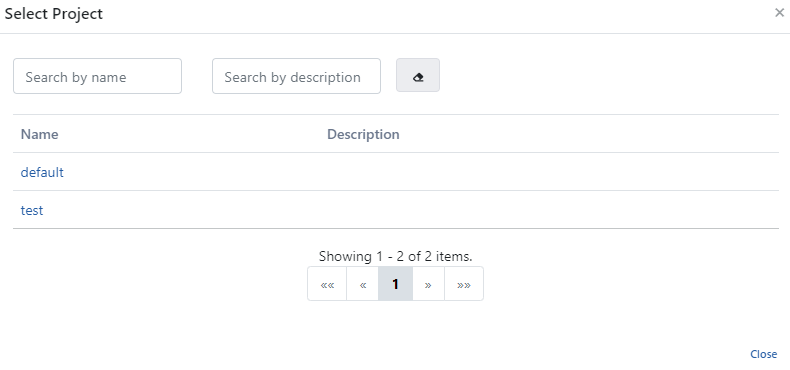
To grant user authority to your project after selecting the project:
Open the Project Settings → Members page.
Type your LDAP user in the LDAP User Members field as shown in the image below and click the Search in LDAP button.
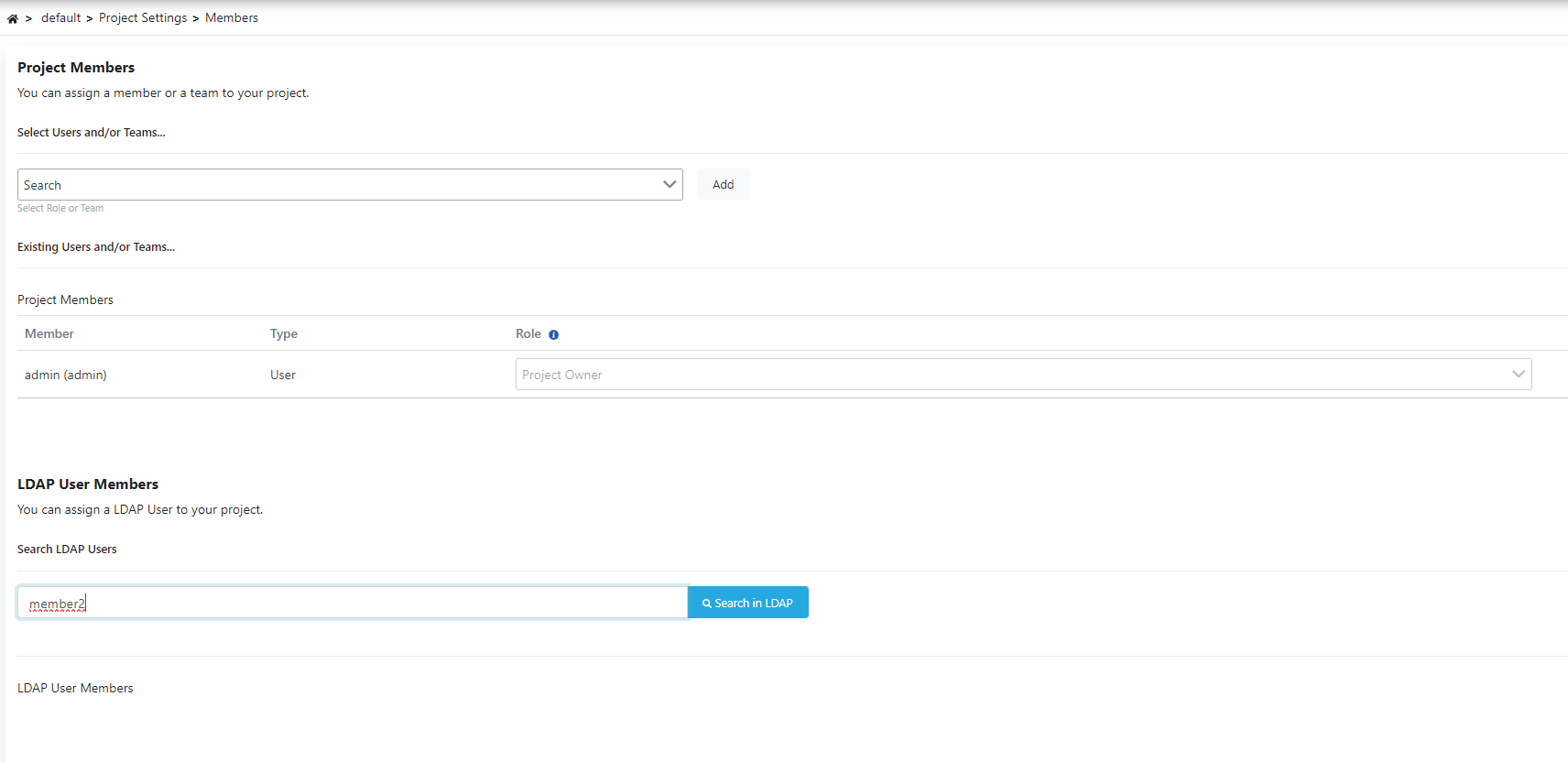
Your LDAP user will appear on the screen as shown in the image below. You can select an authority in the Choose field and add it with Add.

You can add permissions to Group members in the field shown in the image below.

After completing the authorization process, you can complete the saving process by clicking the Save Changes button at the top right of the page.
After this stage, the relevant users or groups will have the permissions you specified in your project.