Authorization
The authorization policy is configured as a part of an authentication policy instead of a separate individual policy. Configuration options of the authorization are same for all authentication policies.
Authorization allows to put one more layer of security after authentication.
Roles owned by the authenticated user are compared with the roles expected by the method/endpoint to be accessed.
- If the roles the client has do not meet the roles expected by the method/endpoint, the message will be interrupted and an error will be returned.
- If the roles of the client meet the roles expected by the method/endpoint, the message flow continues.
Authorization Settings
Authorization settings are made in the Authorization Configuration section of the authentication policy.
First of all, in this section, the authorization settings must be set to ENABLED. When the authorization settings are activated;
- If the policy is added to an API Proxy, role-based access control can be defined both on the API Proxy itself and its methods/endpoints.
- If the policy is added to an API Proxy Group, role-based access control can only be defined for the API Proxy Group.
The picture below shows the policy settings:
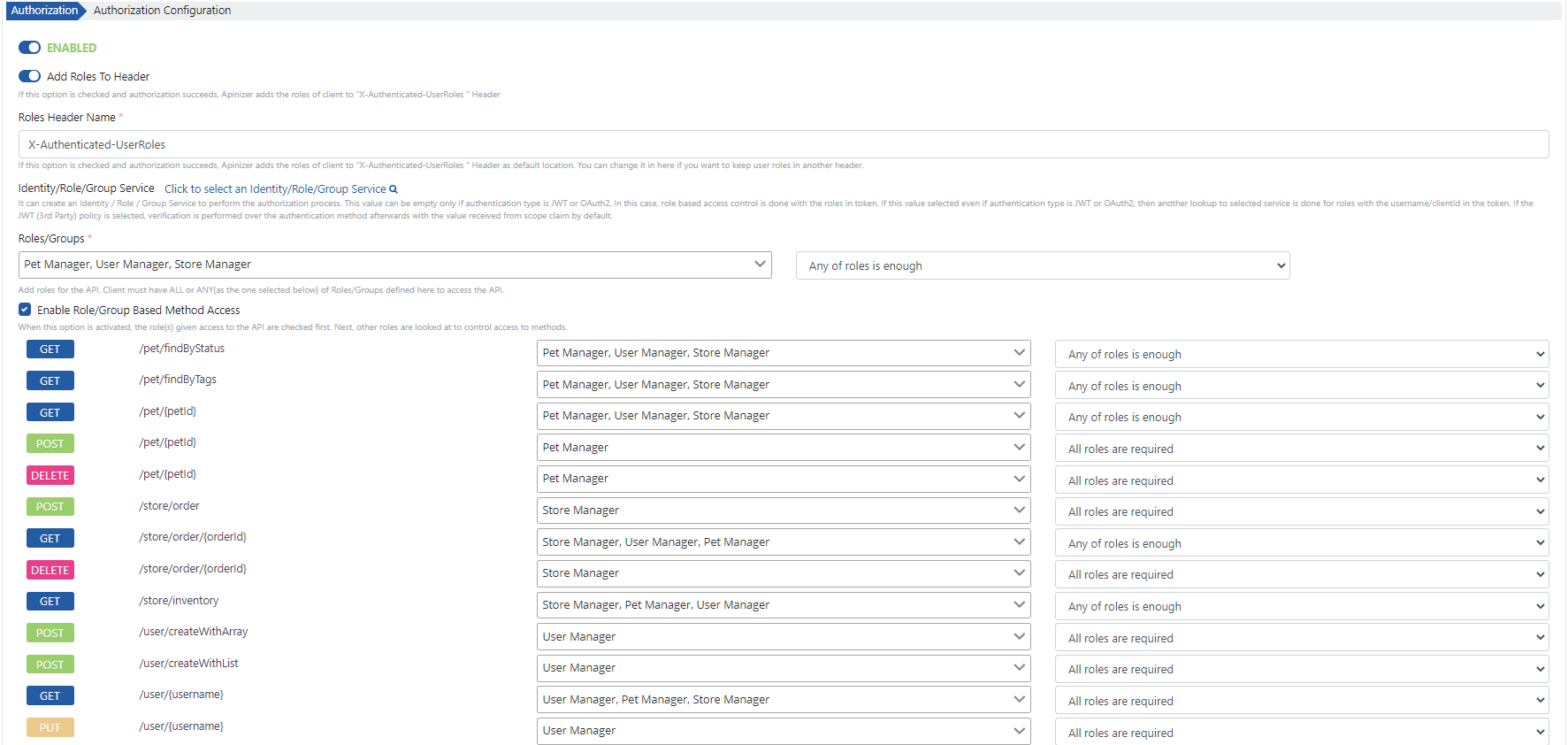
The the Authorization Policy fields are shown in the table below.
Field | Description |
|---|---|
Add Roles to Header | If the option is checked, the roles of the authorized user are sent to the Backend API in a header when the authentication is successful. The default name of the header is X-Authenticated-UserRoles. |
Identity/Role/Group Service | This field must be filled if the roles are to be obtained from another Identity/Role/Group Service instead of the one selected for the authentication policy. If an Identity/Role/Group Service is selected for this field, the roles are queried with the authenticated username and password via this Identity/Role/Group Service. |
Roles/Groups | The roles that the client must have to access the API Proxy are selected. At least one role must be selected. |
Requirement | Select whether the client should have all or at least one of the specified roles to access the API Proxy. It can take one of the following values:
|
Enable Role/Group Based Method Access | When enabled, the roles required for each method/endpoint that API Proxy has can be defined separately. When roles are defined for methods/endpoints, roles are checked for both the API Proxy and the methods/endpoints. For example;
In this case, a client with Role-1 can access /method2, but can not access /method1. This field is not available if the authentication policy is being configured for an API Proxy Group. |
You can visit the Credential Roles and Identity Providers pages for detailed information about managing roles of clients.