Database
The Identity Provider specifies the pool of users to send requests to the API. These default Identity Providers are used when creating the Authentication Policy.
Accessible and manageable by roles with "Manage Authentication Services" authority, such as "Project Owner".
1) Authentication Connection with Database
The image containing the connection settings for authentication with the database is given below:
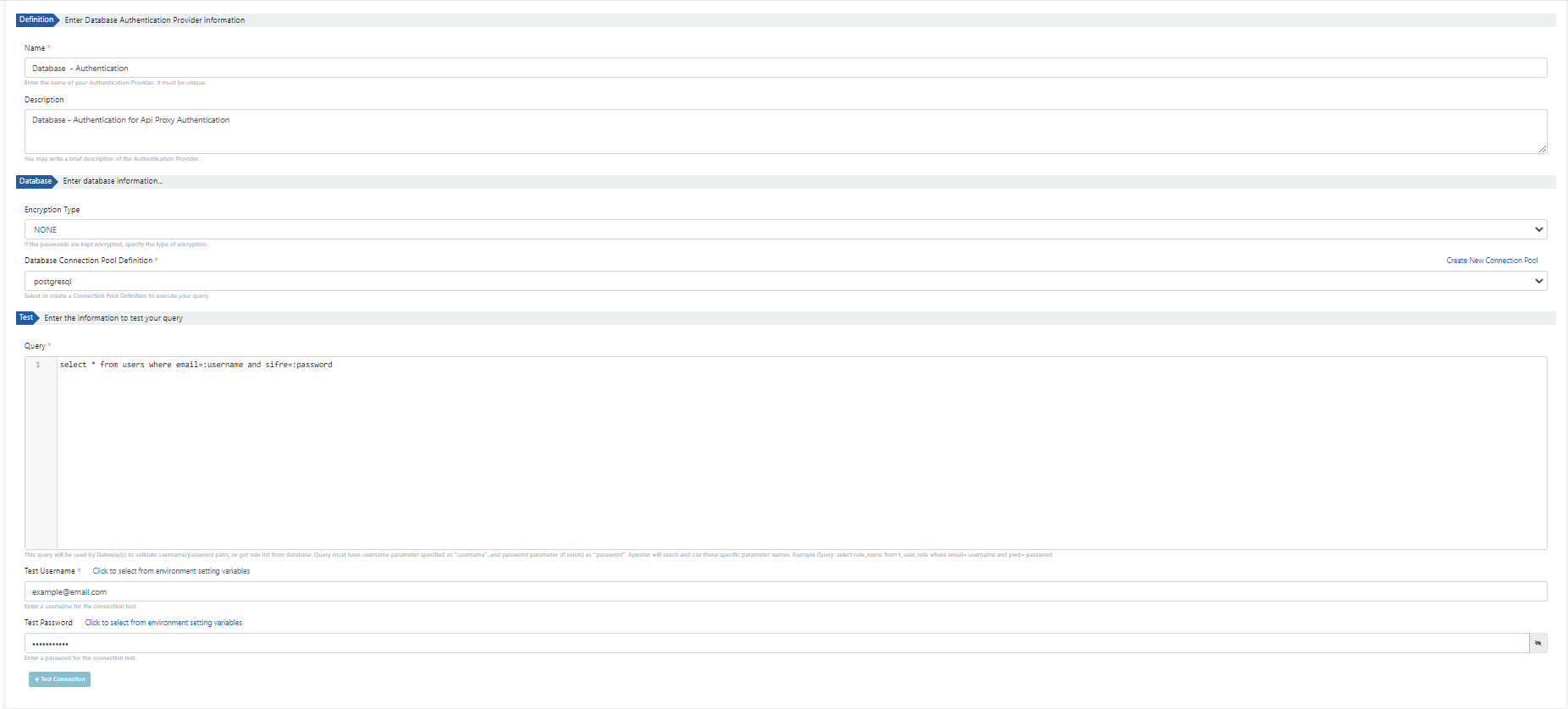
The fields used in the connection settings for authentication with the database are shown in the table below.
Field | Description |
|---|---|
Name | Created Database Identity Provider name information. |
Description | A description can be written to facilitate the management of the created Identity Provider. |
Encryption Type | If the password information is kept encrypted in the table to be used in the database connection, the encryption type for the password kept in the table should be selected.
|
Encoding Type | The encoding to be used for passwords can be specified. |
Salt Pre | Before the password is encrypted, a sequence of letters can be defined to be prefixed with the password. |
Salt Post | Before the password is encrypted, a string of letters to be added to the end of the password can be defined. |
Database Connection Pool Definition | The pool from which the database connection will be taken is selected or created. |
Query | Used to retrieve username/password pairs or role list from a query database. In the query, the username parameter should be defined as ":username" and the password parameter, if any, should be defined as ":password". Apinizer works with these special parameter names. Example query: select role_name from t_user_role where email=:username and pwd=:password |
Test Username | While running the query for testing, the value to be written is entered instead of the username parameter. This parameter can also be selected from environment variables. |
Test Password | While running the query for testing, the value to be written is entered instead of the password parameter. This parameter can also be selected from environment variables. |
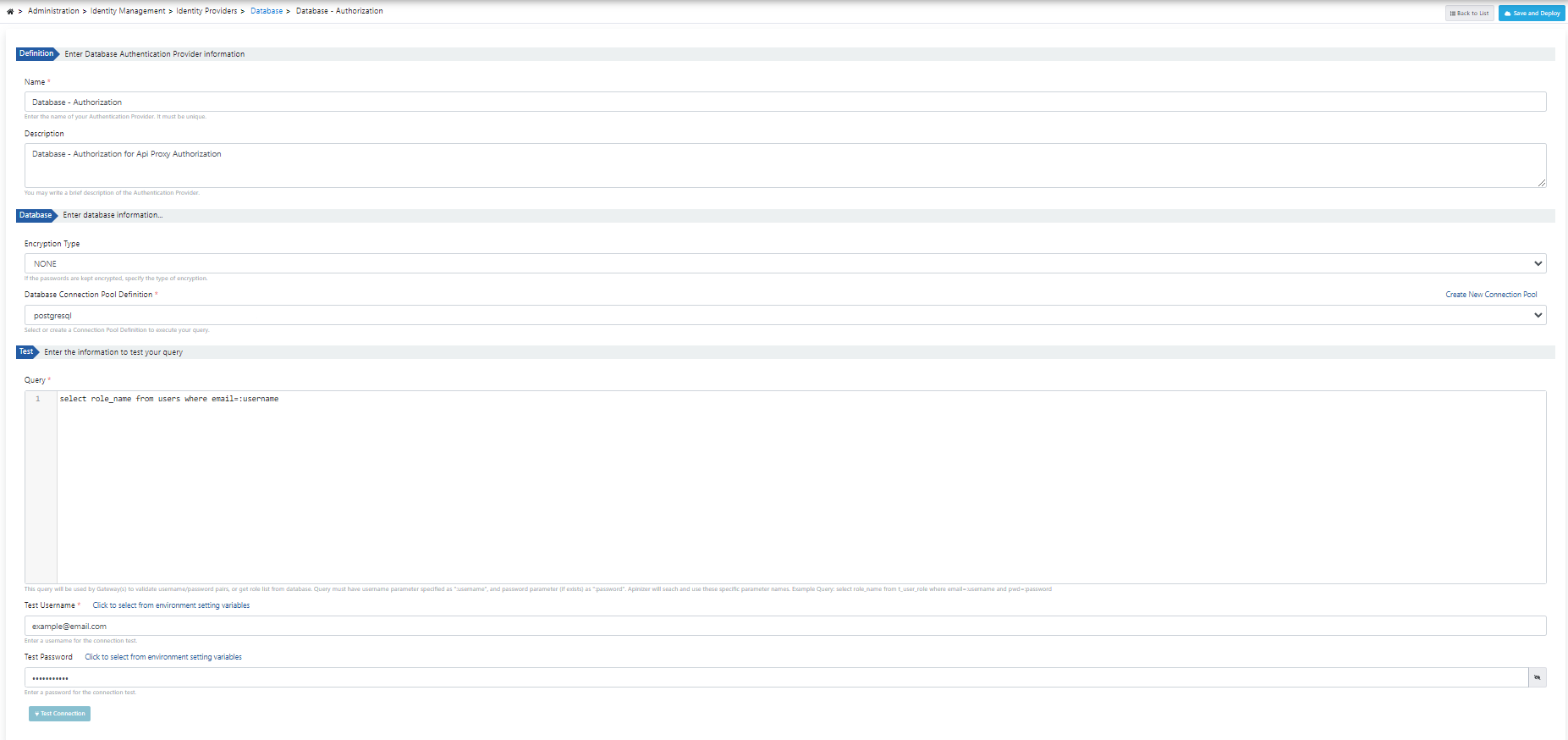
2) Identity Authorization Connection with Database
When performing identity authorization, the role field of the relevant user is retrieved in the database query. This role field is then mapped to the ROLES/GROUPS field in Authorization in the proxy policy.
The visual containing the connection settings for identity authorization with the database is given below: