JOSE Validation
The JOSE Framework is a set of specifications aimed at securing digital content using JSON data structures.
The JOSE Framework includes features such as JWS, JWE, JWT, JWK, and JWA.
Apinizer supports the JOSE Framework specifications, making it easier to use.
The JOSE Validation Policy is used for verifying signed and/or encrypted JSON data sent by the client and performing signature verification and/or decryption operations.
The picture below shows the JOSE Validation:
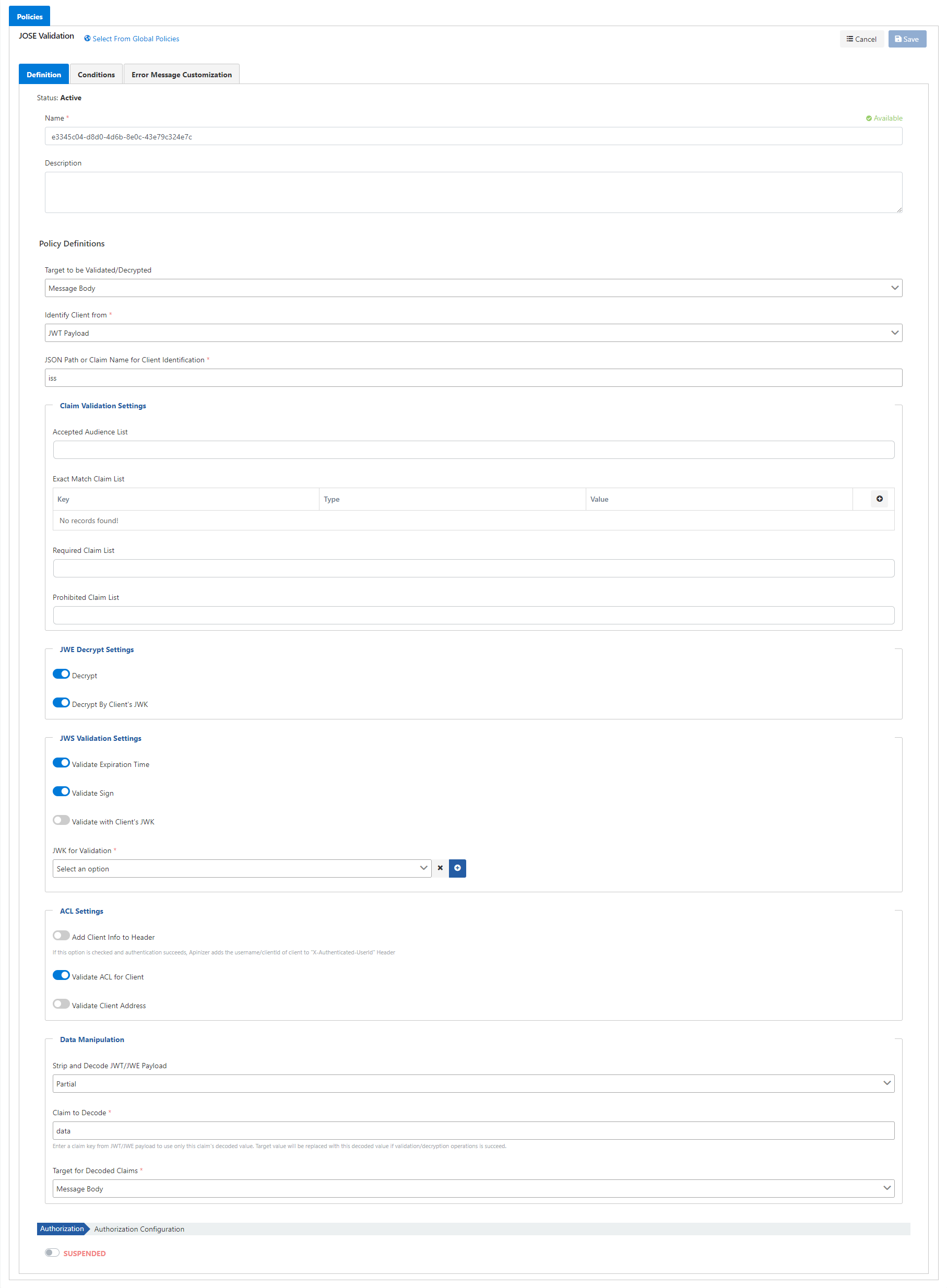
The fields used for JOSE Validation configuration are shown in the table below.
Field | Description |
|---|---|
Name | The name can be written to facilitate the use and management of the policy. You will need this name during the management and selection of policies. |
Description | A description can be given to facilitate the usage and management of the policy. |
Target to be Validated/Decrypted | Signature/encryption may be applied to the entire message body, or part of the message's header, parameter, or body. This field is used to indicate where in the message the signature will be verified and/or the encrypted data will be decrypted. |
Target Variable | The variable used to indicate where the specific portion of the message is located, is the target. |
Identity Client from | Indicates where in the message the client information will be retrieved from the data. The client info can be required for selecting JWKs. Possible values include being specified by the header or body of the signed/encrypted JWT or can be selected with a variable. In most cases, although this data is in the payload, if the JWE is used, the credential is expected to be taken from the header, since information cannot be retrieved without decrypting payload. |
| JSON Path or Claim Name for Client Identification | It specifies from which claim or JSONPath value the client information will be taken in the header or body. If the expression written in this field begins with $, the expression is treated as JSONPath, otherwise it is treated as claim name. |
Accepted Audience List | It is the Audience list that can be included in the incoming JWT/JWE data. If there is any audience information in the incoming data that is outside this list, an error is returned. |
| Exact Match Claim List | It is the list of claims that can be included in the incoming JWT/JWE data. If there is any claim information in the incoming data that is outside this list, an error is returned. |
| Required Claim List | It is the list of claims that must be present in the incoming JWT/JWE data. There may be additional claims in the incoming data outside this list, but these specific claims are required to be present, and if any of them is missing, an error is returned. |
| Prohibited Claim List | It is the list of claims that must not be present in the incoming JWT/JWE data. There may be other claims in the incoming data outside this list, but if any of these specific claims are present, an error is returned. |
| Decrypt | If the incoming data is encrypted (JWE) and it needs to be decrypted, this option is selected. For this option to appear, "Verify Signature" option must be selected. |
| Decrypt By Client's JWK | If the encrypted fields in the incoming JWE data need to be decrypted based on the user identity, this option is selected. In this case, it is checked whether the "iss" (issuer) information in the data is among the users in the Apinizer User Identity Pool. If a user is found whose username/API key matches the issuer information, decryption is performed using the Encryption JWK owned by that user. Also, when the data is sent as encrypted, the "iss" (issuer) information should also be sent in the header. |
| JWK for Decryption | If the decryption of the encrypted fields in the incoming JWE data needs to be performed based on a fixed JWK rather than the "iss" (issuer) information in the data, this option is selected and the decryption process is performed with the selected JWK. |
| Validate Expiration Time | The incomingJWT/JWE data contains information about when it was created in the "iat" claim. The "exp" claim contains information about how long after "iat" it will expire. If the "Validate Expiration Time" option is selected, these two values are added together and compared to the time the request was received, and it is expected to be less than or equal to it. If it is invalid, an error is returned. |
| Validate Sign | It is marked to verify whether the signature in the incoming JWT/JWE data is valid or not. |
| Validate with Client's JWK | If desired, this option is selected to process the signature contained in the JWT/JWE data depending on the user identity. The "iss" (issuer) information in the data is checked to see if it belongs to the users in the Apinizer User Identity Pool. If a user is found whose username/API key matches the issuer information, verification is done with the JWK signature owned by that user. |
| JWK for Validation | If the signature in the incoming JWT/JWE data is to be verified based on a fixed JWK instead of the "iss" (issuer) information in the data, this option is selected and verification is performed with the JWK selected here. |
| Add Client Info to Header | If this option is checked and authentication succeeds, Apinizer adds the username/clientId of client to "X-Authenticated-UserId" Header. |
| Validate ACL for Client | If this option is checked, it allows checking whether the client has access to this API Proxy. |
| Validate Client Address | If this option is checked, this option allows the IP address of the client to be checked. |
Strip and Decode JWT/JWE Payload | This field is used to decode/decrypt the data for which the validation process is performed. If "All" is selected, all data is decoded and if "Partial" is selected, only the specified part is decoded. If "None" is selected, decoding is not performed. |
| Claim to Decode | When the "Strip and Decode JWT/JWE Payload" field value is selected "Partial", it specifies which of the claims in the payload of the JWT/JWE are to be decoded. |
| Target for Decoded Claims | Indicates where in the message the decoded value will be placed after successful validation/decryption. |
| Target Variable for Decoded Claims | Variable used to indicate where the target is in the message if it is a particular part of the message. |
| Authorization Configuration | This option is activated to configure the access control according to the roles of the users. Please visit the Authorization page for more information. |
You can visit the Policies page for the details of the Conditions and Error Message Customization panels.