Manual Management of Gateway Environments
Environment is a runtime execution context for API Proxies in an enterprise.
In this section, the process of defining created Kubernetes definitions in the Apinizer platform will be explained.
When the Manage Kubernetes Namespace and Resources with Apinizer option is marked as Disabled in the System General Settings screen, it is displayed.
The picture below shows the general definition information of the environment:
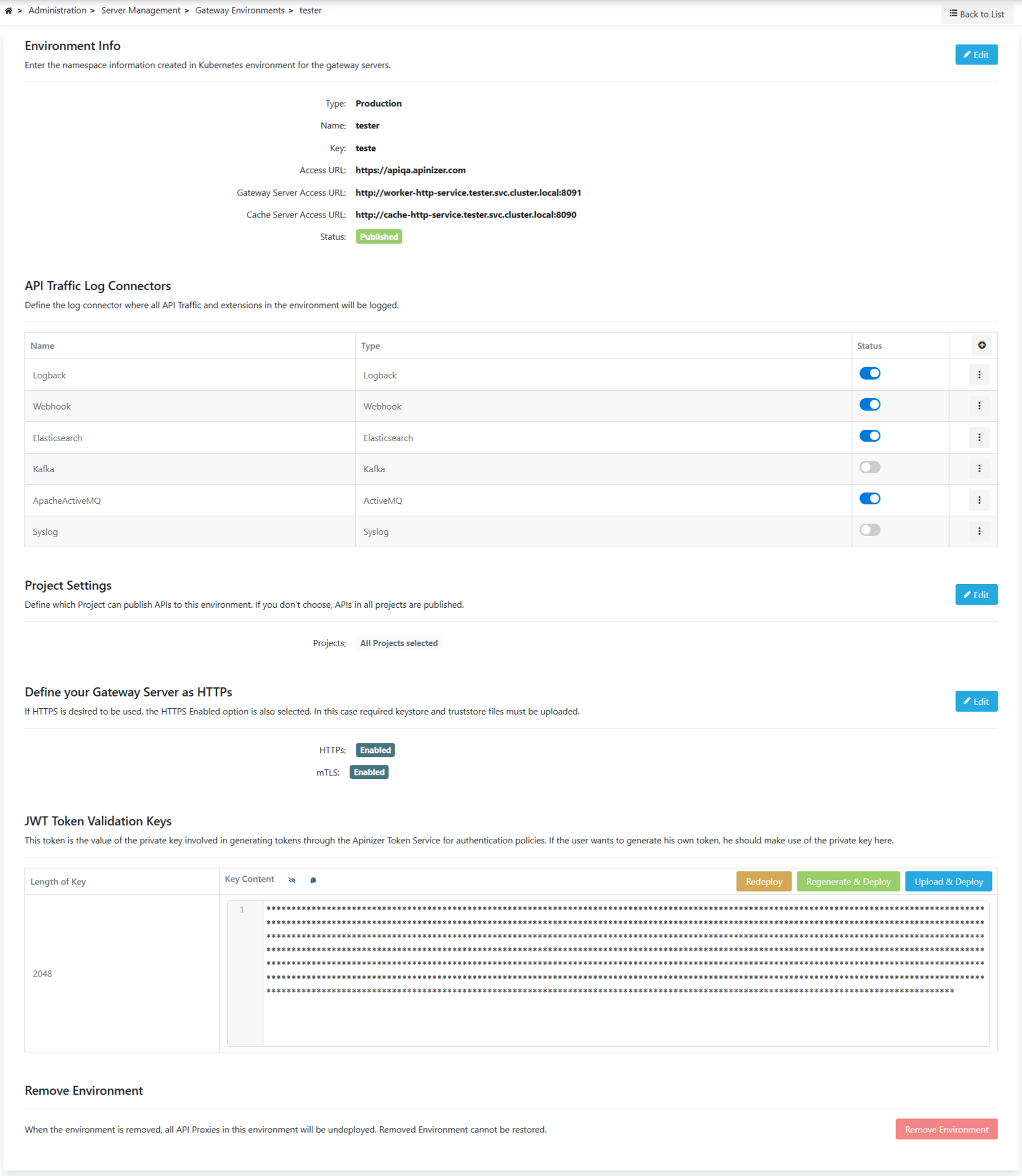
Fields that contains general information about the environment are shown in the table below.
Field | Description |
|---|---|
Type | Test or Production can be selected as the type so that the test is not deducted from the license. |
Name | Name of environment. |
Key | An environment-specific abbreviated key used for the created environment. |
It is the external access address of API Proxies running in the environment. It has been explained in detail in the previous section. | |
| Description | It can be used for ease of management and important notes. |
| Gateway Server Access URL | The service access address of the nodeport or ingress type required to upload the configurations made in the Apinizer Management console to the Gateway Pods is entered here. |
| Cache Server Access URL | The nodeport or ingress type service access address required for the configurations made in the Apinizer Management console to be uploaded to the Cache Pods or for the Gateway Pods to access the cache pods is entered here. |
| API Proxy Traffic Log Connectors | Log connectors where all API Proxy Traffic and extensions in the environment will be logged are defined here. Please refer to this page for more information about adding a connector to environment. |
Projects | You can choose the projects where the environment can be used, or leave it blank so that it can be used in all projects. If one or more projects are selected, they must also be added to be used in newly created projects. It comes with no selection by default. If a project is selected, it means that only API Proxies included in that project can be deployed to this environment. |
Define your Gateway Server as HTTPs | If HTTPS is to be used, the HTTPS Enabled option is also selected. In this case, the necessary files for encryption must be uploaded. |
Keystore | When HTTPS protocol is selected, keystore files can be loaded in JKS or PFX format. |
Truststore | When HTTPS protocol is selected, truststore files can be loaded in JKS or PFX format. |
Keystore Password | Enter the password of the keystore file. |
Truststore Password | Enter the password of the truststore file. |
| mTLS Enabled | Since the mTLS setting works over the HTTPS protocol, it can only be selected when the HTTPS setting is enabled and allows the server to request authentication from the client, but does not enforce this as a strict requirement to establish the connection. If mTLS authorization is required, the mTLS policy should be used. |