Token Service
In addition to providing authentication and authorization, Apinizer can also work as an identity provider service.
Clients can generate tokens using Apinizer's token generator service with their credentials. By sending the generated tokens in the message, they can provide authentication and authorization through these tokens instead of their own credentials.
You can generate OAuth2 or JWT Tokens with Apinizer, and you can perform security checks on your API Proxies with these tokens.
Following image shows the message flow between a client and Apinizer simply.
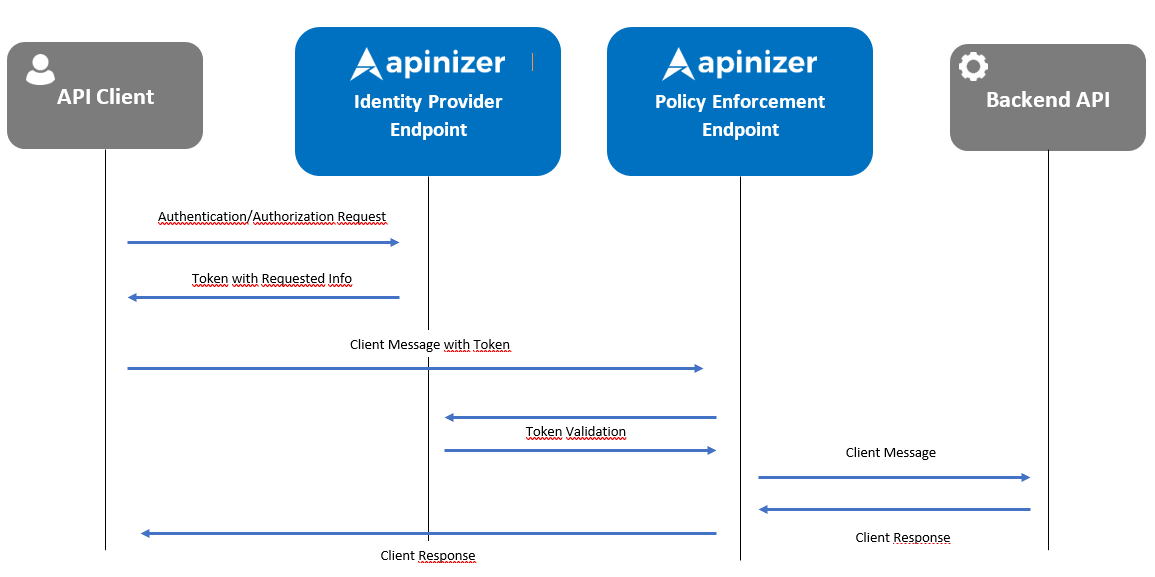
Apinizer stores the tokens generated for OAuth2 authentication in its database and caches them separately for performance.
In JWT authentication, Apinizer does not need any store the tokens for authentication. Instead, it stores the RSA key of the Worker in each environment. The token is verified by checking the RSA key from which the JWT Token is generated. This check only verifies that the token was generated by Apinizer and the data was not corrupted or modified. In addition to this check, the policy also checks the claims in the token according to the API Proxy information from which the message came.
With a new approach, Apinizer prefers to generate JWT tokens by calling the API rather than giving the key value to the client.
Although the key value is often shared for the generation of the JWT token value, Apinizer prefers to generate JWT tokens by calling the API with a new approach at this point. Thus, instead of key control and sharing, it makes token generation and key management easy for clients. In this approach, standard parameters requested in OAuth2 are requested in the JWT token generation API and processed similarly.
Receiving Tokens with JWT and Receiving Tokens with Oauth2 to view the description of your panel Methods of Obtaining Tokens you can visit the page.
If “Manage From This Policy” is selected when receiving tokens withJWT or OAuth2, the CORS and XFF settings you configured in the “Settings” tab of the API Proxy will be valid.
However, if this option is not selected, if it is managed through “Credentials”, the CORS and XFF settings you added to the Worker in “Gateway Environments” will be valid. See.