GetCapabilities Routing Issue in Geographic Information Systems Services
Problem
Addresses in the WSDL returned with GetCapabilities in Geographic Information Systems services need to be moved to Apinizer.Solution
With a Business Rule or Script policy to be added to section 2, if the value ‘GetCapabilities’ comes in the ‘request’ key as a query param in the url, the address here should be changed with string replace to route to the relevant proxy in Apinizer.Client IP Address Appearing as 10.244.x.x
Problem
Client IP address appears as 10.244.x.x in Kubernetes environment.Reason/Why
In Kubernetes NodePort structure, if X-Forwarded-For value does not come from client, it routes the pod’s IP address to the application behind by default. As a solution, we can solve it by making the externalTrafficPolicy value Local, but this time since NodePort does not route incoming requests to other servers in the Cluster, access problems occur. It is necessary to know the relevant Node and go to it.Solution
Since Apinizer Workers will be placed behind a structure like Nginx or F5, xff information needs to be added to the header in the relevant loadbalancer’s configuration file as follows.
Headers Containing Underscores Not Appearing in API Traffic Logs
Problem
Headers containing underscores not appearing/being transferred in API Traffic Logs.Reason/Why
Nginx is widely used as a web server and reverse proxy server. However, in Nginx’s default configuration, HTTP headers containing underscore (_) characters in their names are not processed and passed. This is because underscores are not standard in HTTP RFC.
Solution
To solve this problem, you should set theunderscores_in_headers directive to on in the Nginx configuration file. This ensures Nginx processes headers containing underscores correctly.
Turkish Characters Being Transferred Corrupted
Problem
Turkish characters are being transferred corrupted.Reason/Why
Character set information should be set to Content-Type header during data transmission from client side.Solution
Client should send by setting the value part to application/xml; charset=UTF-8 in the Content-Type: application/xml pair it sends as an example.
PKIX Path Building Failed Error
Problem
PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested targetSolution
Add Certificate to Apinizer
The public certificate of the relevant address should be added to Apinizer from the Certificate Management page.
Login Issue in Apinizer 2024.05.4+ Version
Problem
I updated Apinizer to version 2024.05.4 or later but cannot login to the interface.Reason/Why
Therefore, organizations connecting to the interface using “Kubernetes Ingress Controller” need to make settings to send client ip information with X-Forwarded-For header.Solution
Configure ConfigMap Settings
The “use-forwarded-headers” key should be added with “true” value to the data section in Config Maps definition:
One of the following headers must come from the load balancer side:
- X-Forwarded-For
- Proxy-Client-IP
- WL-Proxy-Client-IP
- HTTP_X_FORWARDED_FOR
- HTTP_X_FORWARDED
- HTTP_X_CLUSTER_CLIENT_IP
- HTTP_CLIENT_IP
- HTTP_FORWARDED_FOR
- HTTP_FORWARDED
- HTTP_VIA
- REMOTE_ADDR
The Gateway checks the above headers in order and uses the first valid IP address found.
Header Keys Containing Underscores Not Being Transferred
Problem
Header keys containing_ (underscore) character are not being transferred to logs and backend when coming to Apinizer Gateway.
Reason/Why
By default, Nginx and Ingress-Nginx Controller do not accept headers containing_ (underscore) character. Therefore, the header is blocked before reaching the gateway.
Solution
Ingress Nginx ConfigMap Settings
The “enable-underscores-in-headers” key should be added with “true” value to the data section in Config Maps definition:
Certificate Issue in WS-S/WS-STS Token Retrieval in SOAP Services
Problem
WS-S or WS-STS policies used in SOAP services cannot retrieve tokens due to “PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target” error.Reason/Why
Since the certificate loaded to Apinizer cannot be seen in SOAP service call, token retrieval of this service needs to be done through reverse proxy.Solution
A reverse proxy that routes with the relevant token retrieval address is created and the token retrieval address of the wss/wssts policy in the service using tokens is given as this service. In rare cases, it may be necessary to change the address in the xml message with script through reverse proxy.ERR_13611_VALUE_MISSING_ON_RDN Error During LDAP Login Setting
Problem
ERR_13611_VALUE_MISSING_ON_RDN error during LDAP login setting.Reason/Why
This error usually indicates a missing value.Solution
DNS Resolution Performance Issue
Problem
Some service addresses not being resolved instantly in systems with intensive environment usage or high number of rate limit definitions.Reason/Why
This situation is caused by insufficient DNS resolution performance.Solution
Increase CoreDNS Resource Limits
CPU and RAM resources should be increased to enable processing more queries simultaneously.
SSL Certificate Issue in MSSQL Connections
Problem
I updated Apinizer to version 2025.07.4 or later but I’m getting an error in my Sql Server (MSSQL) connections: Failed to initialize pool: “encrypt” property is set to “true” and “trustServerCertificate” property is set to “false” but the driver could not establish a secure connection to SQL Server by using Secure Sockets Layer (SSL) encryption: Error: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target.Reason/Why
With this library, tls 1.2 and above are mandatory in jdbc connections. Encrypt default value is true and this requires a connection with a correct certificate. This error is encountered in databases using self-signed, incorrectly configured certificates, or not using certificates.Solution
Note: In your internal systems and development or test environments, this error can be bypassed by adding one of the following parameters to the jdbc url:
;encrypt=false(not recommended);trustServerCertificate=true(should be added carefully, possible consequences in terms of security should be considered)
Service Error During Uploads Larger Than 100 MB
Problem
The service returns errors and requests fail when uploading large files.Reason/Why
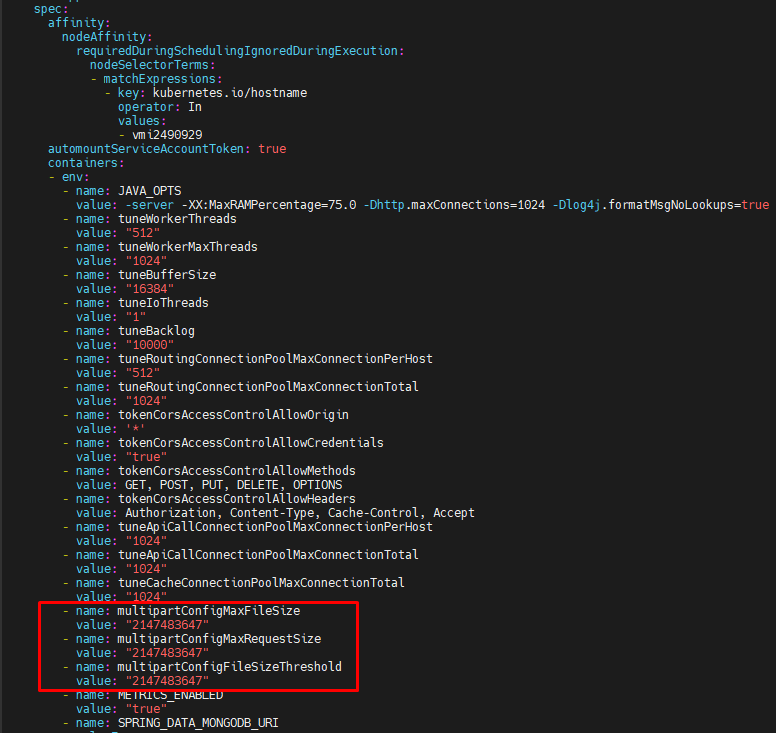
The default value of the file upload–related parameters is 100 MB, which is insufficient for the current large file upload requirements.Solution
To increase this limit, the relevant parameters must be updated with appropriate values in bytes on the deployment named worker in the Kubernetes environment. multipartConfigMaxFileSizemultipartConfigMaxRequestSize
multipartConfigFileSizeThreshold
The values must be defined in bytes and added under the spec → containers → env section of the worker deployment, as shown in the image below.