Credentials
Access control setting with Identity Management in Apinizer can be configured in 2 different ways:
- Via identity information: In this method, the details of the identity information are accessed. In the details of the credential, access is given to API Proxies and their settings are displayed, and the action is taken.
- Via API Proxies; In this method, the API Proxy is detailed. The action is taken by displaying the credentials that have been granted access to API Proxy. Click to apply the condition in this option.
This page fulfills the condition in the first option.
The credentials of the clients that will access the API Proxy defined in Apinizer are created and managed from this page.
The credential access permission alone is not sufficient to access the API proxy. In order for the settings in the credential and access permission to take effect, one of the authentication policies must be added on the API Proxy and the Security Manager option must be selected as the authentication method in this policy.
Credential List
When the Credentials page is first opened, the available credentials are listed as in the image below:
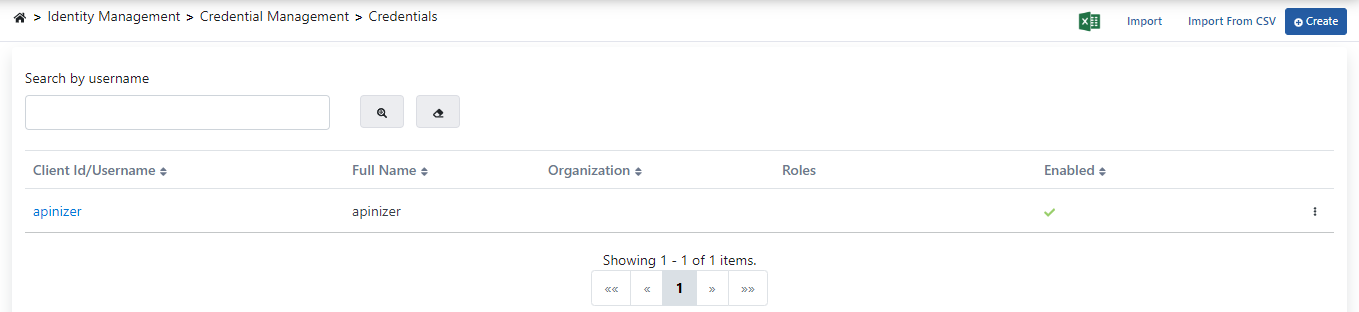
The fields used for screen components are shown in the table below.
| Field | Description |
|---|---|
Advanced Search | It is used to perform detailed searches on credential. |
Access Control List | It is the table where the credentials are listed and sorted. |
Create | Used to create new "Credential". |
Import From CSV | It is used to collectively register credential. |
Import | It is used to import the credential with .json or .zip extension. |
Export Credential List as an Excel File | It is used to download the list of credentials as an excel file. |
Export | All data of the credential can be exported for reuse in another project. In this process, only general information is exported. Advanced settings, API Proxy ACL, API Proxy Group ACL, JWK settings and mTLS settings are not exported as they are project-based information. |
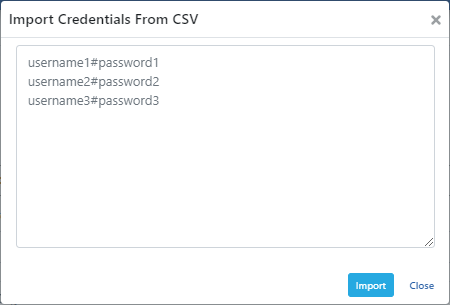
Bulk Credential Transfer with CSV
Import from CSV feature can be used to transfer existing credentials to Apinizer.
If this feature is desired to be used;
- Current user information should be written in such a way that each record comes on one line.
- The user name and password information must be included in the registration together and the password information must be open.
- The # sign must be put as a separator between the username and password information.
- Each line must be separated with the Enter key.
The data prepared in this way is entered on the screen that opens and the import button is pressed.
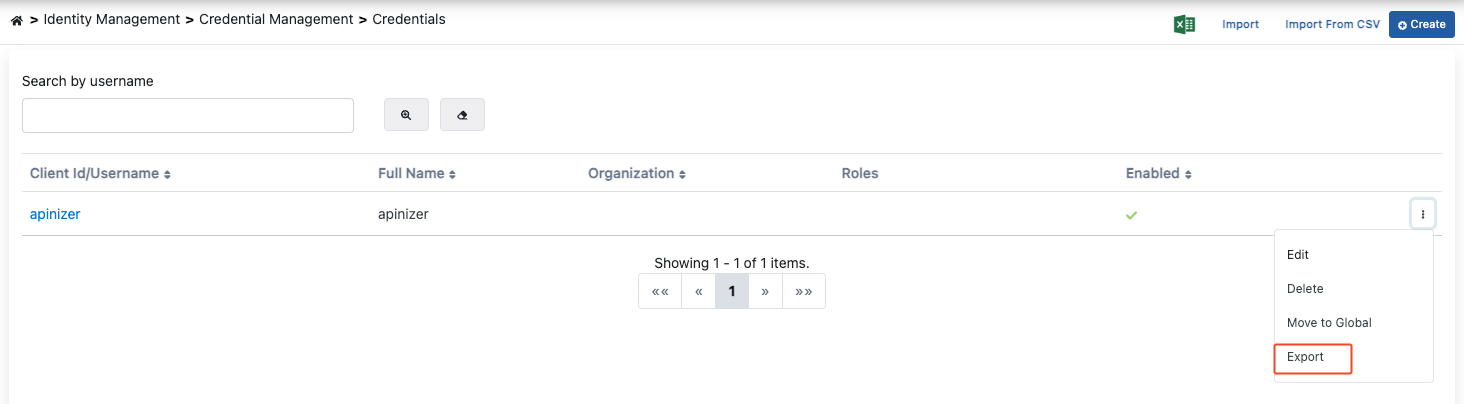
Export Credential
To export the Credential, select Export from the menu at the end of the line.
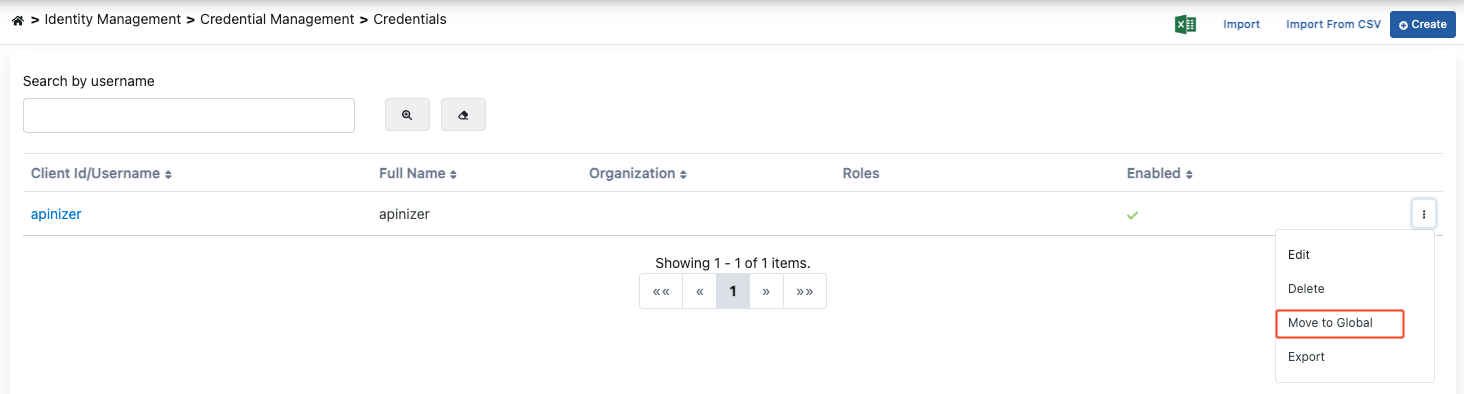
Move Credential to Global
Credential information is moved to the Admin page with the "Move to Global" option, removing it from this list. It becomes usable in all projects, and its management is handed over to the Admin user.
To move Credentia to global, select Move to Global from the menu at the end of the row.
Credential Creation
When the Create button is pressed to add credentials, the following image is displayed:
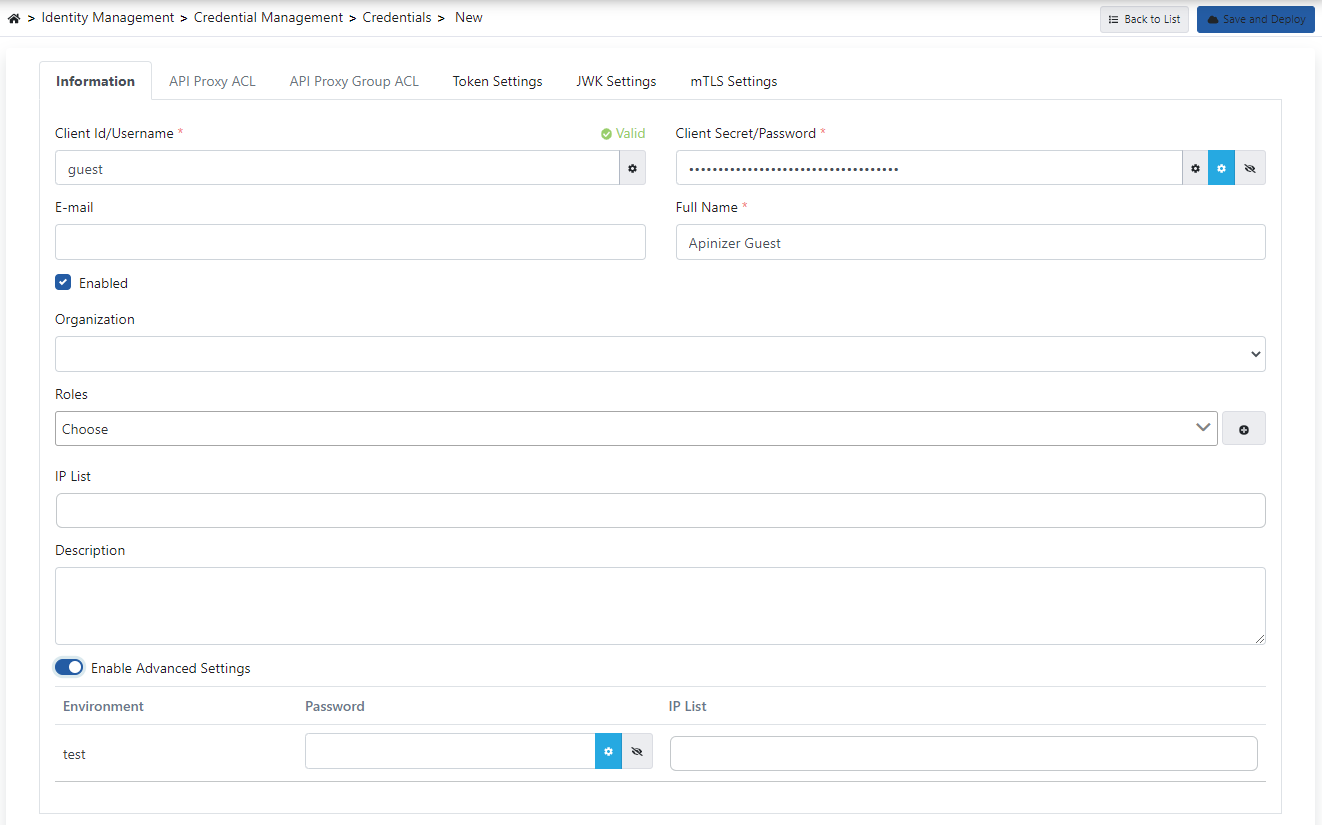
As seen in this image, we can do two types of operations on identity information:
- Entering, creating or updating the details of the credential
- Creating or updating the credential's access control list
The descriptions of the credential fields are as follows:
| Field | Description |
|---|---|
Username | It is the "username" information that will represent the credential, this value is used to access the user ID for authorization. It has to be singular and unique in the whole system. |
Password | It is the password information of the credential. If desired, it can be created automatically with the button next to it. |
The owner of the credential is the mail information of the client used to access the client. | |
Full Name | The owner of the credential is the client's full name. |
Enabled | Indicates whether the credential is active (available). If selected, it is active. |
Organization | The institution/organization information that the credential is related to can be optionally selected. It is kept for information/reporting purposes only. |
Roles | The roles that the credential has. Authorization is done according to these roles. For detailed information about authorization, you can visit the Authorization page. |
IP List | If the credential needs to come only from certain IP addresses, the information from which IP addresses this credential can be accessed is entered here. Leaving it blank means that the request will be accepted from all IPs. Entering this information alone is not enough for the rule to be run. In order for it to be active on any API Proxy, an authentication policy must be present on the relevant API Proxy, "Security Manager" must be selected as the identity provider in this policy, and the "Check Client Address" option must be activated just below. |
Description | This field can be filled if you want to enter a description about the identity information. |
Enabled Advanced Settings | If the credential, password and IP list need to be customized based on the environment, this option activates the customization settings. When selected, password and IP list can be entered for each environment. |
Environment Password | A password can be entered to be used specifically for the environment in the relevant line. If this field is entered, the password value entered here will be valid if API Proxies offered on this environment are authorized. If it is left blank, there will be no change in the use of the original password that was originally set. |
Environment IP List | An IP list can be entered to be used specifically for the environment in the relevant line. An IP list can be entered to be used specifically for the environment in the relevant line. If it is left blank, there will be no change in the use of the original IP list set first. |
Credential Access Control Settings
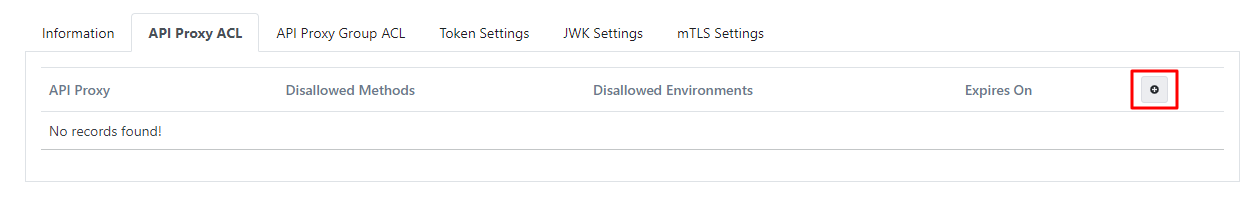
To set the access permissions of the credential, proceed to the Access Control List panel.
The API Proxy to be granted access in this panel is selected from the screen that appears by pressing the red-marked button in the image below.
From the screen that opens, the API Proxies you want to set are selected and the Add button marked in red below is pressed.
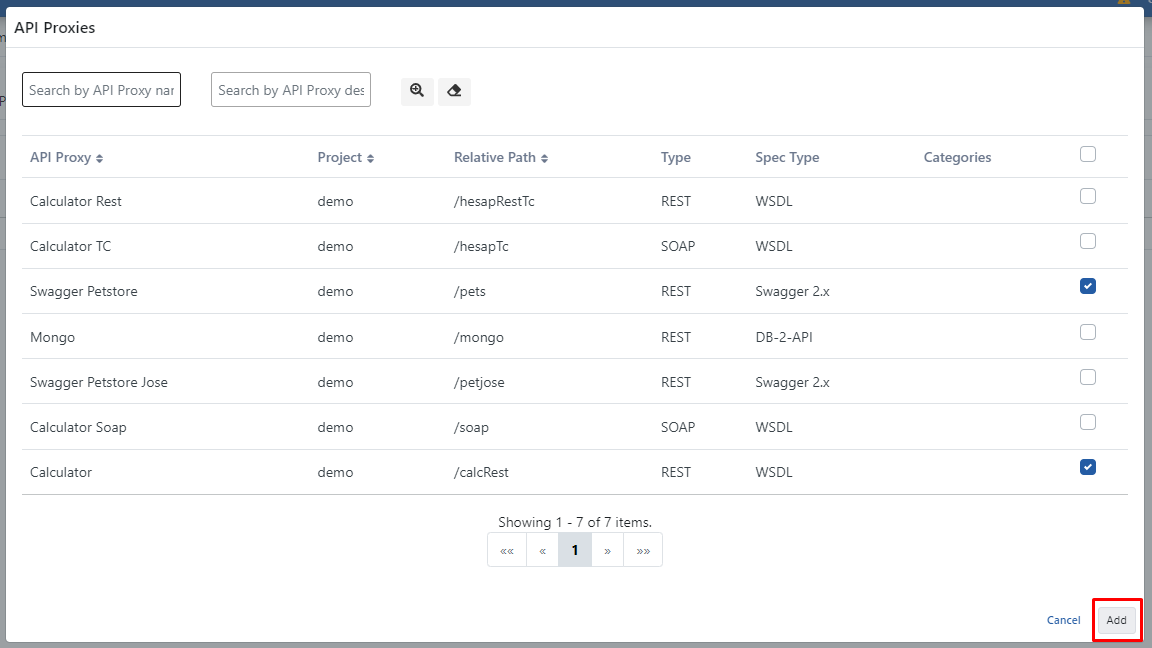
With this process, access permission is granted for the selected API Proxies to the credential. In order for this process to be active on live running rules, it must be loaded into environments.
For this, when the processes are completed, the settings are activated by pressing the Save and Deploy button in the upper right corner.
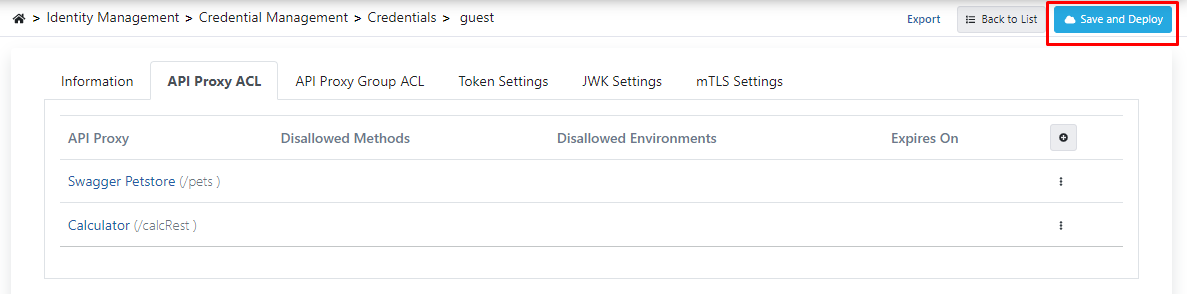
In order to customize the identity information on the basis of API Proxy, click on the Edit link on the line with the relevant API Proxy record from this screen.
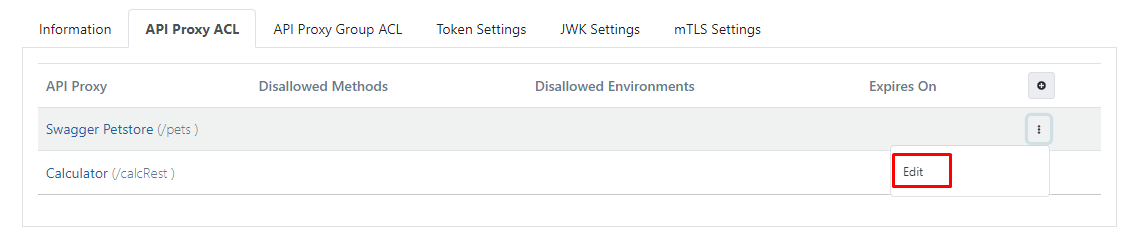
On the screen that appears, specific settings for this API Proxy can be made for the credential:
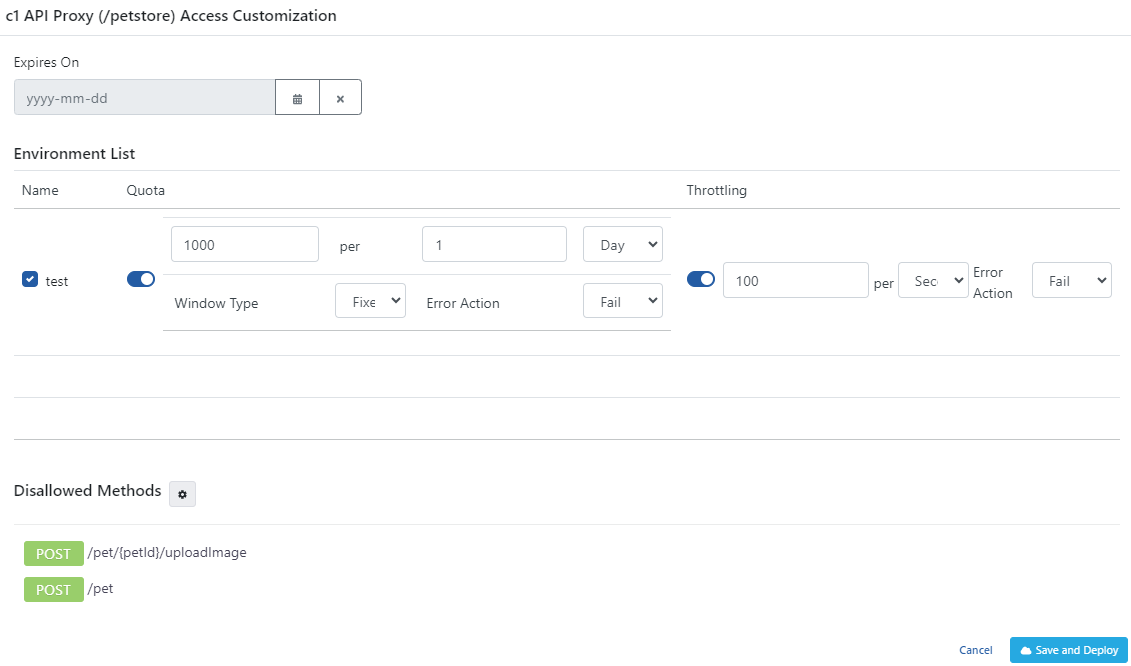
The fields used for API Proxy-based access customization configuration are shown in the table below.
| Field | Description |
|---|---|
Expires On | If this date value is entered, the Credential will be unable to access API Proxy as of this date (effective from 00.00 at night). If it is empty, it will continue to access the API Proxy unless it becomes inactive. The arrival of this date only restricts access to this API Proxy, it does not make any changes in accessing other API Proxies. |
Environment List | Allows entering Quota and Shrinkage values specifically for the environment in which API Proxy is installed. |
Quota | The specified environment specific Quota value of the API Proxy. |
Throttling | The Throttling value of the API Proxy specific to the specified environment. |
Message Count | It is the maximum number of messages that can be sent to the Backend API within the time given by the Throttling Interval. |
Interval Time Amount | The numeric value specifying the duration of the throttling window in the chosen time unit. |
Interval Time Unit | The time unit (e.g., seconds, minutes) used to define the throttling window for API request limits. |
Interval Window Type | The time interval method used for API rate limiting (fixed or sliding). |
| The timeout duration for the cache connection is specified. | |
Action for Cache Connection Error | Specifies the action to be taken if the policy has a connection problem with the cache server. |
Disallowed Methods | Regardless of the roles of the credential, if it is desired not to access any method of the API Proxy, the methods that the API Proxy wants to be disabled are selected here. By default, all methods of API Proxy can be accessed with the credential. |
Save and Deploy | After the settings/changes are completed, the settings are activated by pressing the Save and Deploy button. |
Token Settings
To change the token settings of the credential, proceed to the Token Settings panel.
The image containing the Token Settings is given below:
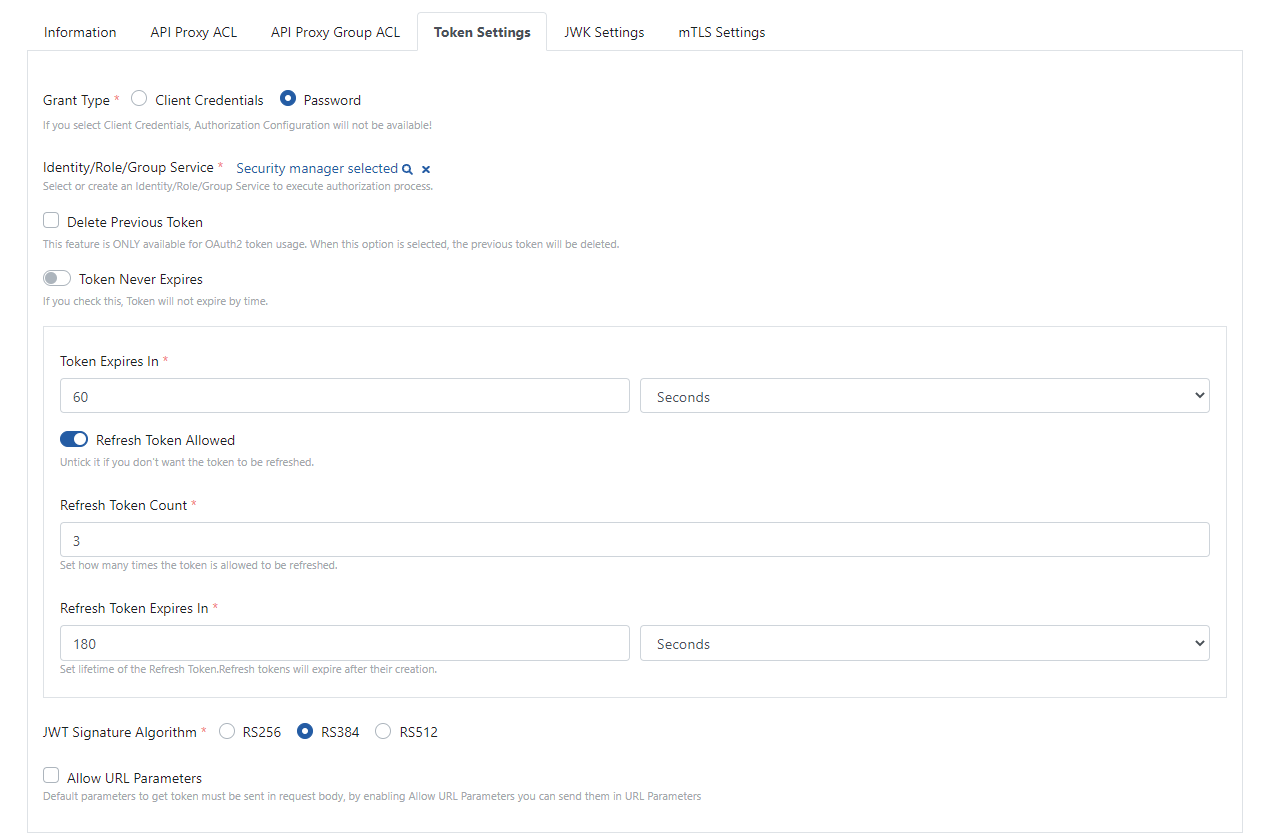
The fields used for Token Settings configuration are shown in the table below.
| Field | Description |
|---|---|
Grant Type | Accordingly, the information that will be requested for token production changes. See.
|
Identity/Role/Group Service | If Grant Type is Password; it is the identity provider service that specifies where to verify the username and password information to be sent. |
Select to JWT Regenerator Service API | This feature is only valid for JWT token usage. If the Grant Type is Password and the "API" option is selected from the Identity/Authorization Service, this field will be visible. It enables the JWT token value to be regenerated via the selected API without authentication. |
Delete Previous Token | This feature is only valid for OAuth2 token usage. In case of new token purchases or renewals, it invalidates the previous token. |
Token Never Expires | If this option is checked, the token does not become invalid over time, it can be used as many times as desired. |
Token Expires In | Specifies the lifetime during which the token will be available. |
Refresh Token Allowed | Enables the token's regeneration feature. |
Refresh Token Count | Specifies how many times the token can be regenerated. |
Refresh Token Expires In | In each renewal, it specifies how long the token will have to live. |
JWT Signature Algorithm | This feature is only valid for JWT token usage. It is used to select the signature algorithm to be used when generating the token. |
Allow URL Parameters | When sending a request for token generation to the Token Service, information is only allowed to be sent in the message body by default. If it is desired to allow this information to be sent as a URL parameter, this feature can be activated with this option. It is recommended not to be used as it will pose a risk in terms of security. |
JWK Settings
In the JWK settings tab, the necessary JWK keys are selected in order to decrypt the data of the incoming credential about the JWK keys and/or verify the signature.
The image containing the JWK Settings is given below:
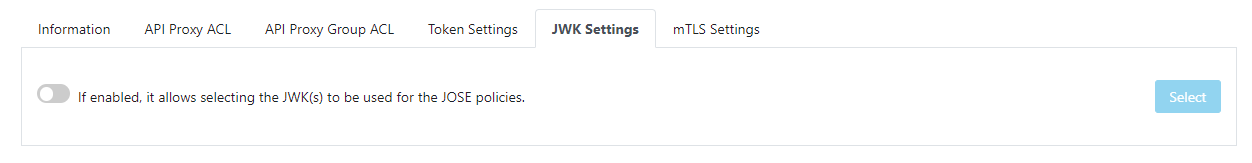
The image containing the JWK Settings when enabled is given below:
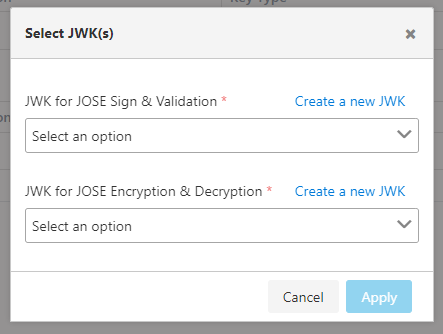
The fields used for JWK Settings configuration are shown in the table below.
| Field | Description |
|---|---|
JWK for JOSE Sign & Validation | This is the JWK key that the identity has for signing/verification operations. When the JOSE validation/implementation policies dictate that the user's key should be used, this JWK is used for signing/verification purposes. |
JWK for JOSE Encryption & Descryption | This is the JWK key that the identity has for encryption/decryption operations. When the JOSE validation/implementation policies dictate that the user's key should be used, this JWK is used for signing/verification purposes. |
mTLS Ayarları
In the mTLS settings tab, the truststore selection required for the incoming credential to be verified with the mTLS Authentication Policy is made.
The image containing the mTLS Settings is given below:
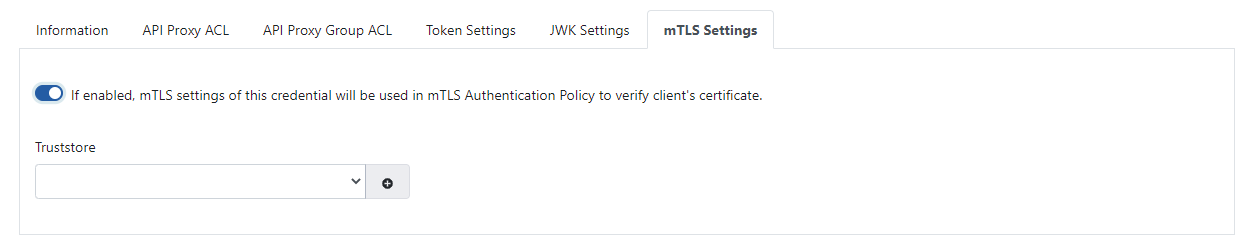
The fields used for mTLS Settings configuration are shown in the table below.
| Field | Description |
|---|---|
Truststore | Truststore is selected. If it is not defined before, a new one can be created by pressing the + button on the side. |