1) Adding LDAPs Connection Information
Open Connection Management → LDAP/Active Directory page and add your information. In the Server Address field, start with ldaps:// and add ldap domain and then 636 port. An example image containing LDAPs connection settings is provided below: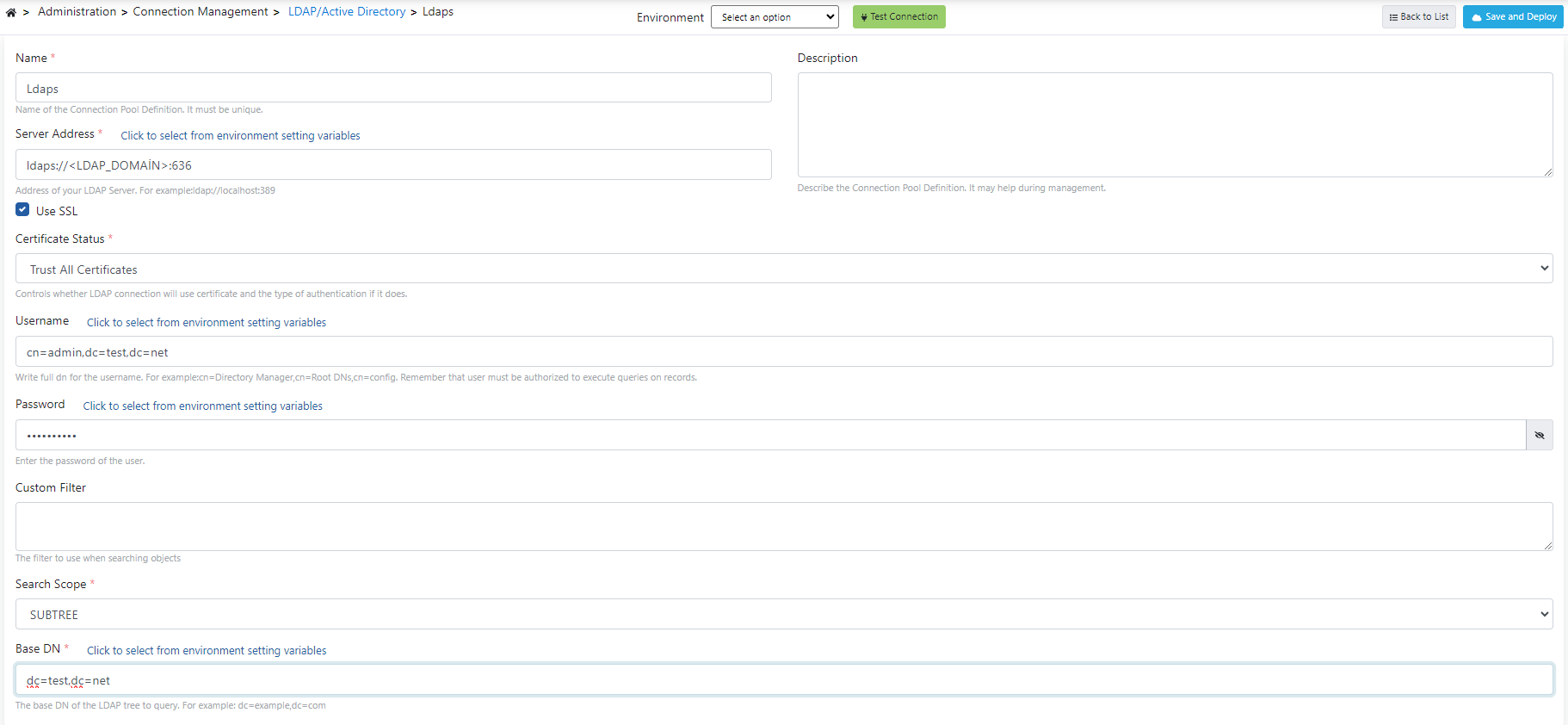
- Base DN for users:
ou=Users,dc=example,dc=com - Base DN for groups:
ou=Groups,dc=example,dc=com

2) LDAPs Login Settings
This section contains LDAP connection configurations that will enable integration with identity management systems in organizations that can be accessed via LDAP connection so that users can login to Apinizer. Open Administration → System Settings → LDAP Settings page.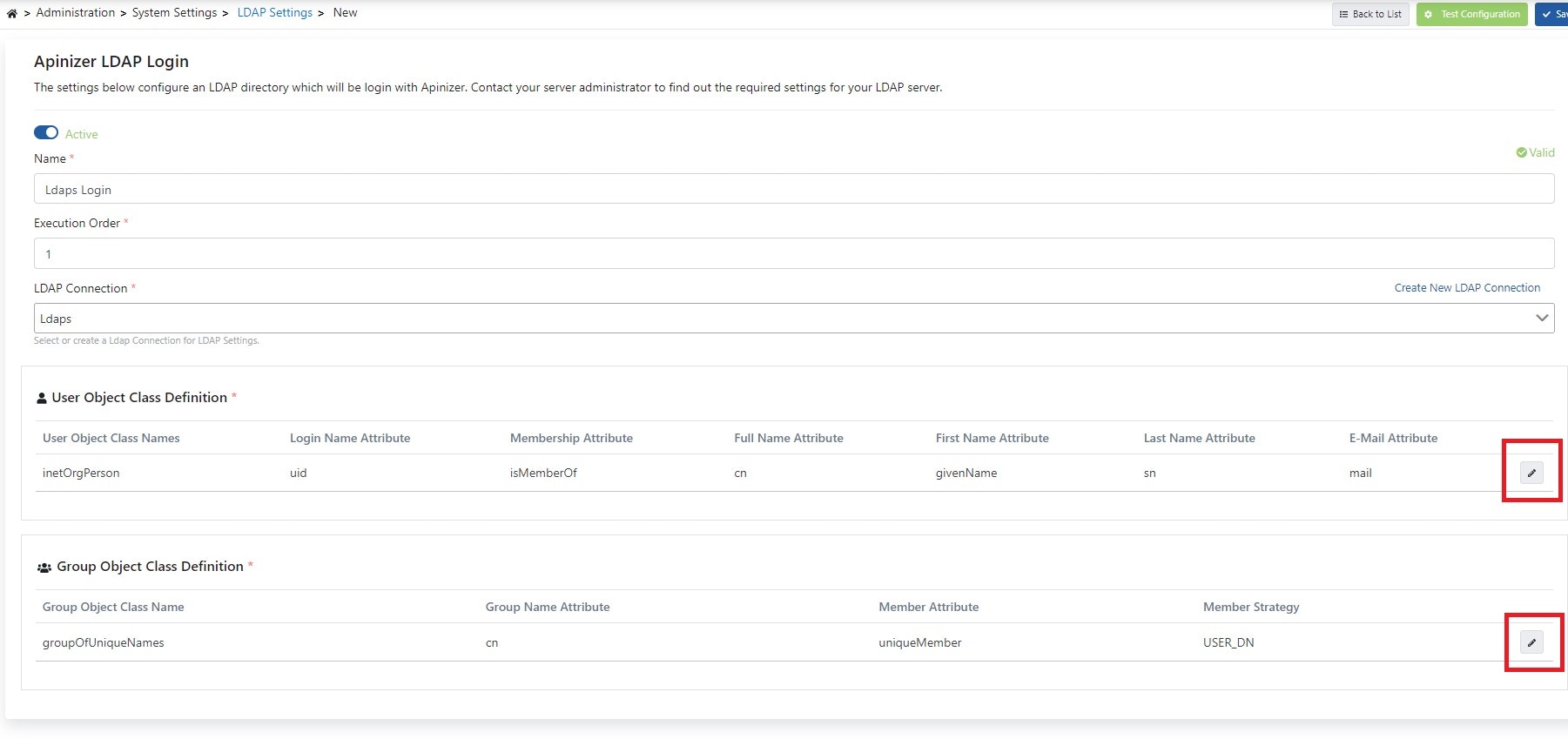

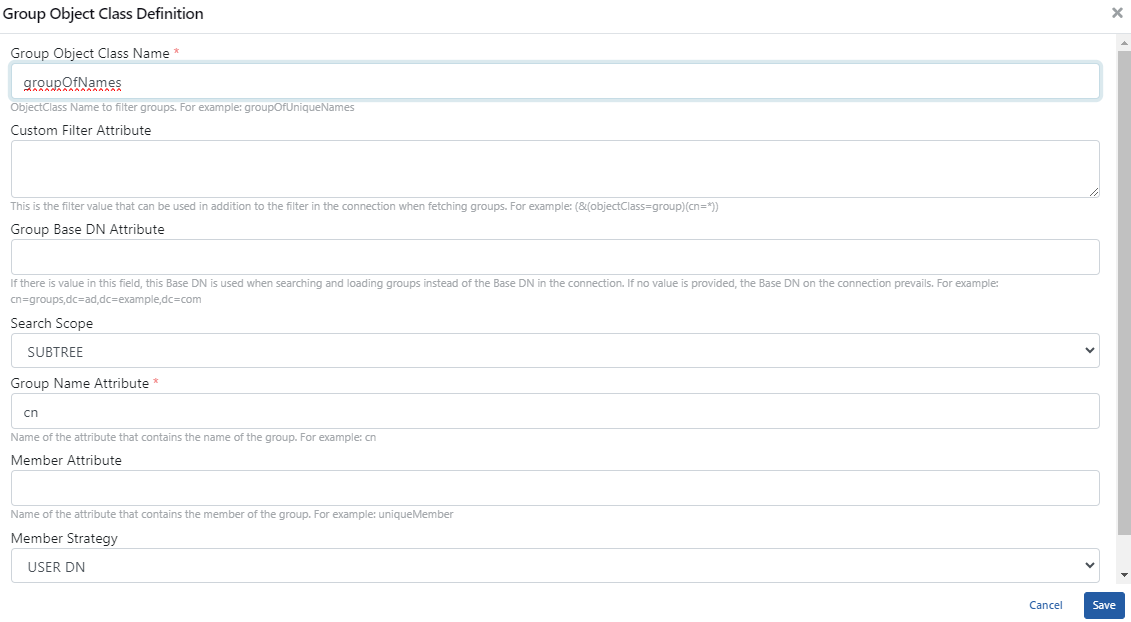
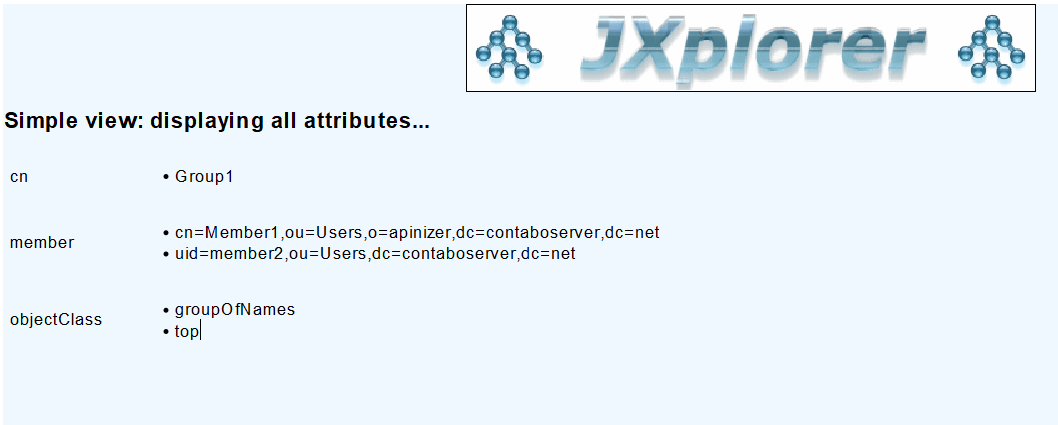
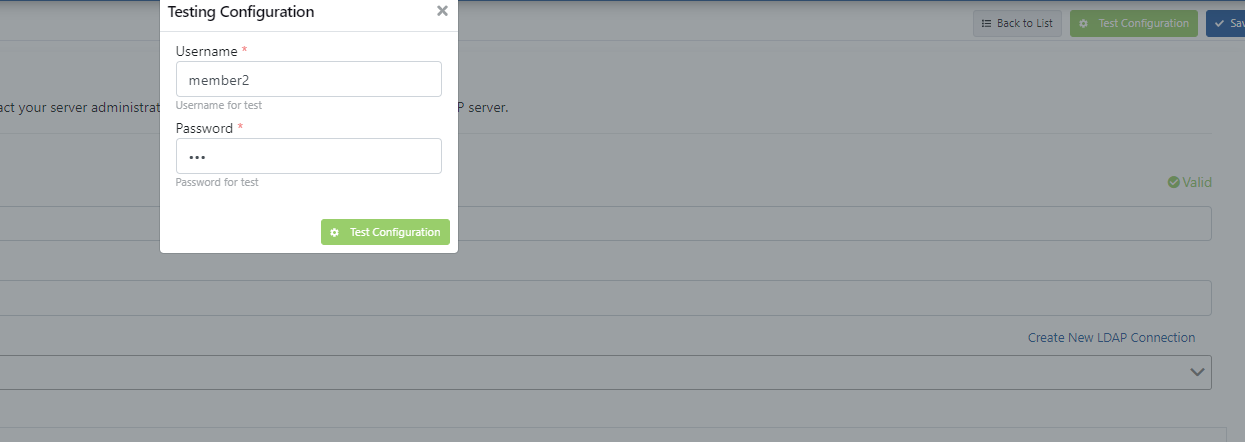
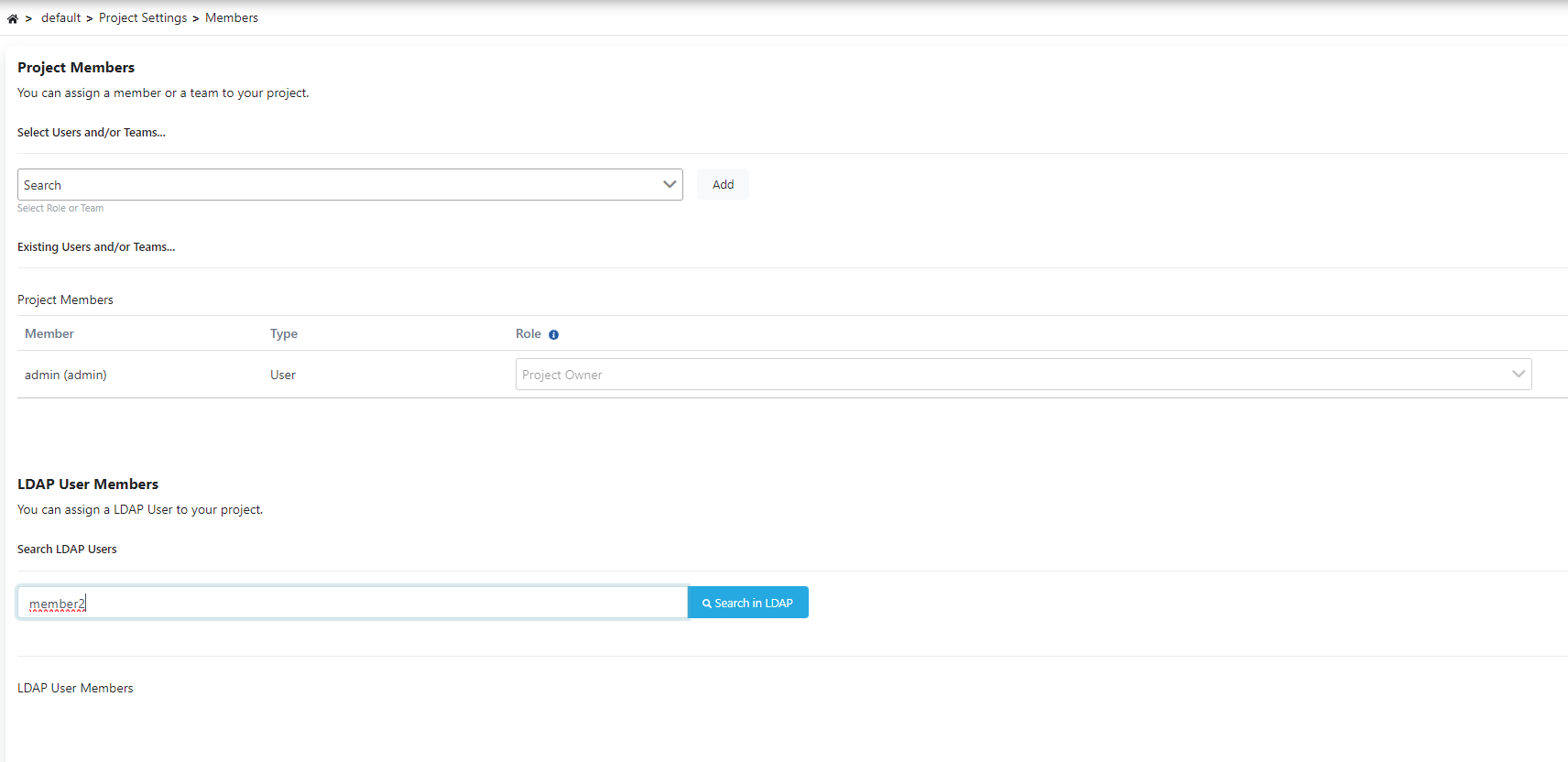
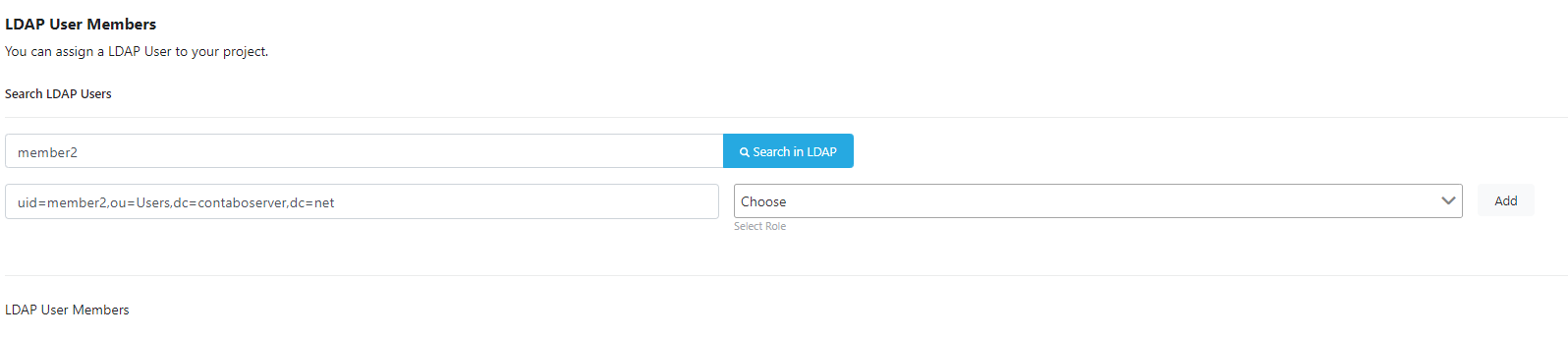
3) Authorizing LDAP Users or Group Members in Project
This section explains authorization operations for LDAP users and groups on a project basis. Select a project from the area where your projects are located as in the image below.