In the first sections of the content, step by step from the beginning; AKS installation, resource creation, usage and external MongoDb and ElasticSearch server steps are described.If there is a ready cluster on AKS, you can start directly from step 5 Installing Apinizer on AKS.
1. Introduction
What is Microsoft AKS (Azure Kubernetes Service)?
Azure is a complete cloud platform that facilitates new application development processes by hosting existing applications. Azure Kubernetes Service (AKS) enables creating, configuring and managing a pre-configured virtual machine cluster to run containerized applications. When you deploy an AKS cluster, Master nodes and all other kubernetes nodes are deployed and configured on your behalf.2. Installing and Configuring AKS, AKS CLI and kubectl
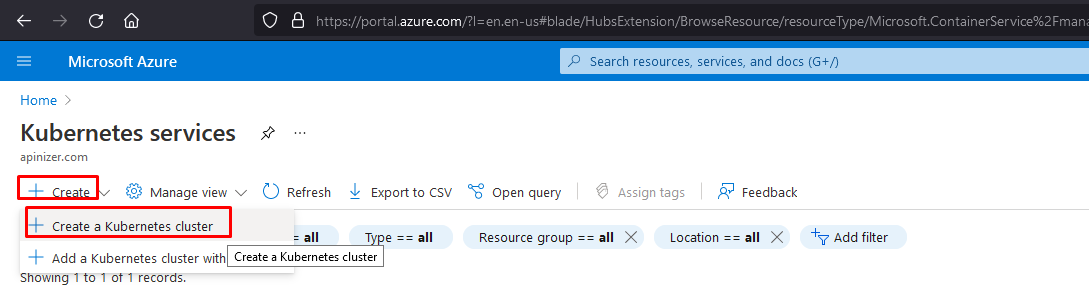
AKS Cluster Installation
Since Azure contains a structure targeting ease of use, installation can be done easily by proceeding with default settings if no special setting is requested.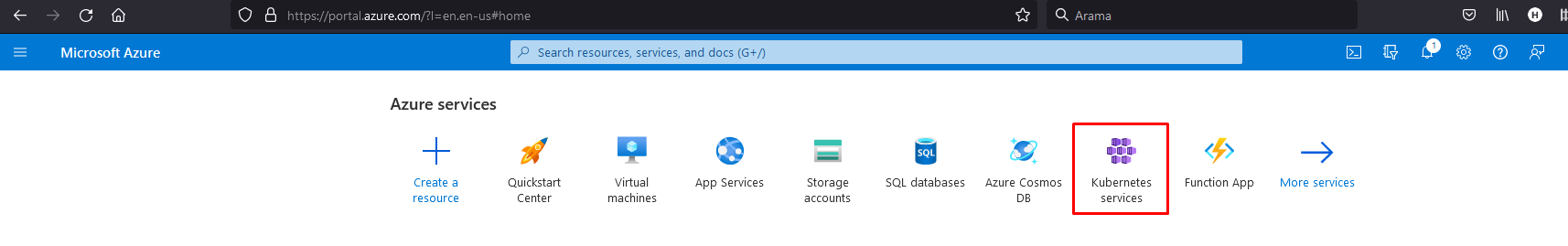
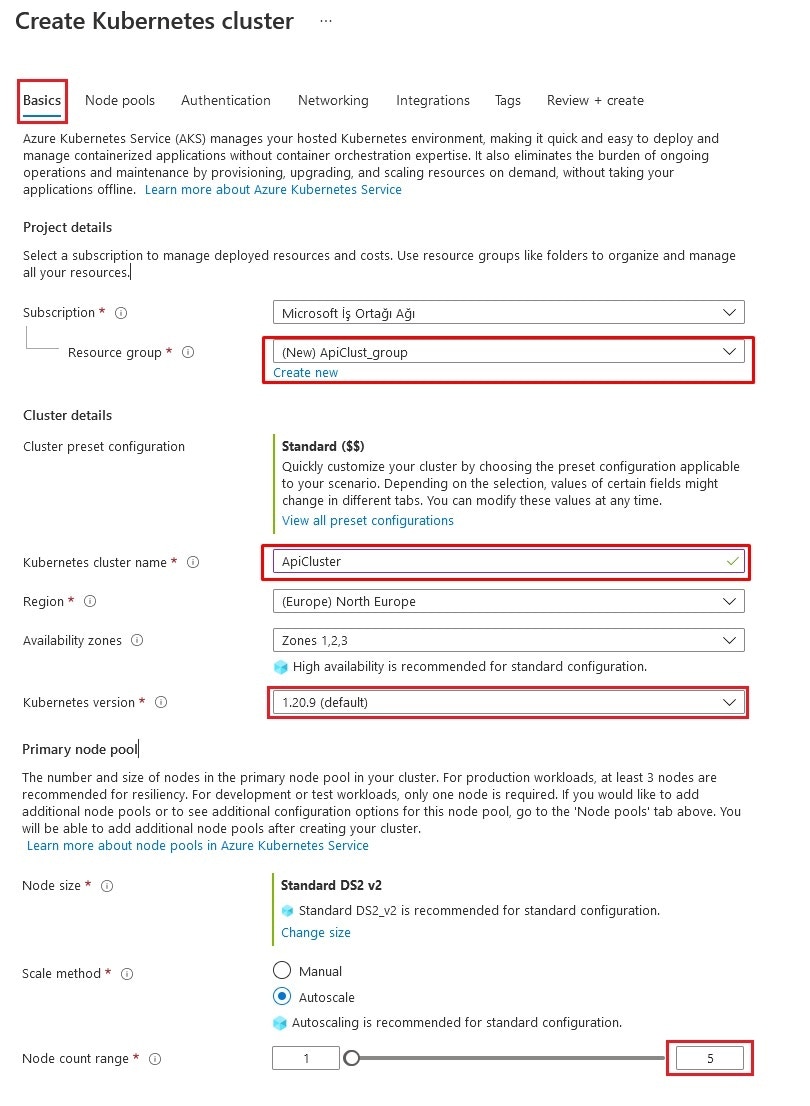
Adding Node Pool
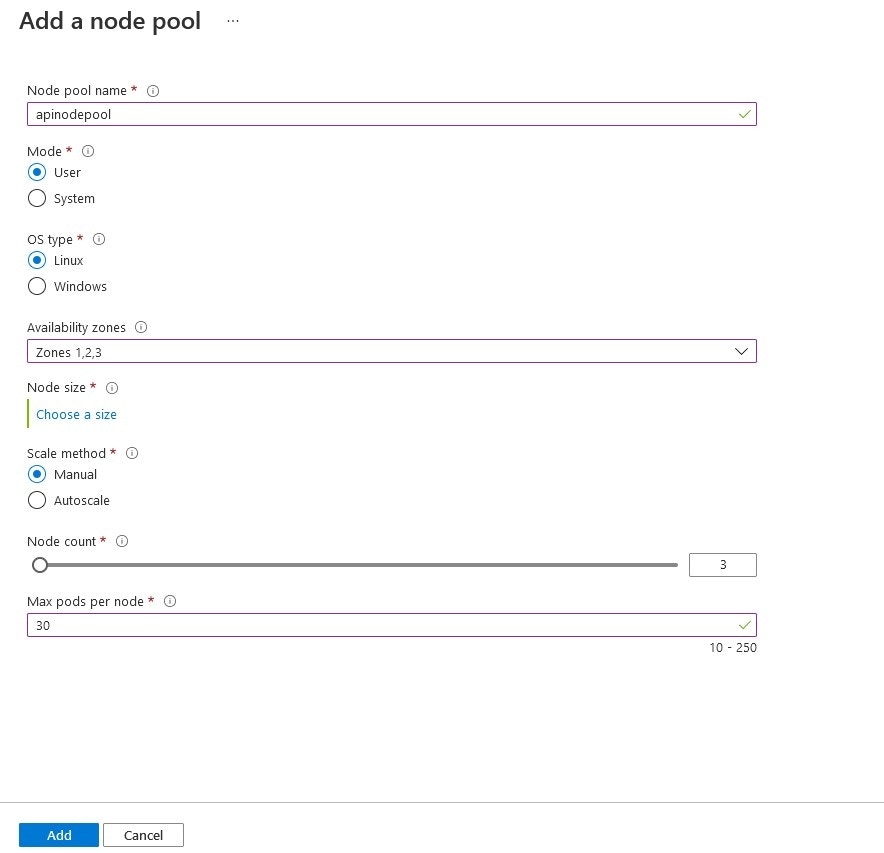
Node Pool (Node Pool) contains settings related to nodes within the cluster. You can select an existing node definition or create a new definition.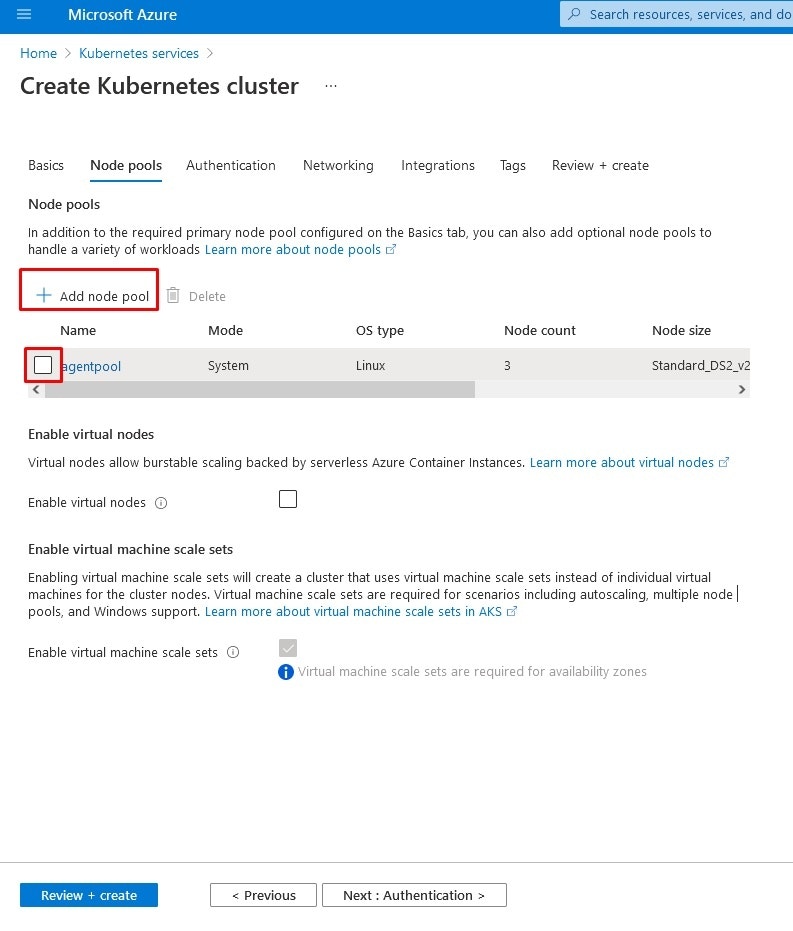
Authentication Settings
In the Authentication section, you can set how you want to restrict your cluster.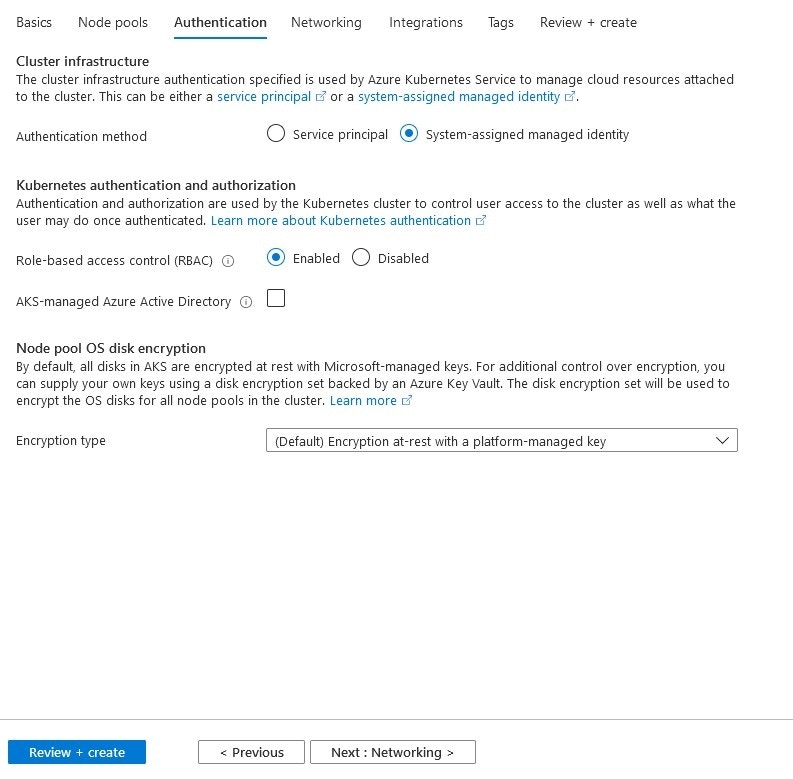
Networking Settings
The Networking tab includes whether you will leave network settings to Kubenet or Azure CNI, which draft you want your DNS name in, and security and network settings related to access.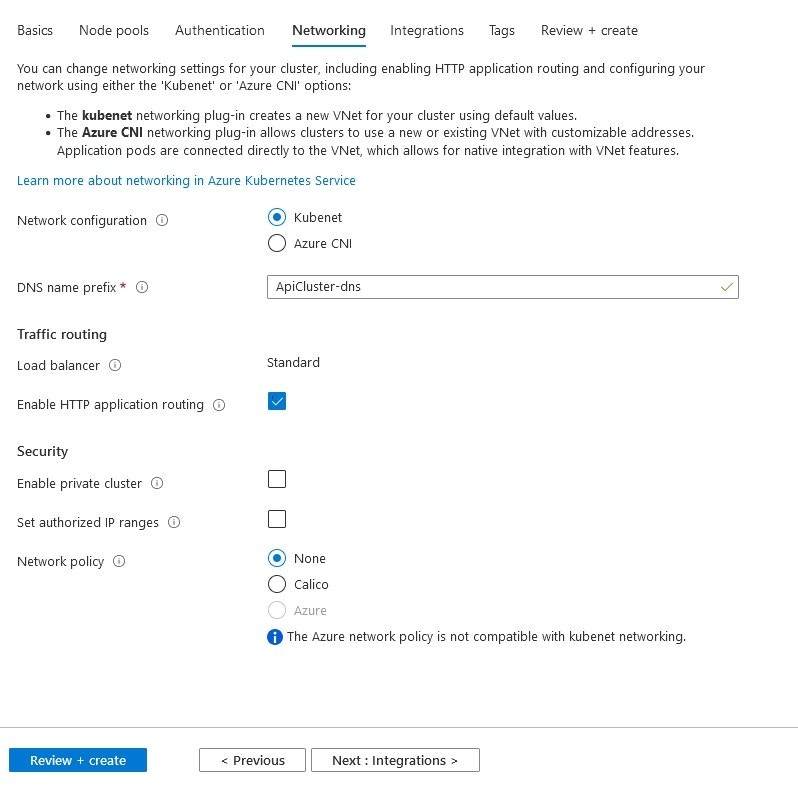
Integration Settings
In the Integrations tab, your decisions regarding some useful integrations provided by Azure are set.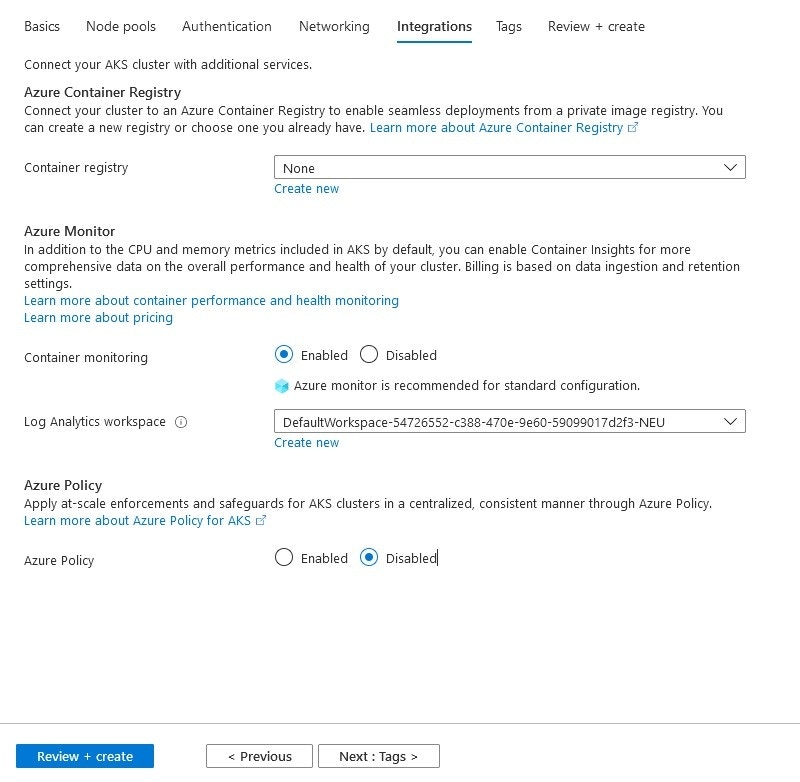
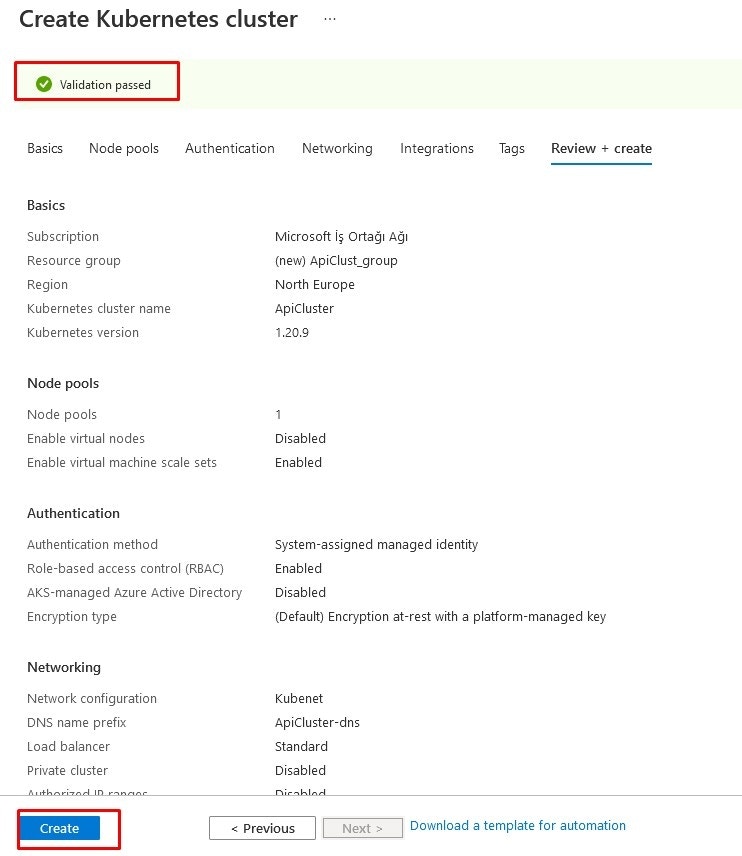
3. AKS CLI Installation
Azure CLI can be installed on Windows, MacOS and Linux environments. It can also be run in a Docker container. The version of Azure CLI suitable for the operating system can be downloaded and installed from: Azure CLI Installation Guide Then connect to your client account on your computer with the following command and the subsequent process.Signing in with Azure CLI
CLI can open your default browser and load an Azure sign-in page.Otherwise, open a browser page and go to: https://aka.ms/devicelogin. Enter the authorization code displayed in your terminal.If there is no web browser or the web browser cannot be opened, use the device code flow with the az login —use-device-code command.
4. Installing and Setting Up Cloud MongoDb and ElasticSearch
As stated in the Installation and Configuration document, Replicaset MongoDB and Elasticsearch are needed. These can be installed on any virtual server, used as cloud, or if they already exist, proceed to the next step. In this section, cloud systems in the applications’ own environments are used.- For MongoDB, go to MongoDB Atlas and create an account, and it can be used free of charge up to a limited DB size. Apinizer does not need a large database because it only keeps configuration definitions in MongoDB.
- For Elasticsearch, Apinizer can be defined by using an elastic service in the cloud environment through the Elastic Cloud address.
MongoDB Cloud Settings
After creating an account from MongoDB’s own site, create a database with the desired name and edit the related settings. Click the Add IP Address button from the Network Access menu for access permission.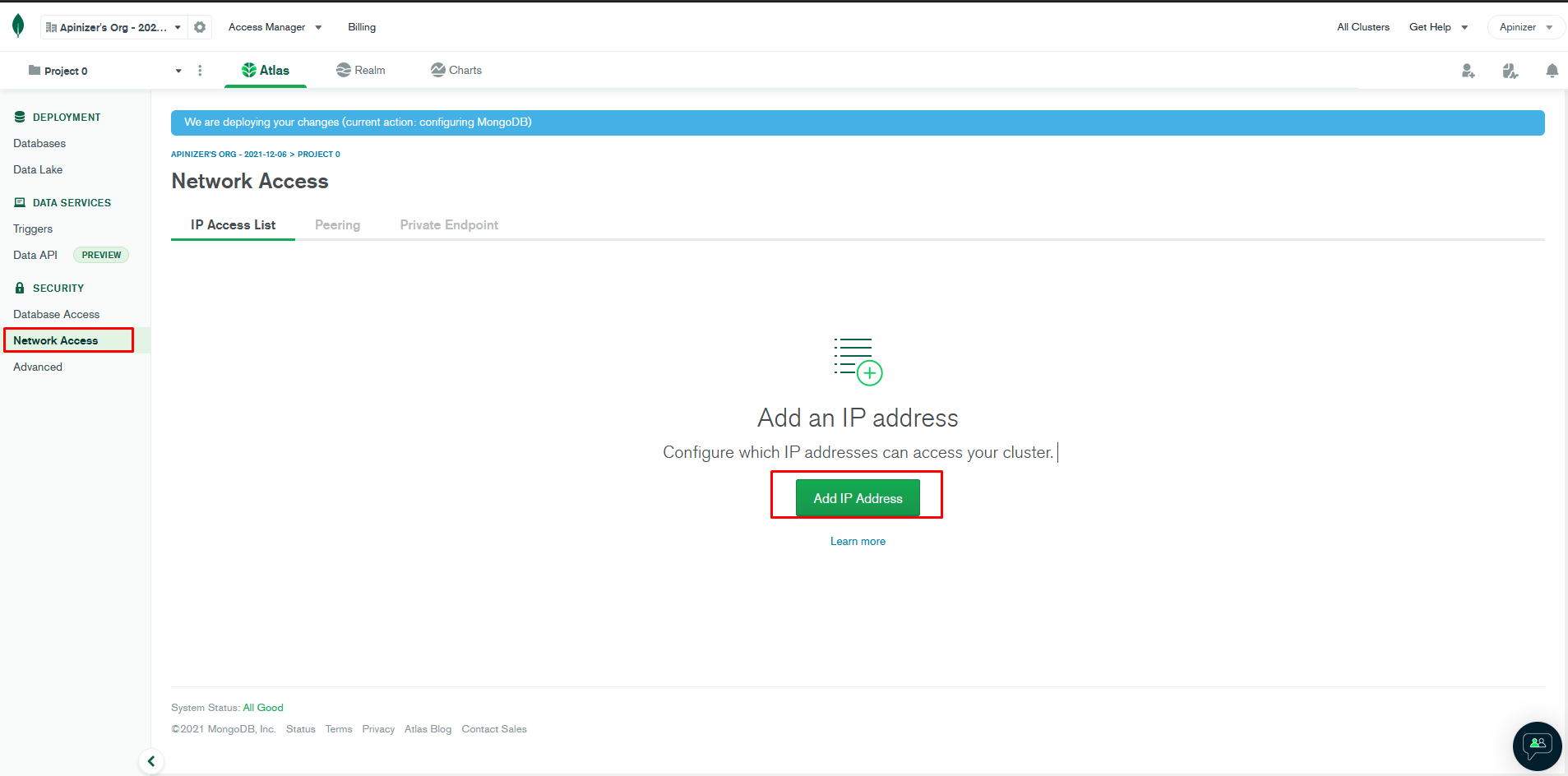
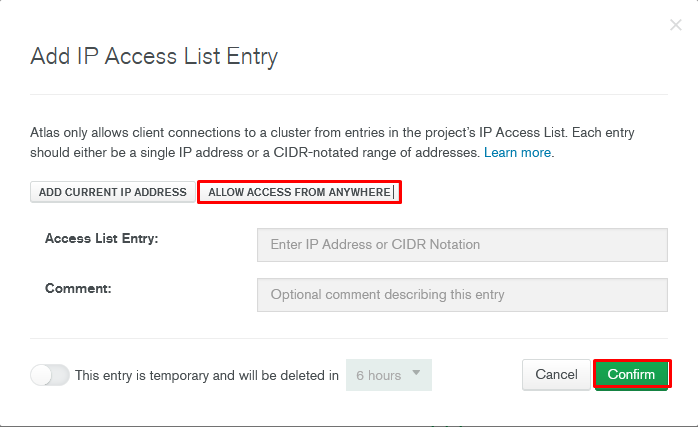
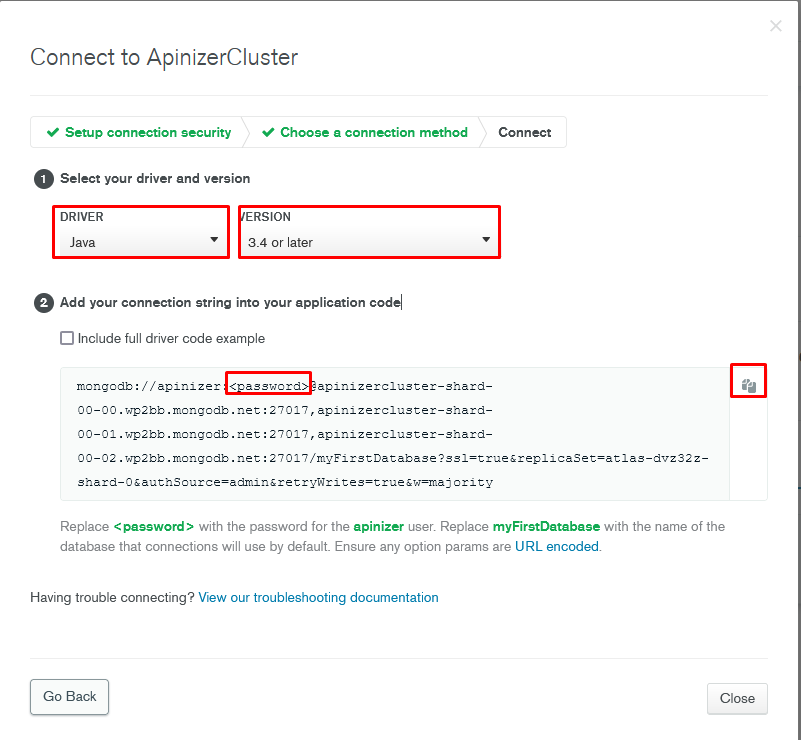
Getting MongoDB connection string:
To get the connection string (Connection String) that will provide the connection to the created database, return to the Databases page and press the Connect link. From here, you can get the necessary information to connect to any MongoDb database editor yourself, or press the Connect your application button to connect the Apinizer application.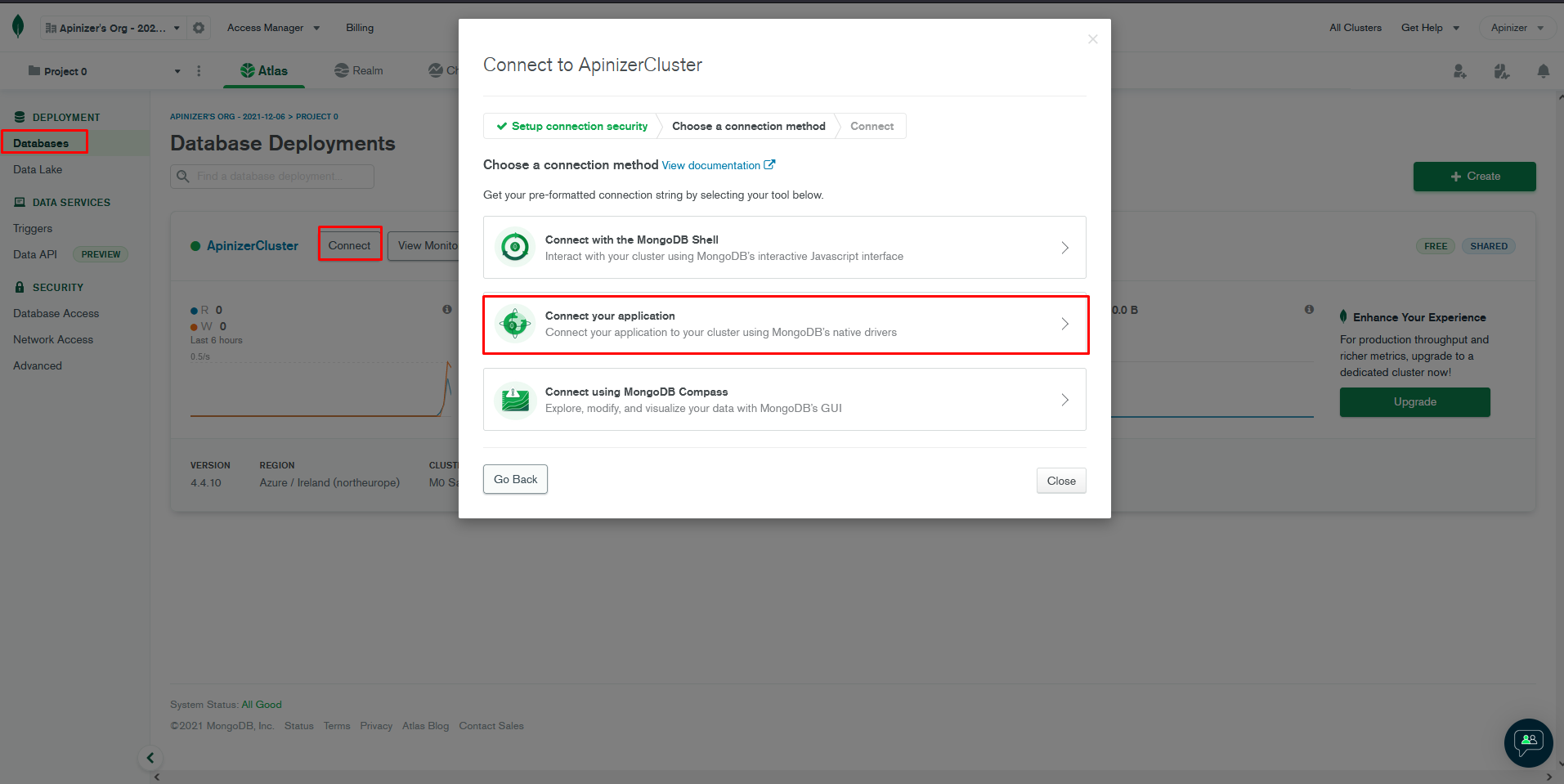
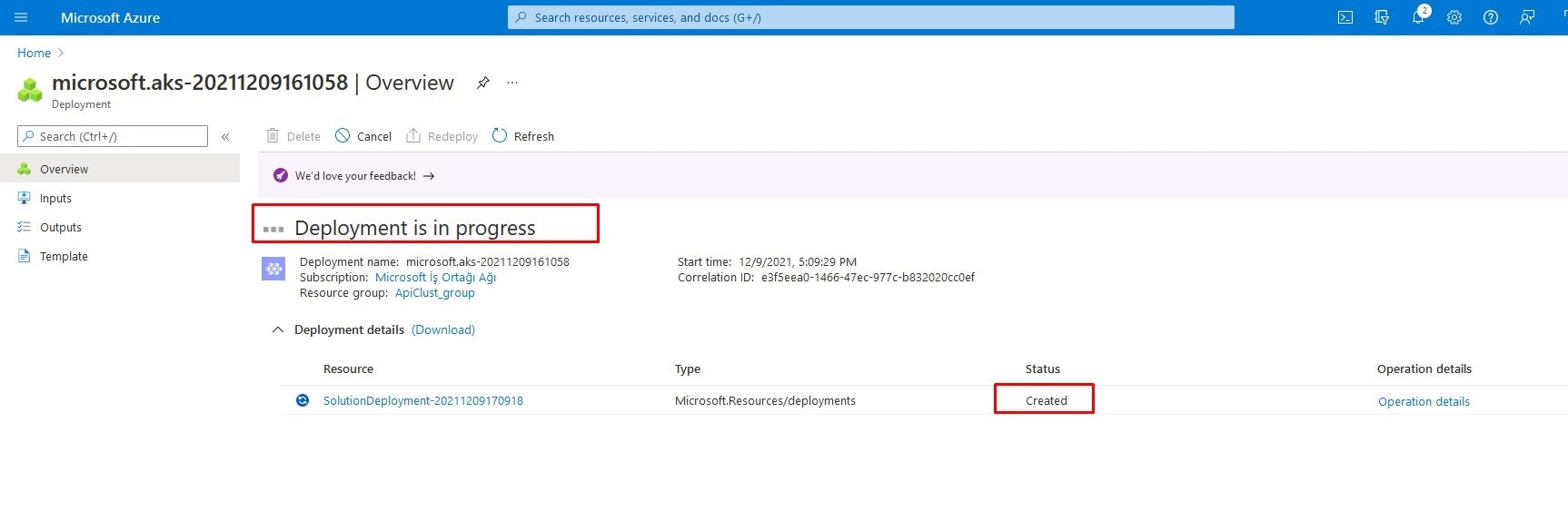
5. Installing Apinizer on AKS
What is described under this heading describes the definition of opening Apinizer as a service, different from Apinizer installation documents.Apinizer Management Console installation
A .yaml file should be created for Apinizer and loaded to AKS cluster. Example apinizer-deployment.yaml file settings are below:Creating Access Service for Apinizer Management Console
After the installation is completed, a service is needed to access Apinizer Management Console. A service is created by following the steps below. It may take a minute or two to get the external IP sometimes.6. Apinizer Management Console Login
Login is made by writing the service access address in step 2 to the browser’s address bar. You can contact Apinizer support team for default username password. The Apinizer Management Console Address created according to these settings:http://<EXTERNAL-IP>/
7. Apinizer Configurations
Defining Log Servers
Apinizer stores API traffic and metric information in Elasticsearch database. To continue the installation process, Elasticsearch cluster definitions need to be made. Go to Administration → Server Management → Elasticsearch Clusters page from the menu in Apinizer Management Console application. The image containing Elasticsearch cluster definition settings is given below: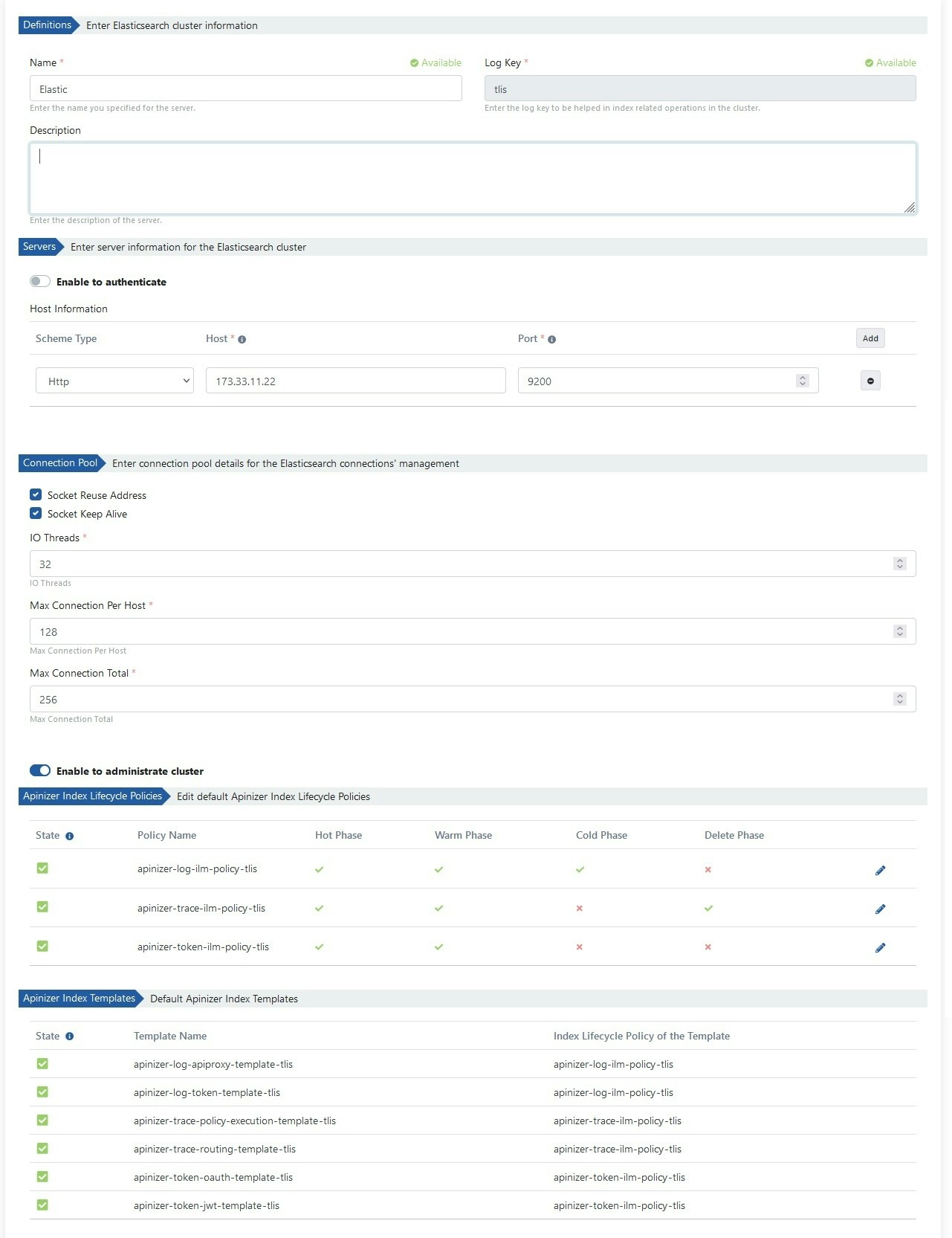
Environment Definition
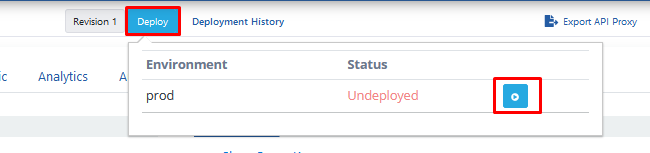
At least one environment needs to be loaded (deploy) for an API Proxy to be accessible. Apinizer also allows an API Proxy to be loaded to multiple environments. Go to Administration → Server Management → Gateway Environment page from the menu in Apinizer Management Console application. The image containing environment definition settings is given below: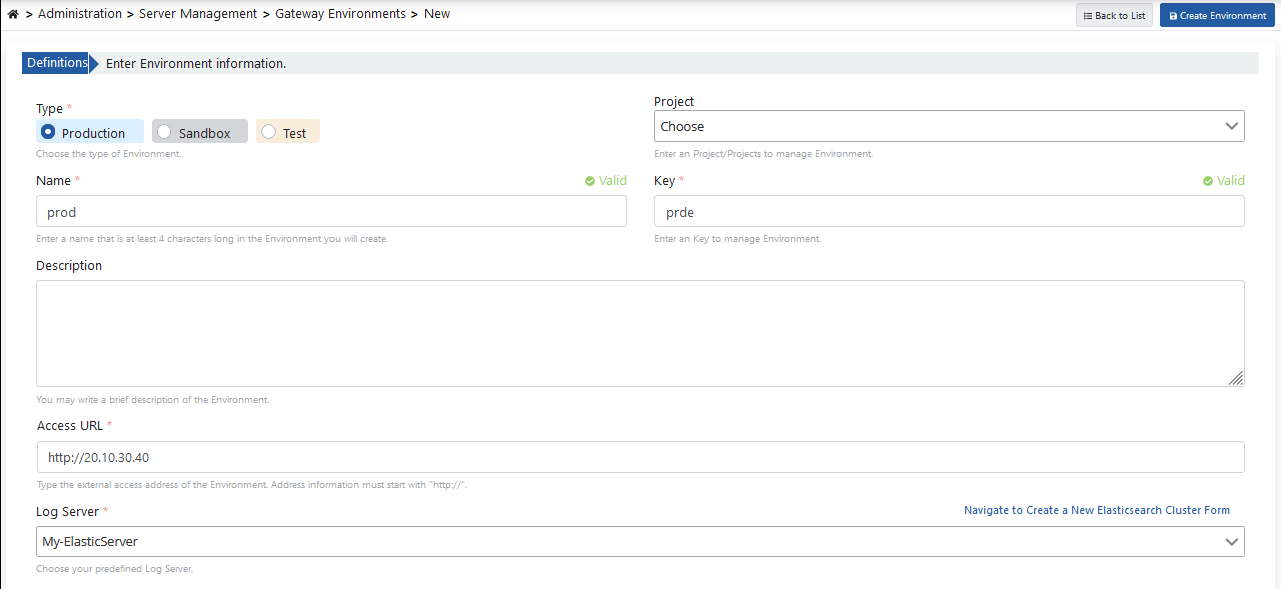
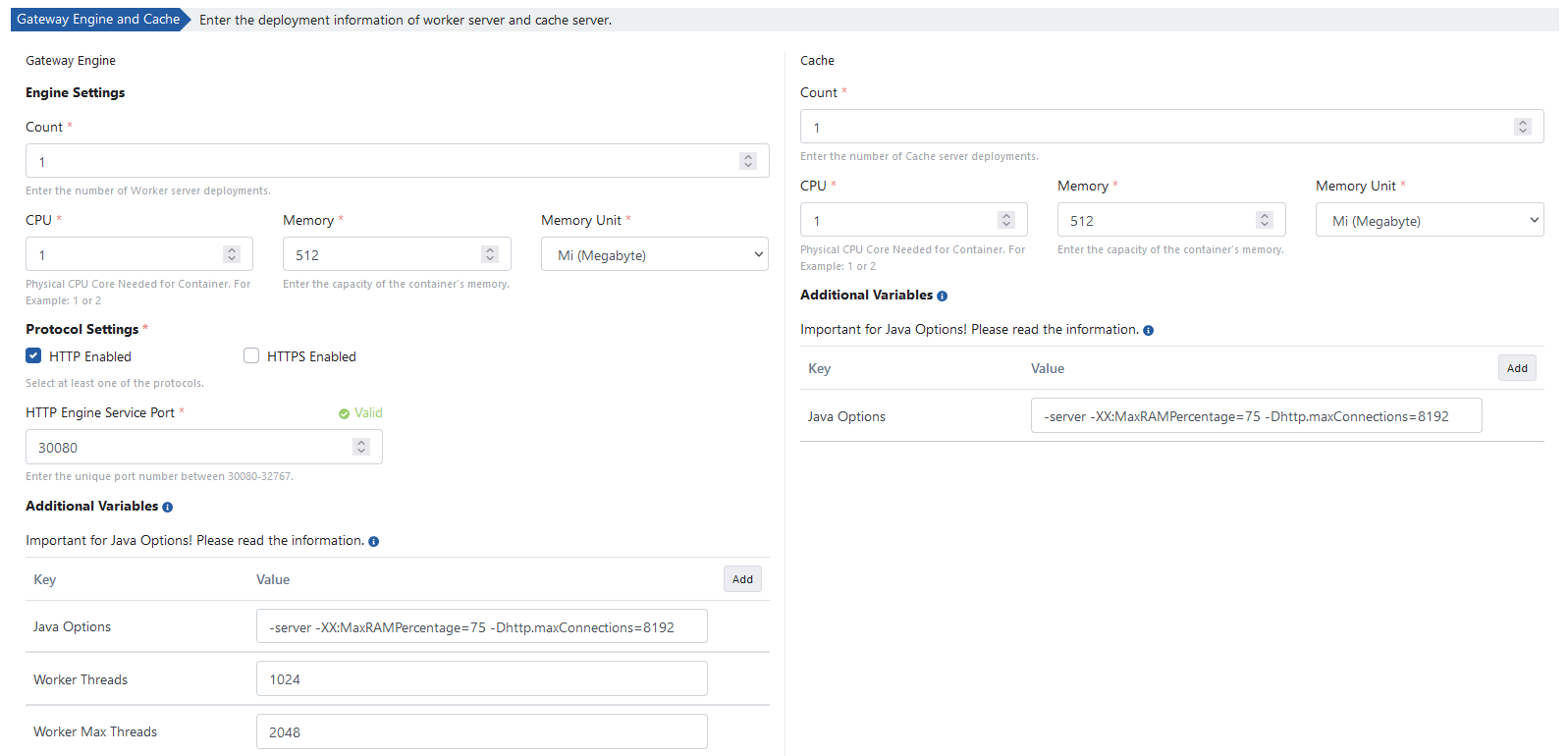
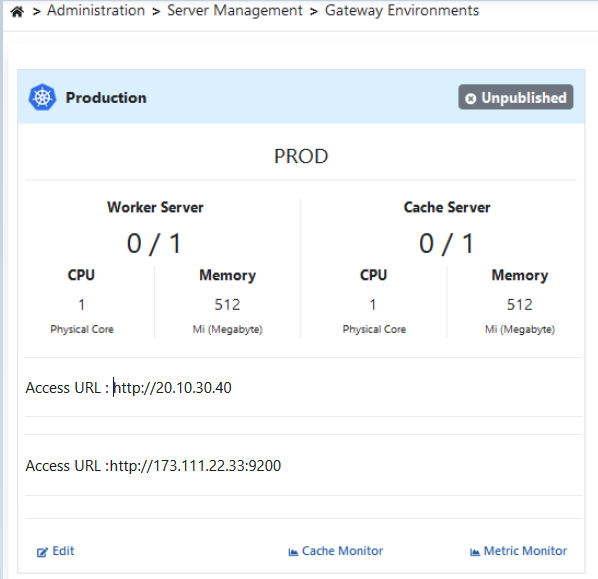
Opening Environment as Service
Finally, a service needs to be created to access APIs that will run in the environment we published.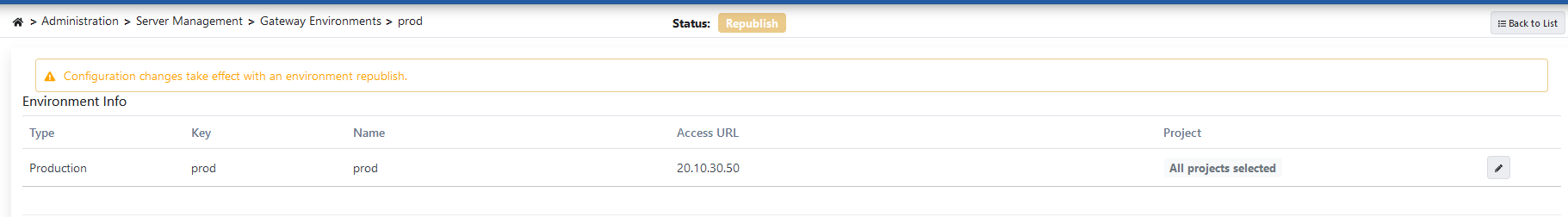
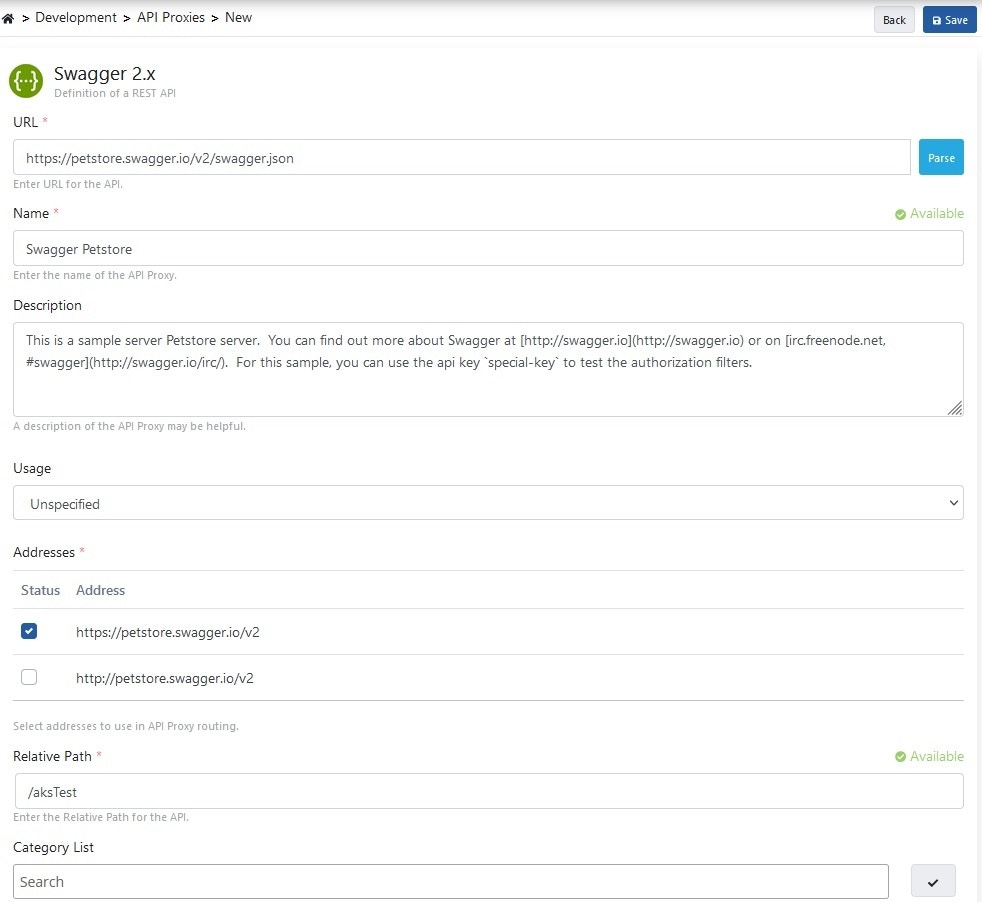
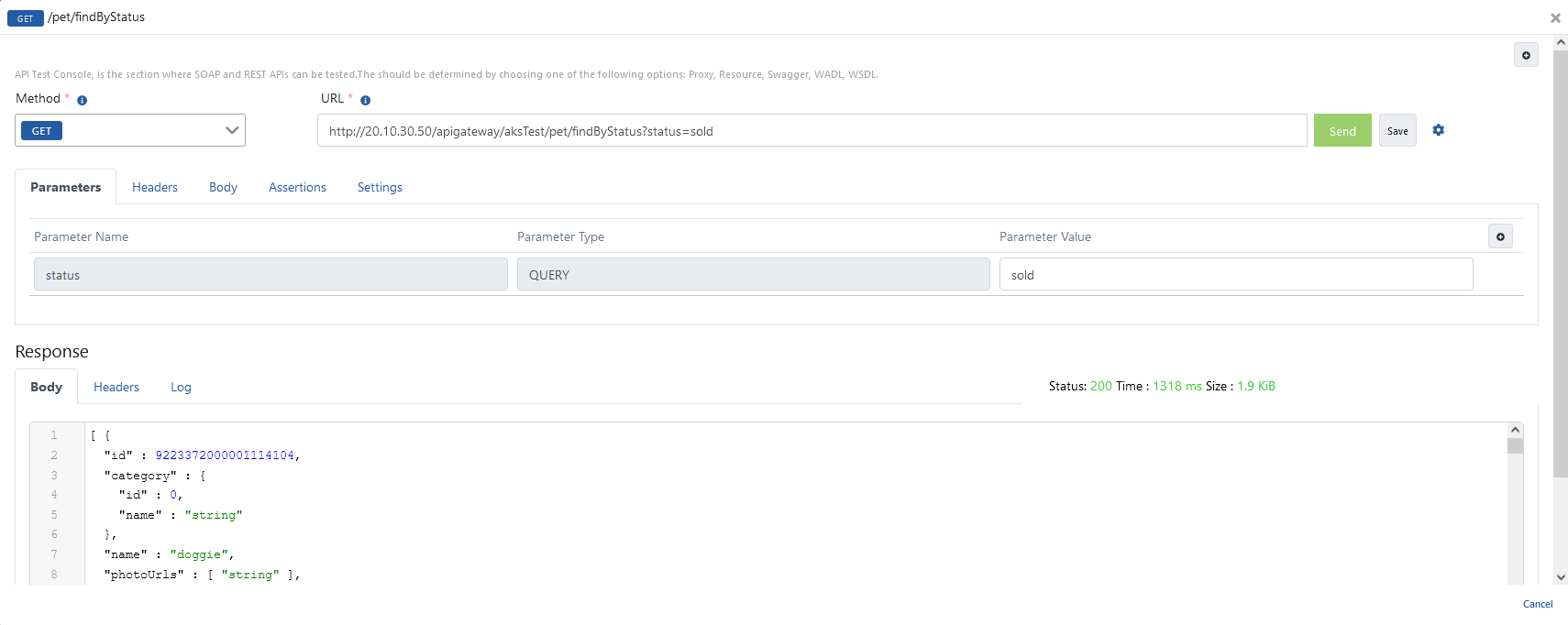
8. Publishing and Testing the First API in Apinizer
In the last step, opening an API to Apinizer as an API Proxy through a sample API definition file is described. The project where the API Proxy will be registered is selected from the navbar menu.