Message Flow and Pipeline Structure
Client and Backend API
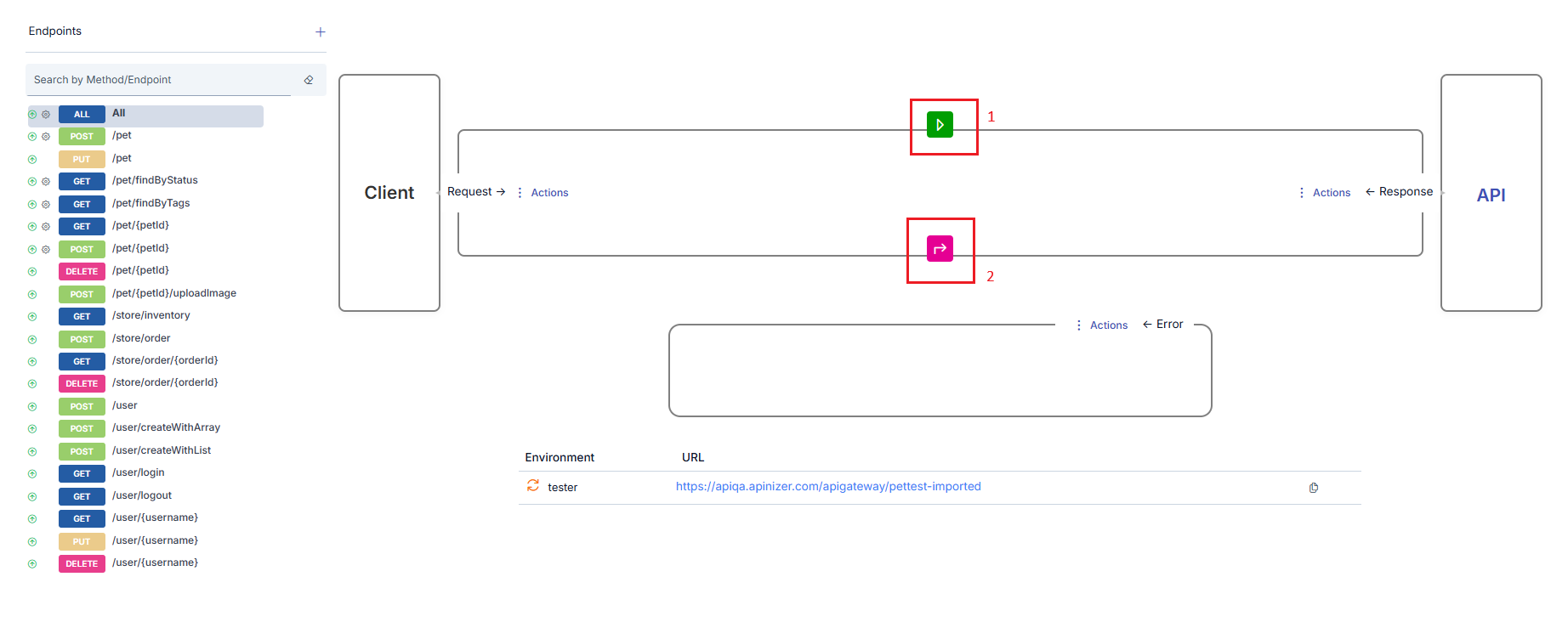
The flow between the client and Backend API is shown with the following elements:- An arrow symbolizing the request message going from the client to the Backend API
- An arrow symbolizing the response message going from the Backend API to the client
- Icons showing the policies applied on request or response messages and the application order
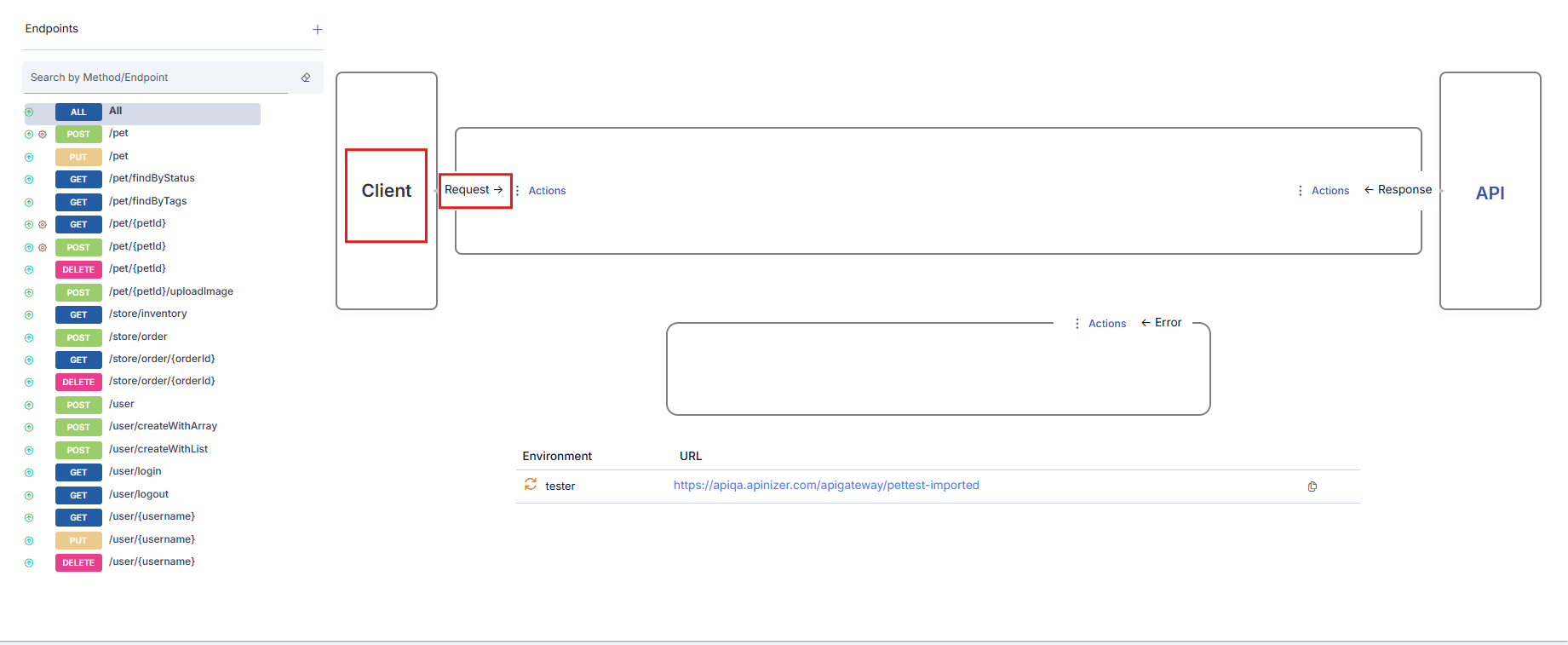
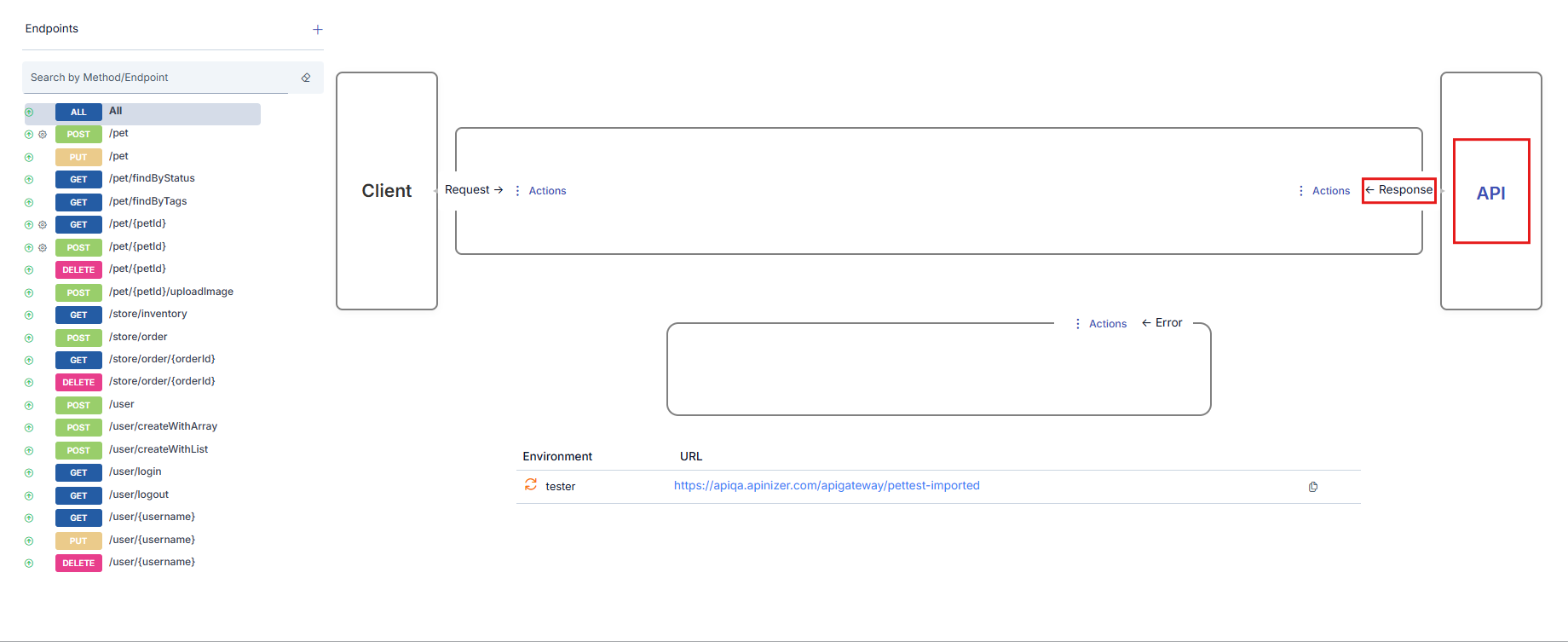
Details of policies will not be covered in this section. For detailed information about policies, you can refer to the What is Policy? page.
Request Pipeline
Request Pipeline is the pipeline where requests from clients are processed before being sent to the backend.Request Pipeline Flow
Request Pipeline consists of the following stages:- Pre-flow Policies: Security and validation
- Conditional Policies: Conditional operations
- Routing Step: Routing to backend
Response Pipeline
Response Pipeline is the pipeline where responses from the backend are processed before being sent to the client.Response Pipeline Flow
Response flow is processed in the following order:- Post-flow Policies (Response): Response transformation
- Conditional Policies: Conditional operations
- Logging: Operation record (Asynchronous)
- Client Response: Response to client
Error Pipeline
Error Pipeline is the pipeline where error conditions are processed. Error Pipeline comes into play when an error occurs in the Request or Response pipeline.Error Pipeline Flow
In error conditions, the following flow is followed:- Fault Handler Policies: Error handling policies
- Error Transformation: Error message transformation
- Error Logging: Error record
- Error Response: Error response to client
Policy Execution Order in Error Conditions
Policies to be executed in error conditions are added with the “Add Error Policy” option. If there is an error at any point in the flow, the normal flow is interrupted and first, if available, the error response template is applied to the error message. Then, policies added to the “Error Policies” line are executed from right to left in order.Conditional Policy Execution
Policies can be executed conditionally. Conditional policy execution enables applying different policies based on message content, header values, query parameters, IP address, time-based conditions, or system variables. For detailed information about conditional policy execution, you can refer to the Conditional Policy Execution page.Policy Management
Policies are configurations made to describe operations such as security, message filtering, validation, transformation or enrichment, partial business logic implementation, error management, etc., to be performed on request and response messages. The API Gateway executes the policies introduced to it with these configurations during the message flow between the Client and Backend API.This section generally describes operations that can be performed on policies. To get detailed information about any policy, you can refer to the relevant policy documentation from the What is Policy? page.
Policy Location and Execution Order
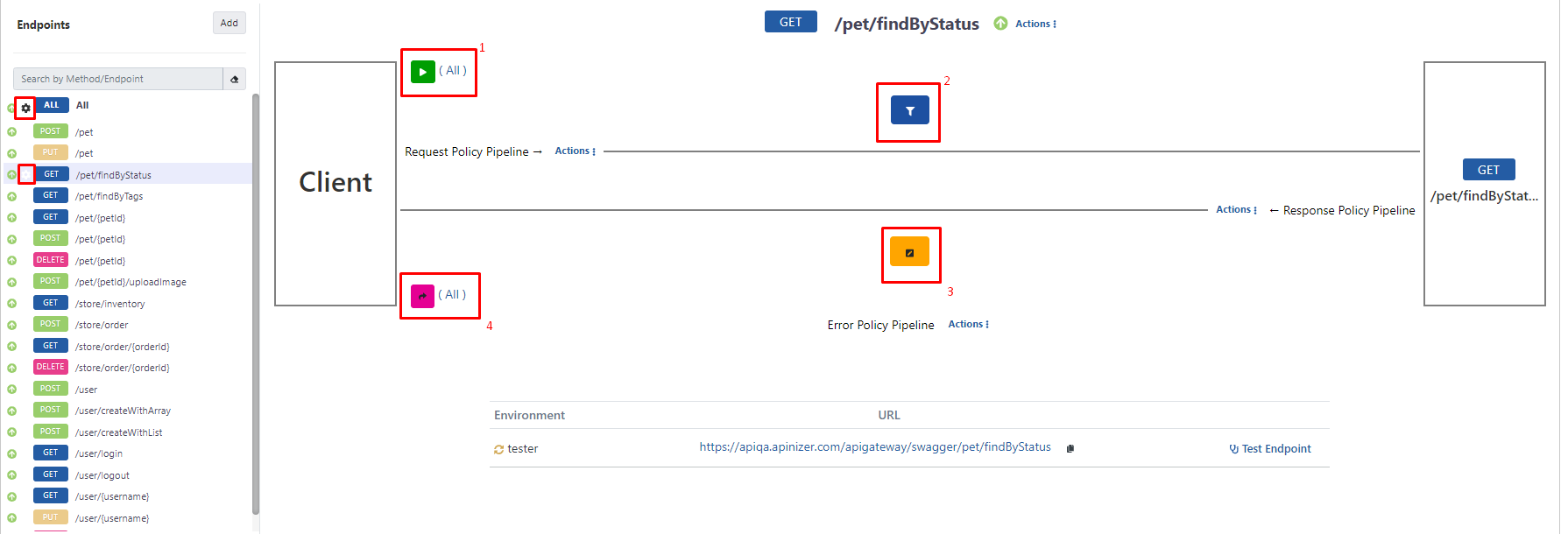
Policies can be added at 3 different points:- API Proxy Group
- API Proxy
- Method/Endpoint
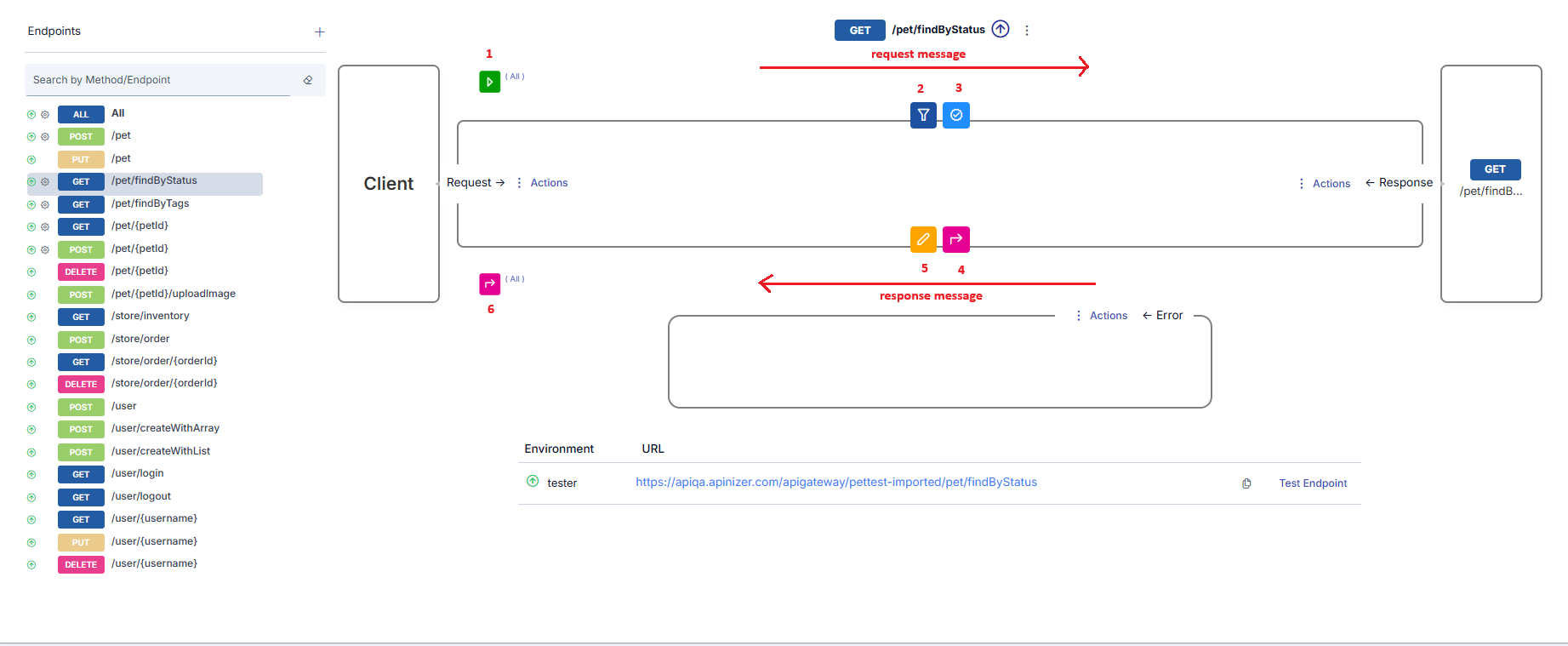
- The area marked with frame 1 shows policies added for all methods/endpoints of this API Proxy, valid for all methods/endpoints, and to be applied to request messages. The text All indicates this.
- The area marked with frame 2 shows policies valid for the selected method/endpoint and to be applied to request messages.
- The area marked with frame 3 shows policies valid for the selected method/endpoint and to be applied to response messages.
- The area marked with frame 4 shows policies added for all methods/endpoints of this API Proxy, valid for all methods/endpoints, and to be applied to response messages. The text All indicates this.
- The area marked with frame 1 shows policies added for all methods/endpoints of this API Proxy, valid for all methods/endpoints, and to be applied to request messages.
- The area marked with frame 2 shows policies added for all methods/endpoints of this API Proxy, valid for all methods/endpoints, and to be applied to response messages.
Policy Execution Order
Policies are executed in the message flow order:- For request messages: API Proxy Group → API Proxy → method/endpoint in order
- For response messages: method/endpoint → API Proxy → API Proxy Group in order
Adding Policy to Flow
To add a policy:Entity Selection
The entity where the policy is to be added is selected. For example, for a policy to be applied to all methods/endpoints of an API Proxy, All is selected in that API Proxy’s method/endpoint field.
Adding Policy
The ➕ Add Policy icon in the appropriate area is clicked according to whether the policy is to be added to request messages or response messages.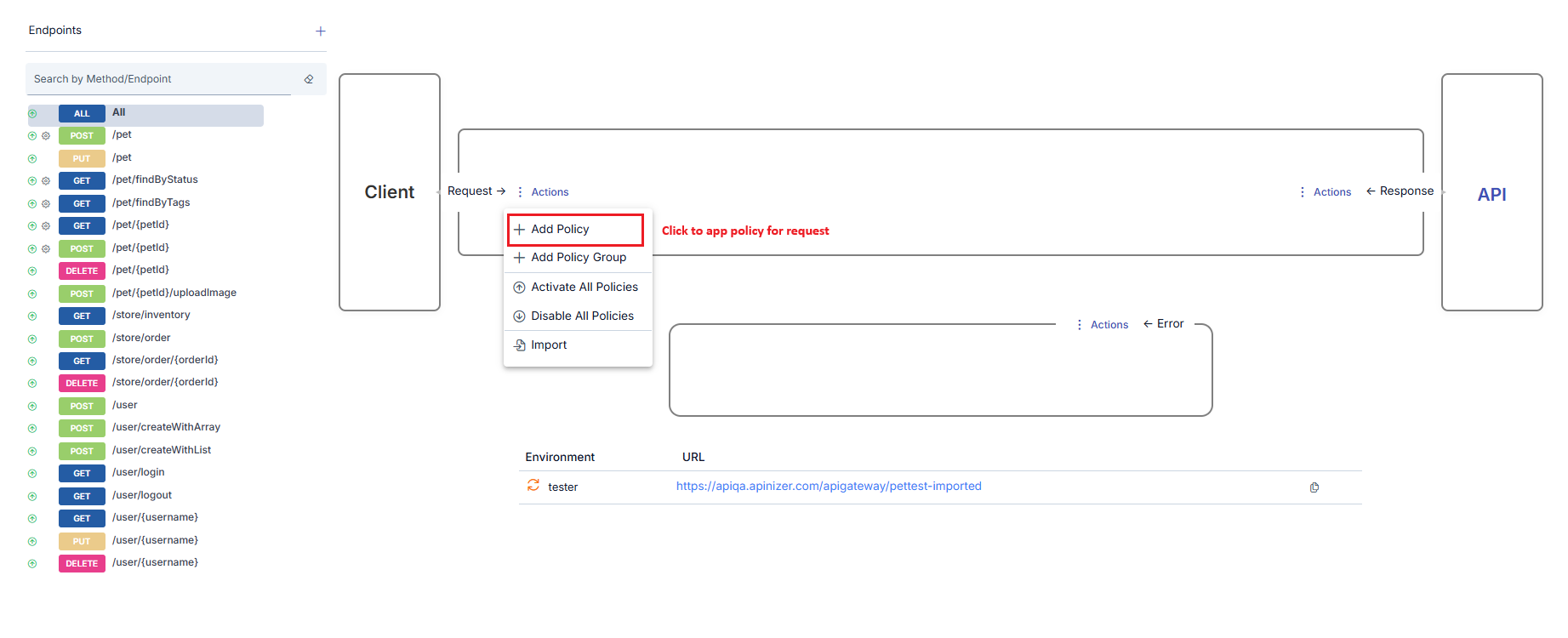

Policy Type Selection
The type of policy to be added is selected from the opened window. Policy types shown in this window vary according to the active API Proxy’s type and which area the policy is to be added to.

Policy Configuration
When the policy to be added is selected, a window opens where configuration information for that policy can be entered. Policies can be added in different ways from this window: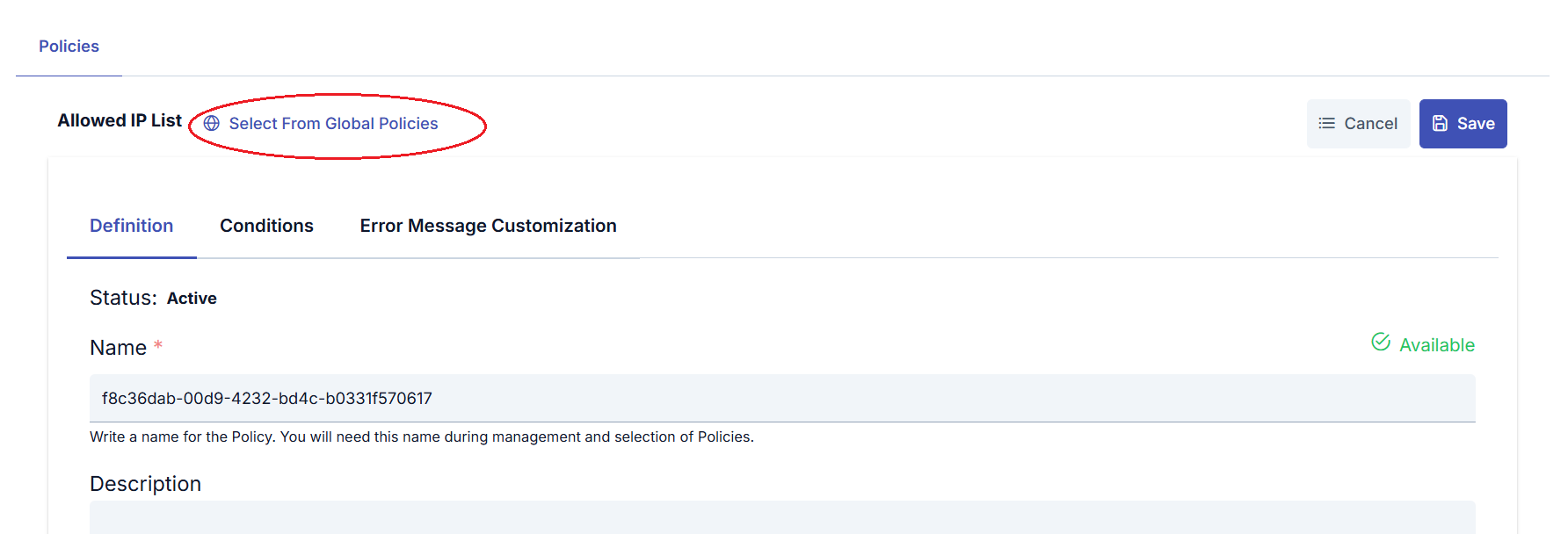
- To add an existing global policy: In the policy window, click the Select From Global Policies link next to the policy type at the top. The appropriate policy is selected from the opened window and the process is completed.

- To create a local policy: A local policy is created with the data entered in the opened window without any special operation.
Updating Policy in Flow
When an existing policy’s icon is clicked, a window opens where that policy’s information can be updated.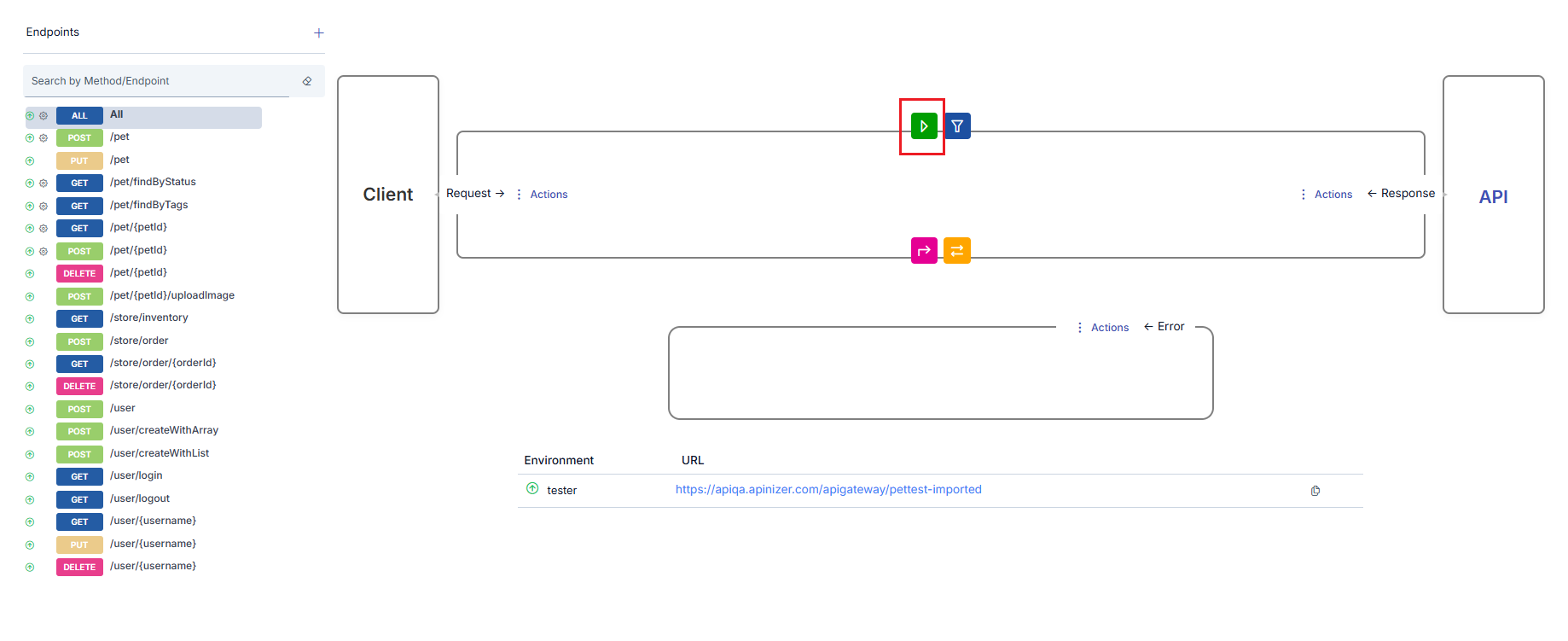
Activating/Deactivating Selected Policy
A policy can be temporarily removed from use without being deleted from the method/endpoint or API Proxy where it was added. For this, the policy is opened for update and the Deactivate button at the top of the opened window is clicked.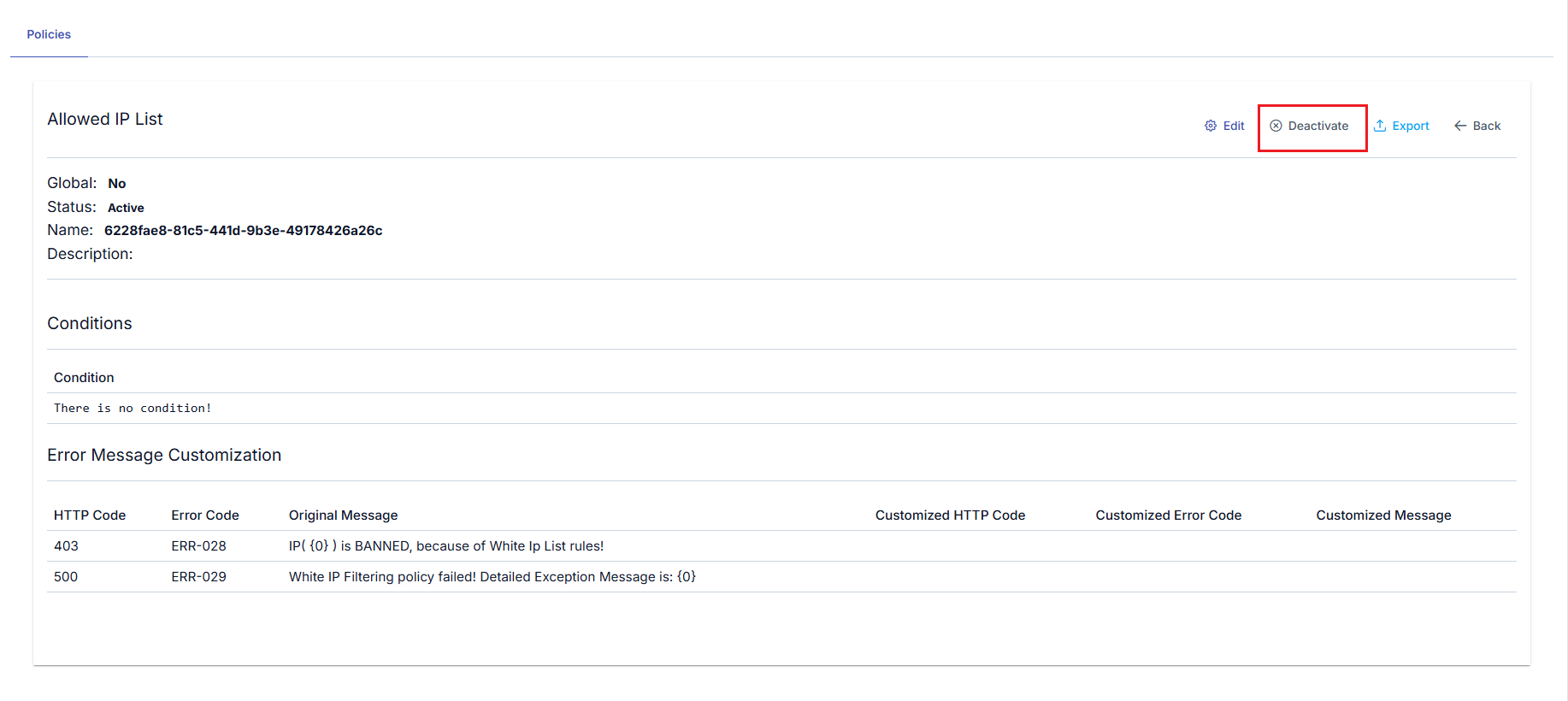
Activating/Deactivating All Policies
In the method/endpoint section, the Disable All Policies link appears at the bottom of the middle section. When this link is clicked, if All option is selected, all policies added to the API Proxy; if in any method, only all policies added within that method are disabled. Disabled policies can be reactivated individually from the policy update window later or collectively by clicking the Activate All Policies link.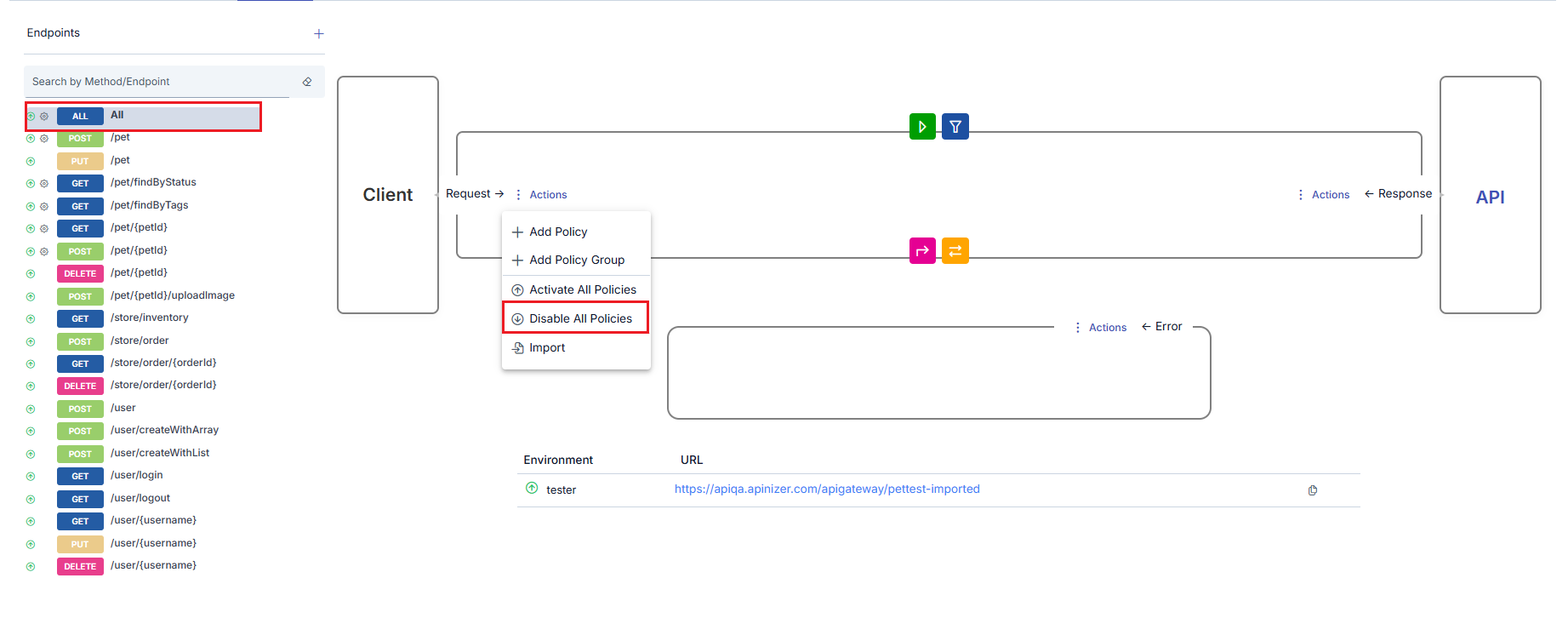
Removing Policy from Flow
When the mouse is hovered over the policy to be deleted, an icon appears that will delete the policy. The policy can be deleted by clicking this icon.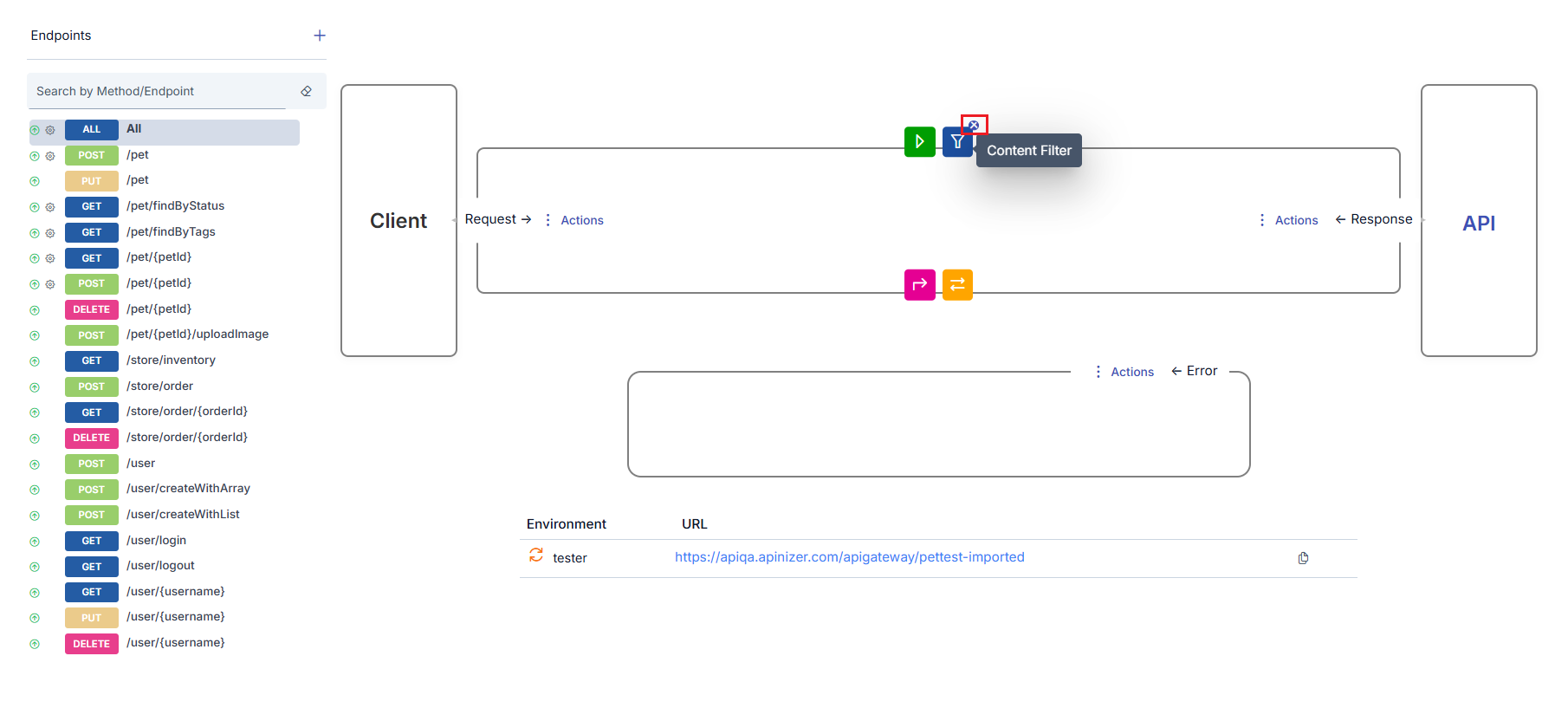
Policy Application Examples
Example 1: Simple Message Processing
Request
GET /api/v1/products
1. Pre-flow: OAuth2 Authentication
✓ Successful
2. Pre-flow: Rate Limiting
✓ Successful
3. Route: Routing to backend
Request is sent to Backend API
4. Post-flow: Response Logging
✓ Successful
Response
200 OK
Example 2: Conditional Policy Application
Request
POST /api/v1/products
1. Pre-flow: OAuth2 Authentication
✓ Successful
2. Conditional Policy
Based on Content-Type header:
- If
application/json→ JSON Schema Validation ✓ - If
application/xml→ XML Schema Validation ✓
3. Route: Routing to backend
Request is sent to Backend API
4. Post-flow: Response Transformation
✓ Successful
Response
201 Created
Example 3: Policy Application in Error Condition
Request
GET /api/v1/products
1. Pre-flow: OAuth2 Authentication
✗ Token invalid
2. Fault Handler Policy
- Error Response Transformation
- Error Logging
Response
401 Unauthorized
Best Practices
Request Pipeline
Request Pipeline
- Run security policies first
- Leave heavy operations last
- Perform validation before transformation
- Optimize conditional policies
Response Pipeline
Response Pipeline
- Do data masking first
- Do transformation afterwards
- Leave logging last
- Consider performance
Error Pipeline
Error Pipeline
- Catch all errors
- Create user-friendly error messages
- Mask sensitive information
- Perform detailed logging

