- Security Manager in Apinizer requests Plain-Text type authentication information from API Client.
- Authentication information is sent to be checked via LDAP.
- LDAP returns a response to Apinizer regarding authentication information. If this authentication is correct, the flow continues.
- Apinizer makes a request to Backend API.
- Backend API responds to Apinizer.
- Apinizer responds to API Client.

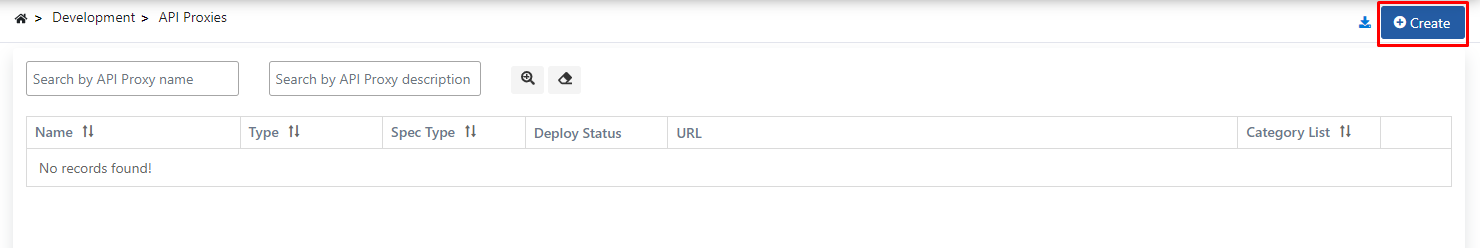
Creating API Proxy

Since no proxy definition has been made before on the opened page, the text No records found! appears.
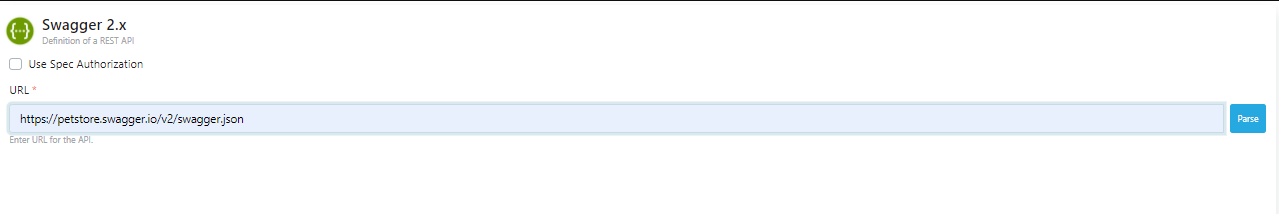
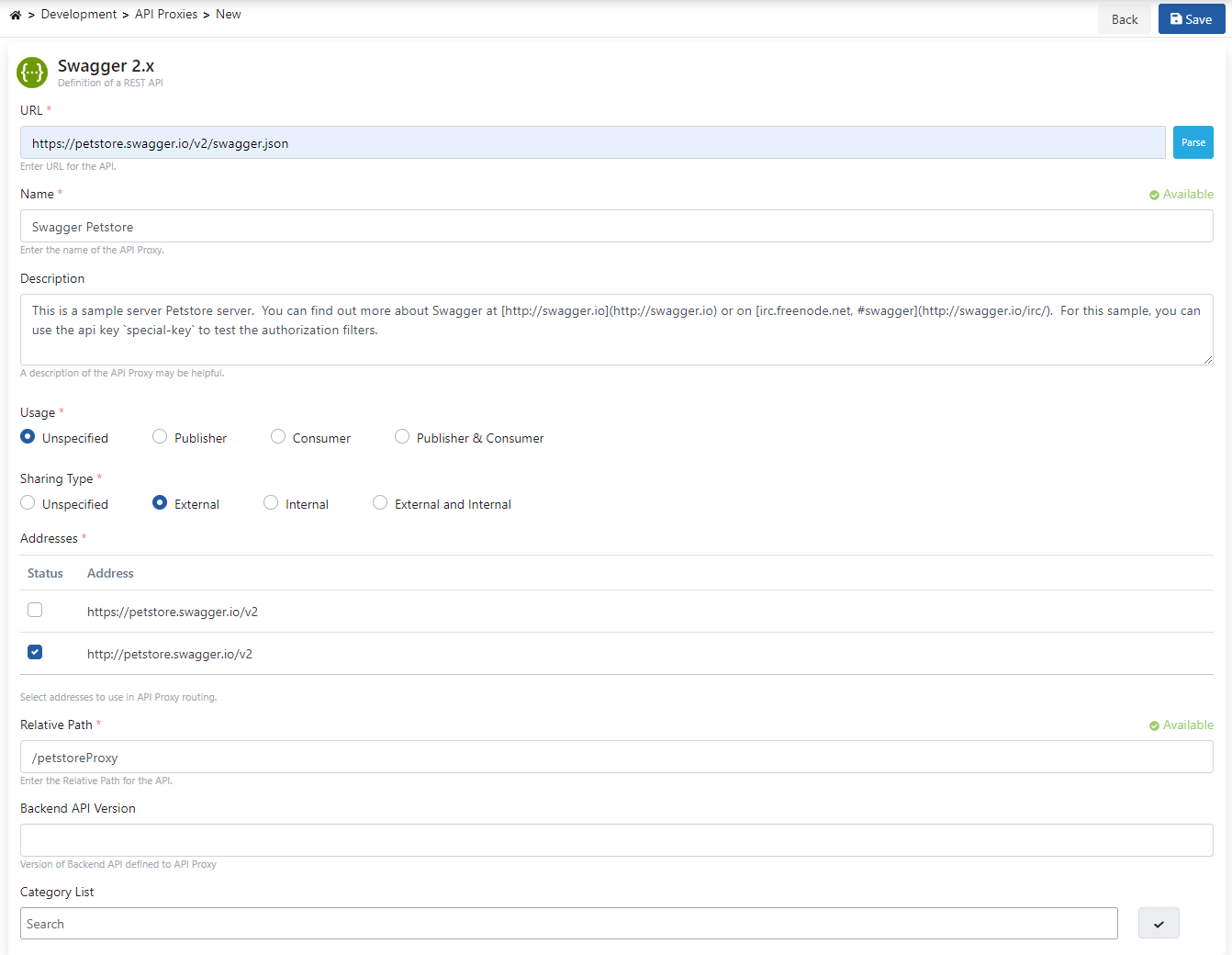
- The Usage field specifies who will use the created API Proxy. Options such as publisher, consumer, publisher and consumer are available here.
- The Sharing Type field specifies the sharing type of the created API Proxy. Options such as external, internal, external and internal are available here.
- One or both of the two API addresses under the Addresses tab can be selected. If both addresses are selected, Apinizer will perform the Load Balance operation itself.
- Relative Path is the address where the created API Proxy will be opened for access.
- The Category List field also allows categorization of the created API Proxy.
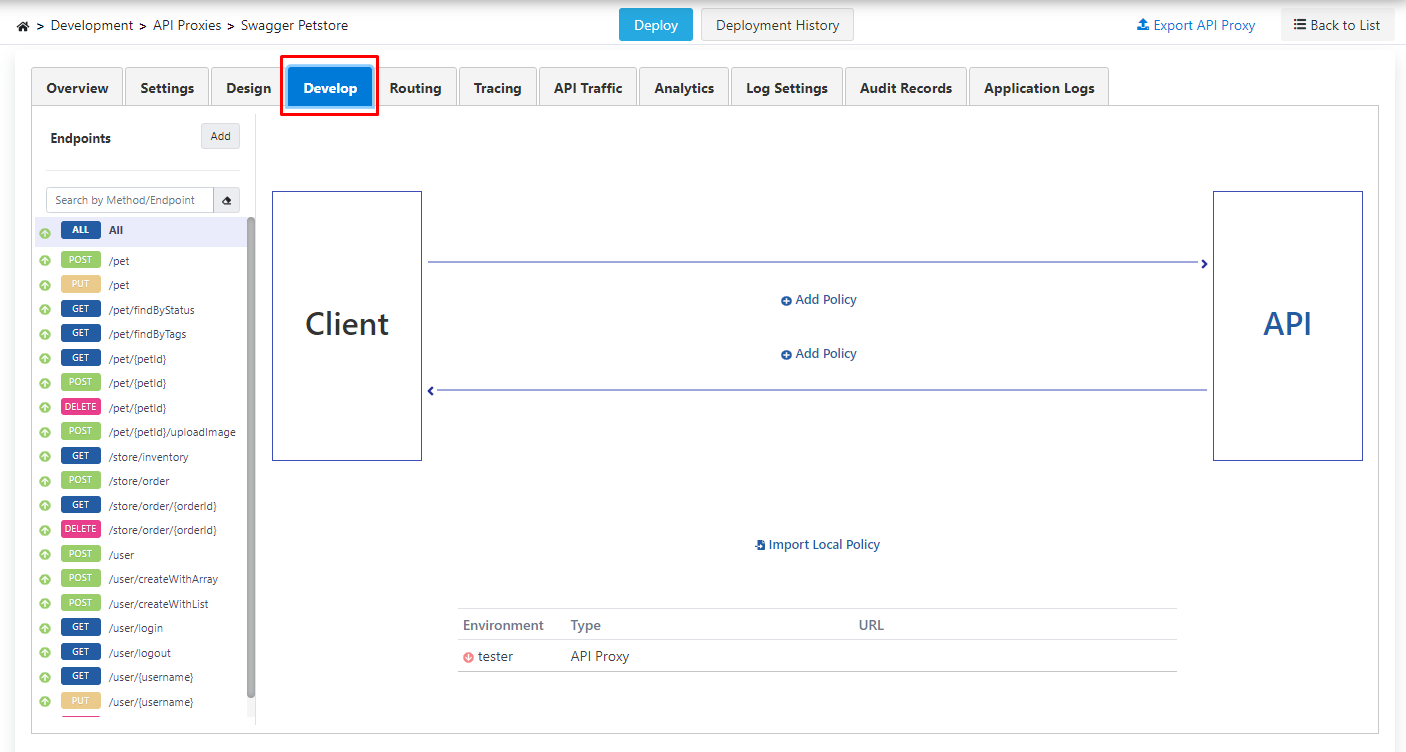
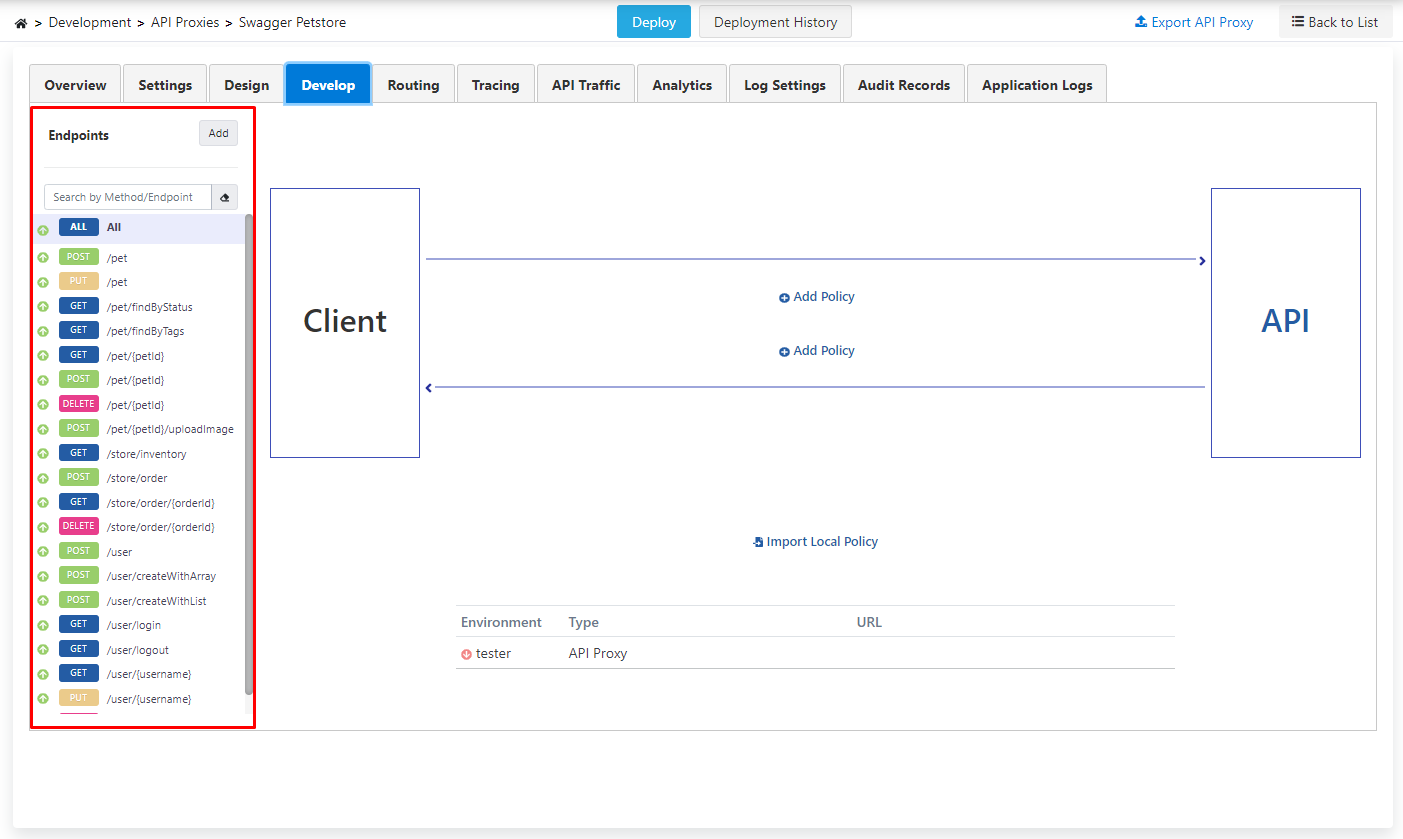
Policies to be added with the All expression above these endpoints can be applied to all endpoints.
Establishing LDAP/Active Directory Connection
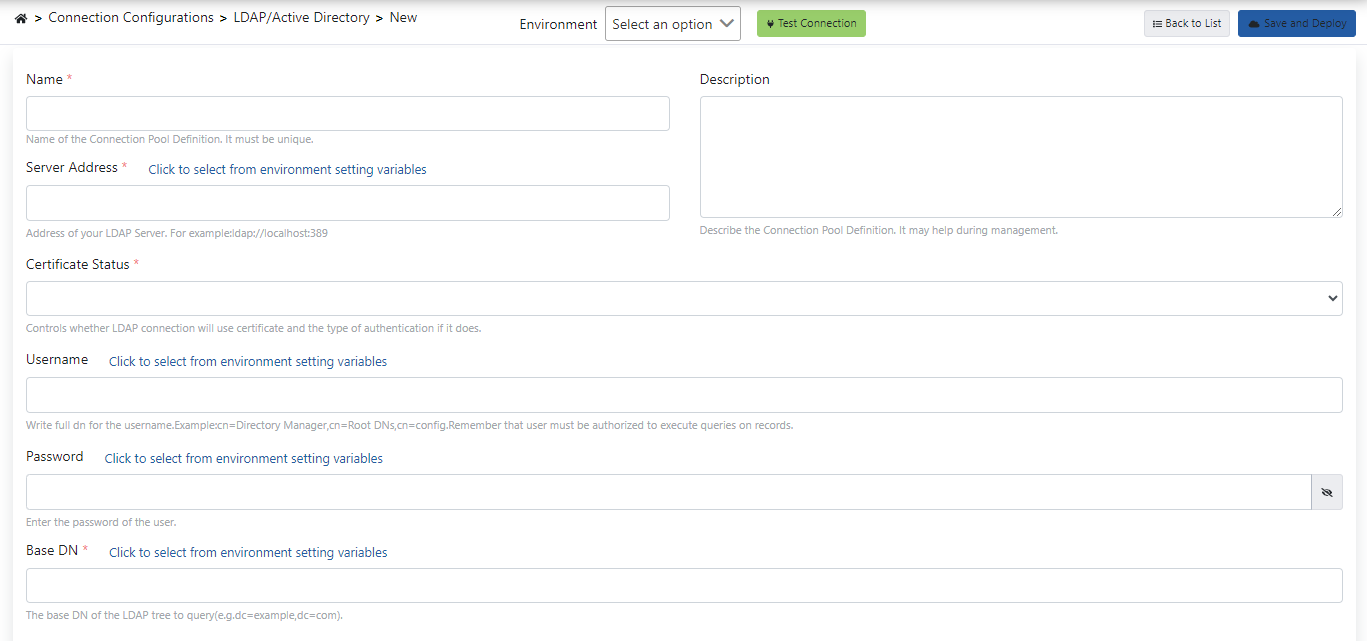
Click the LDAP/Active Directory menu under the Connection Management menu.Since no LDAP/Active Directory definition has been made before, the text There is no LDAP/Active Directory appears on this page.

- The Name field expresses the name of the connection to be created.
- The Server Address field writes the address of the LDAP/Active Directory server to be connected to.
- A description can be added to the created connection with the Description expression.
- The Certificate Status field selects or creates a new certificate required for LDAP connection.
- The Username field enters the username information to be used during connection, and the Password field enters the password to be used during connection.
- The Base DN field also specifies the base dn address of the LDAP to be connected to.


Creating Authentication Policy
Go to the page where API proxies are listed and select the proxy named Swagger Petstore from here. Go to the Develop tab and click the Add Policy button. On the opened page, the Plain-Text Authentication policy is selected.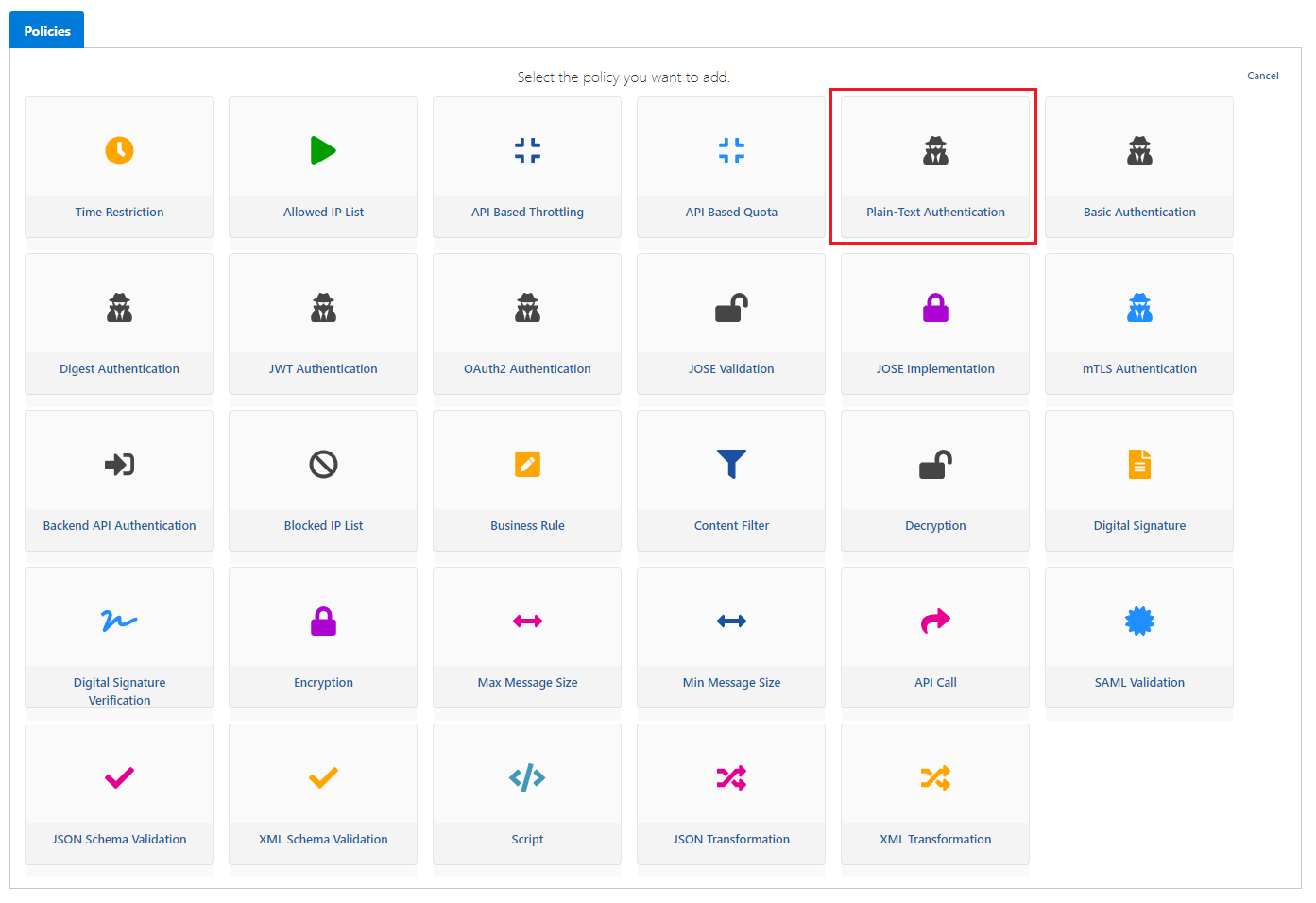
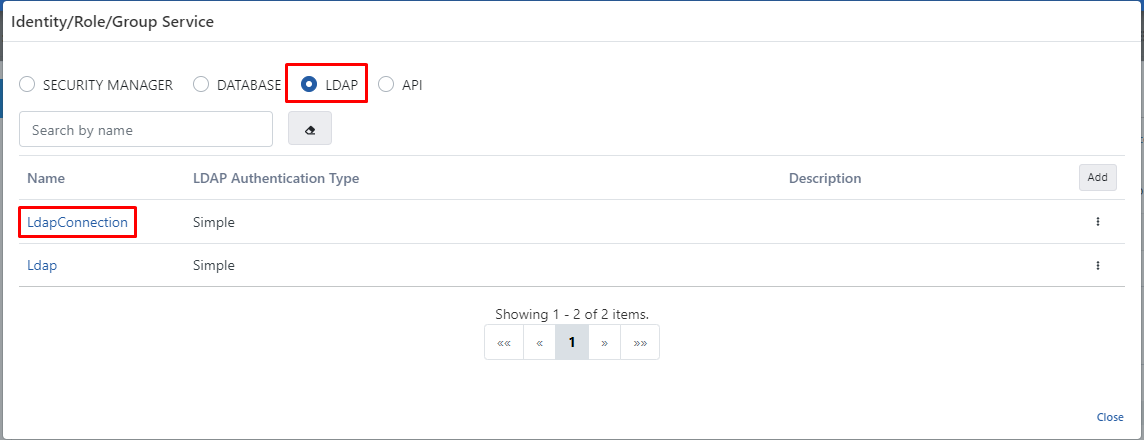
- The value to be selected in the Identity/Role/Group Service field is the LDAP value. Because authentication control will be performed by the structure in LDAP/Active Directory.
- When the LDAP value is selected, the previously created LDAP connection must be selected.
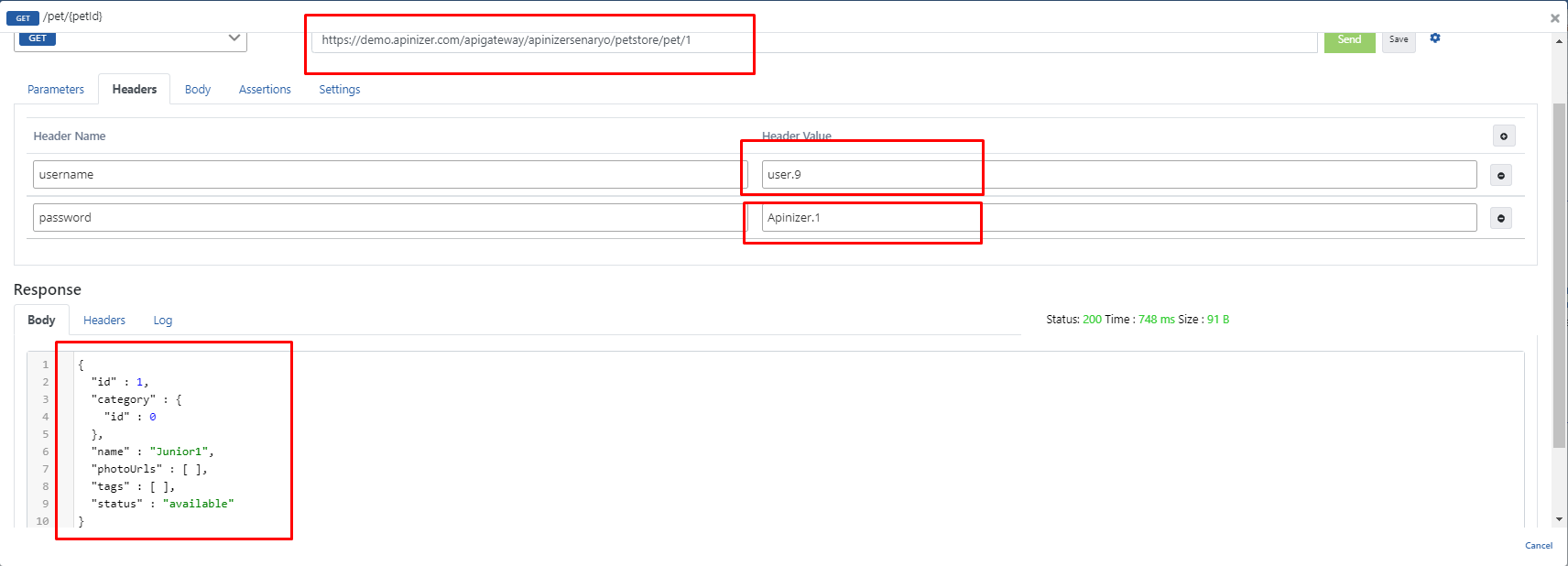
- The Variable for username and variable for password expressions also select which variable the username and password information will be retrieved with. In this scenario, these values will be retrieved from header.
- The Add Client Info To Header option specifies whether client information will be present in the Header going to the backend API.
- If this option becomes active, another parameter named Authenticated User Header Name appears.
- The X-Authenticated-UserId expression here specifies the header name with which the client information going to the backend API will go.
The relevant icon is seen when the policy is registered.
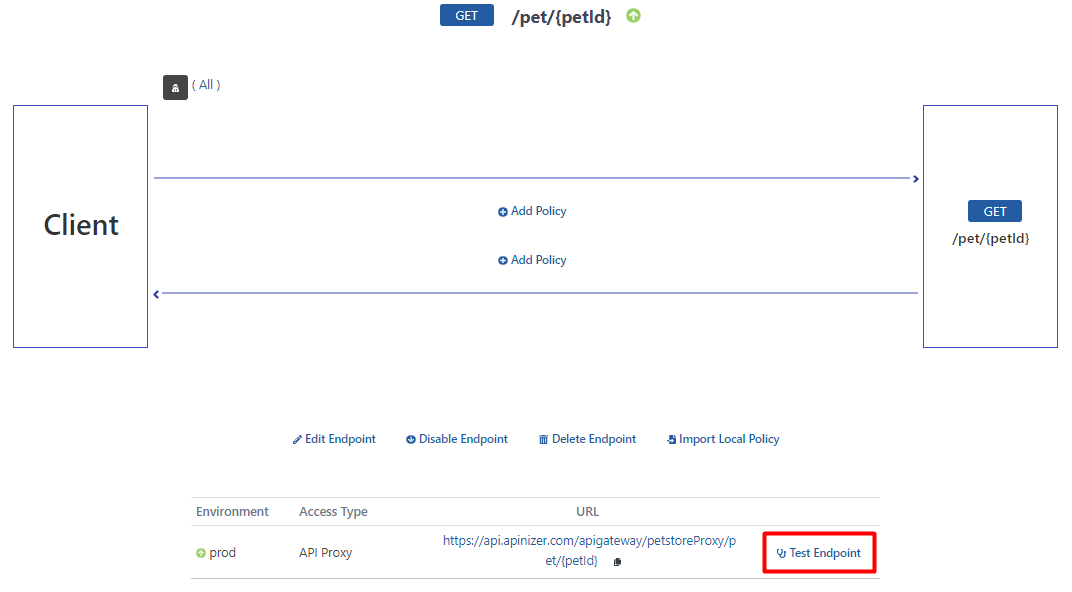
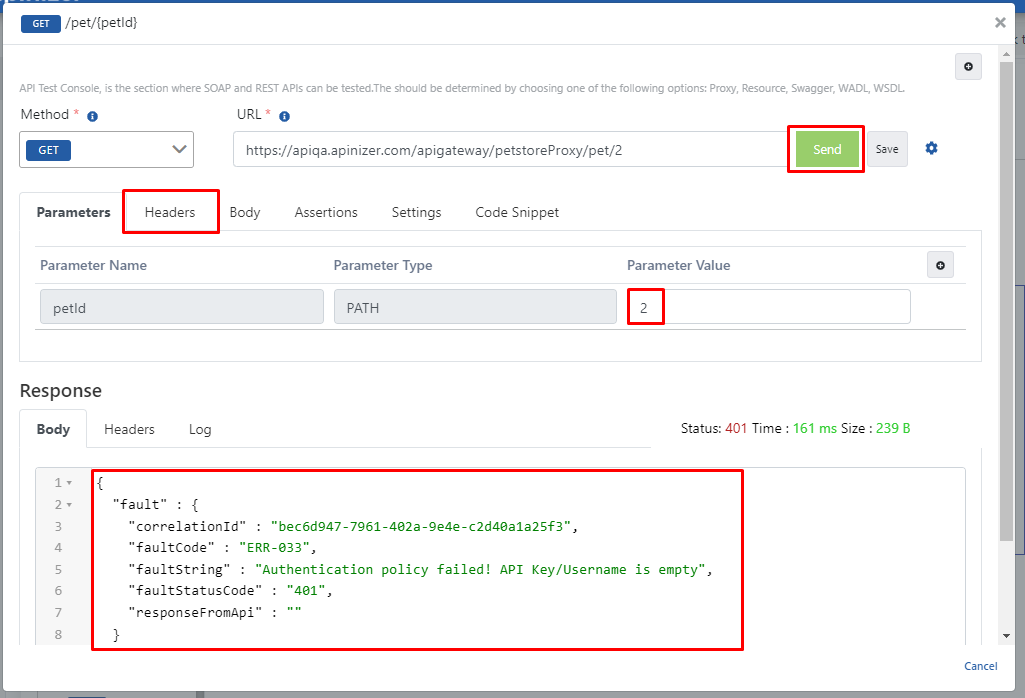
Testing the API Proxy
After selecting the “/pet/” endpoint, click the Test Endpoint button.