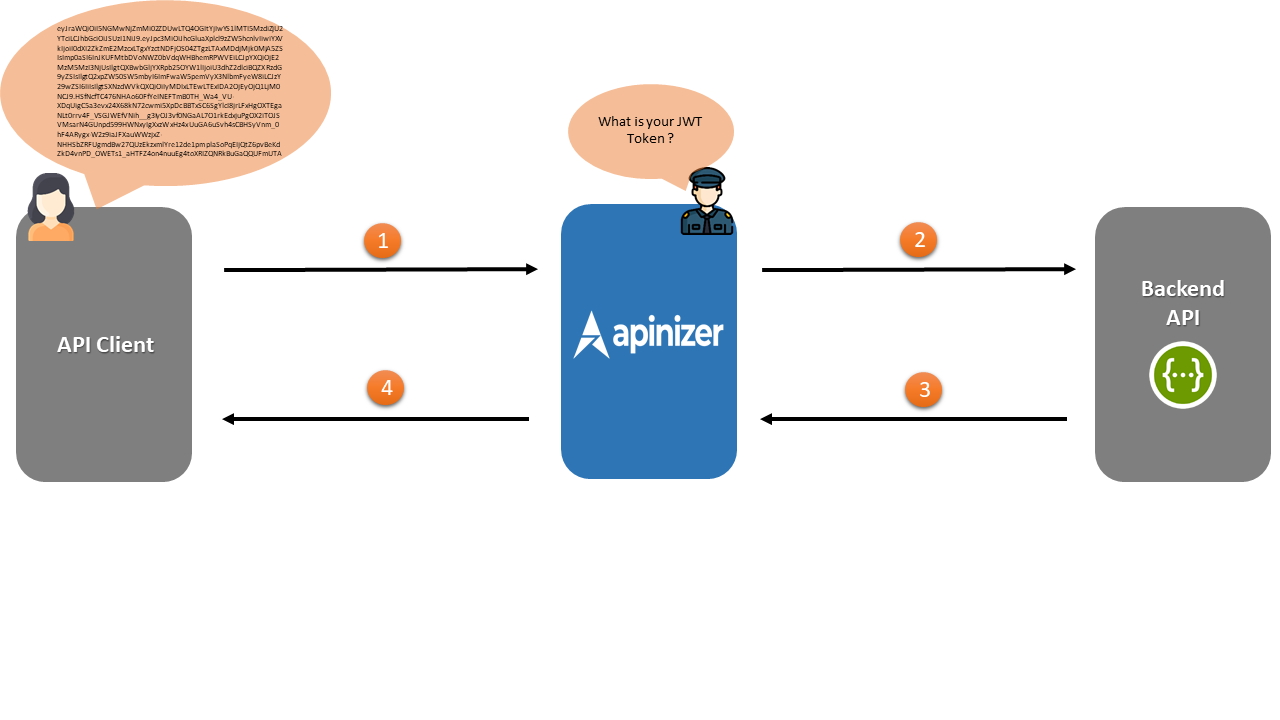
- Security Manager in Apinizer requests JWT type authentication information from API Client. If this authentication is correct, the flow continues.
- Apinizer makes a request to Backend API.
- Backend API responds to Apinizer.
- Apinizer responds to API Client.
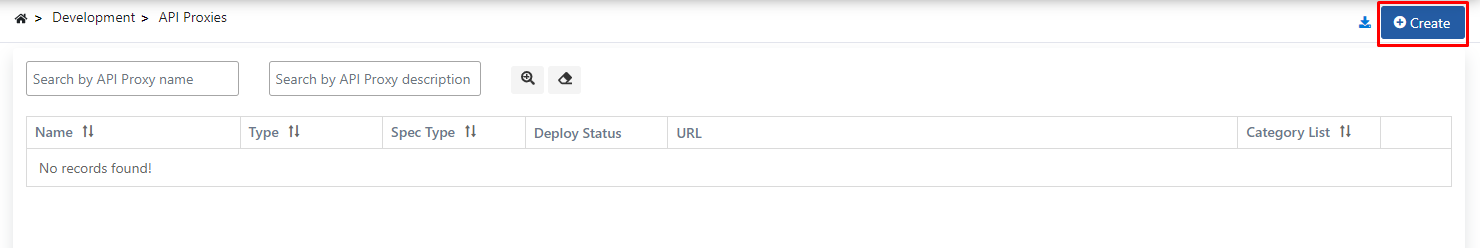
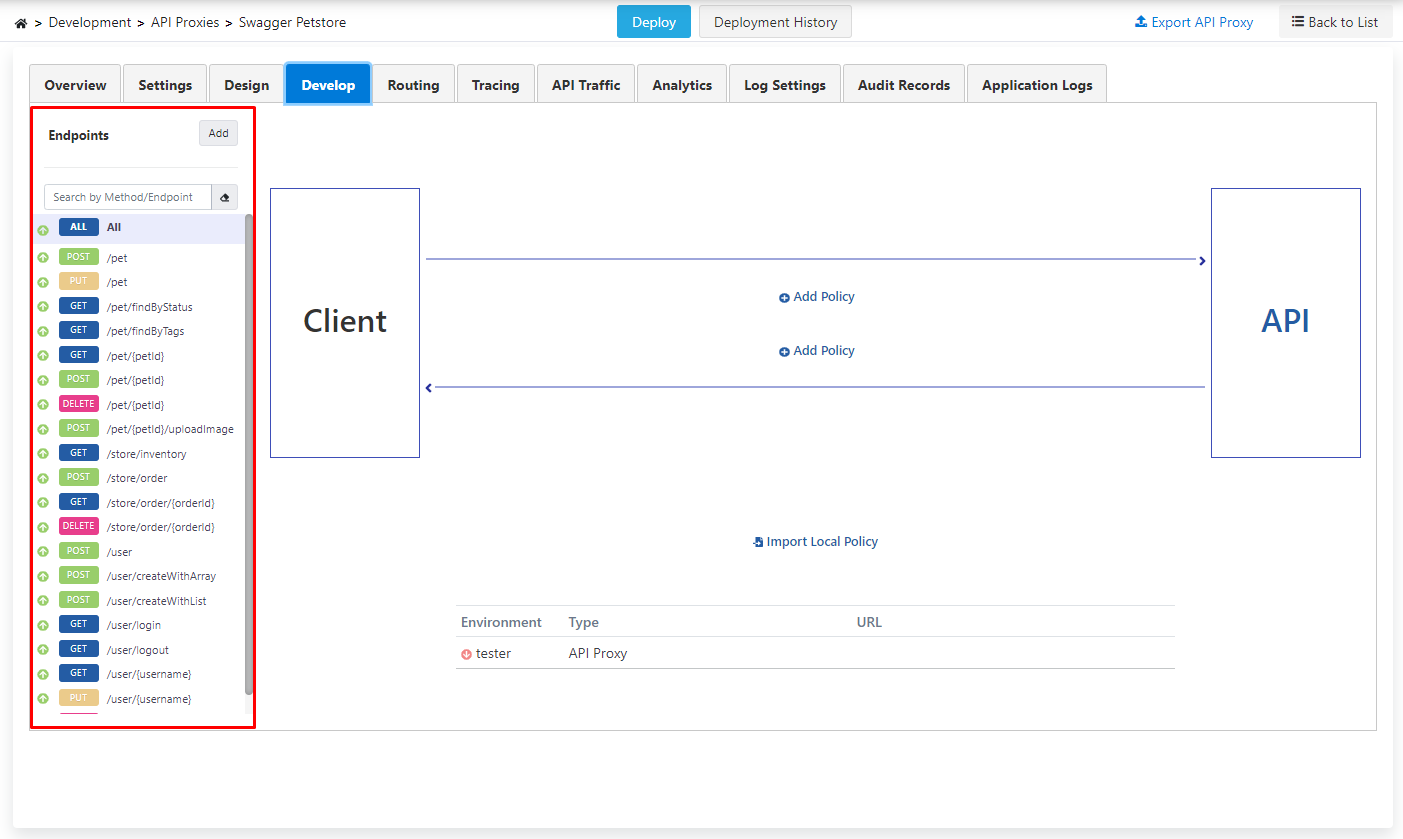
Creating API Proxy

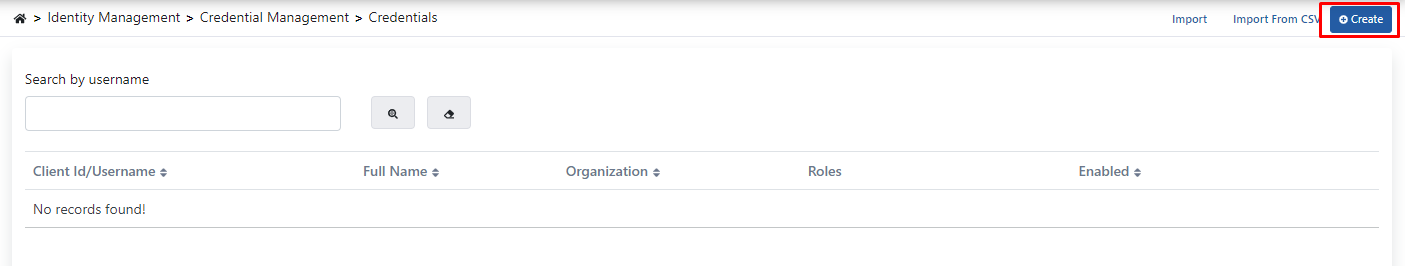
Since no proxy definition has been made before on the opened page, the text No records found! appears.
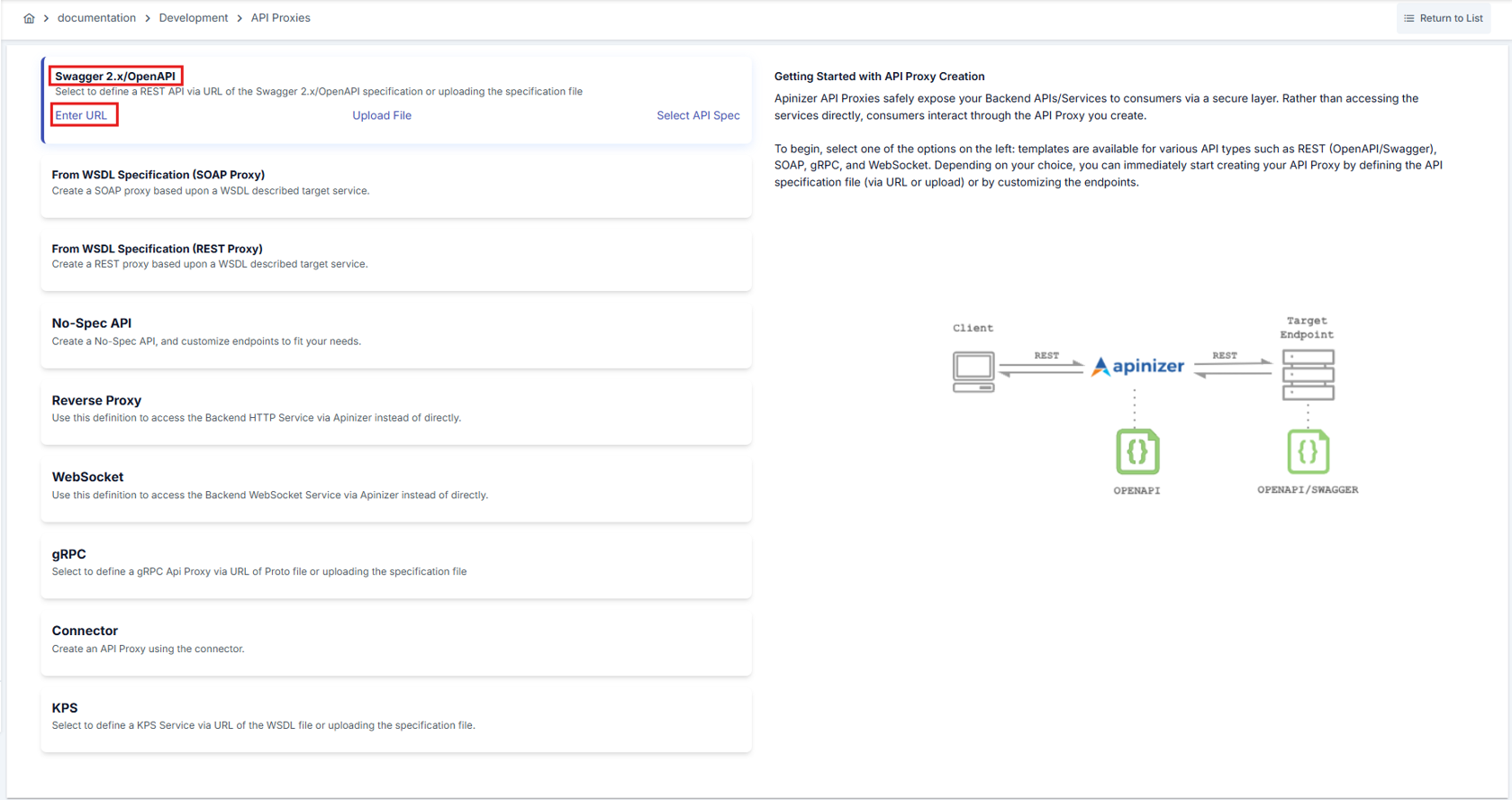
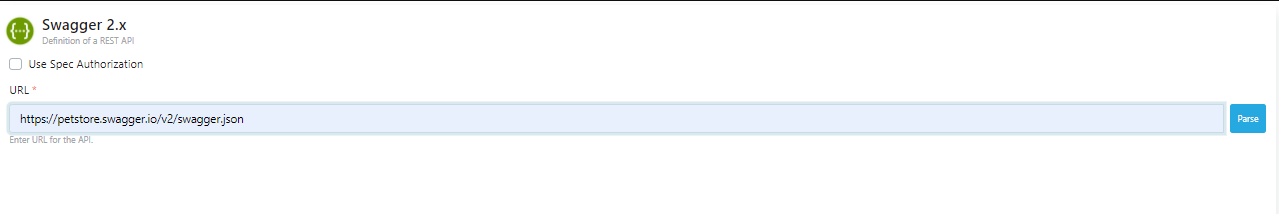
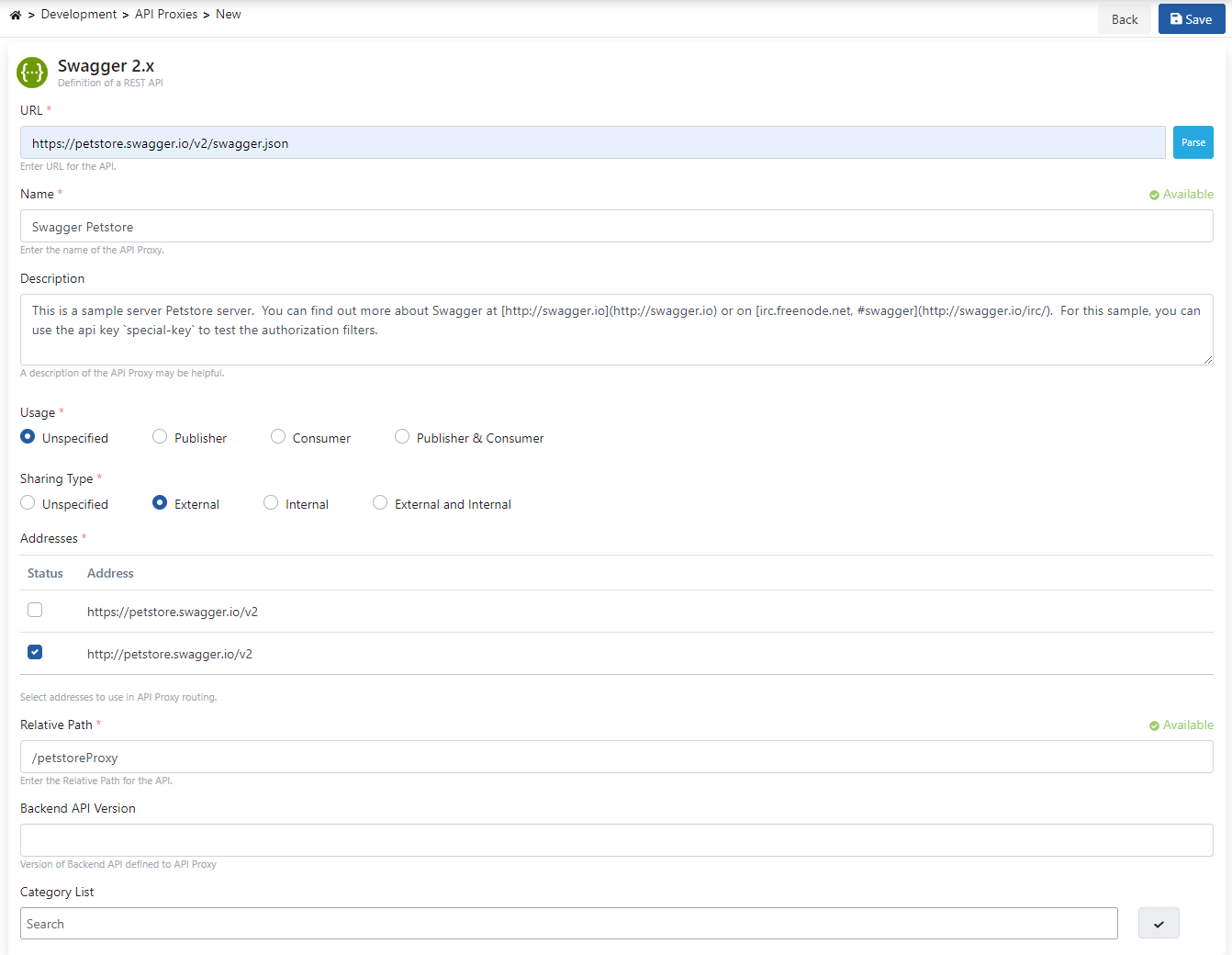
- The Usage field specifies who will use the created API Proxy. Options such as publisher, consumer, publisher and consumer are available here.
- The Sharing Type field specifies the sharing type of the created API Proxy. Options such as external, internal, external and internal are available here.
- One or both of the two API addresses under the Addresses tab can be selected. If both addresses are selected, Apinizer will perform the Load Balance operation itself.
- Relative Path is the address where the created API Proxy will be opened for access.
- The Category List field also allows categorization of the created API Proxy.
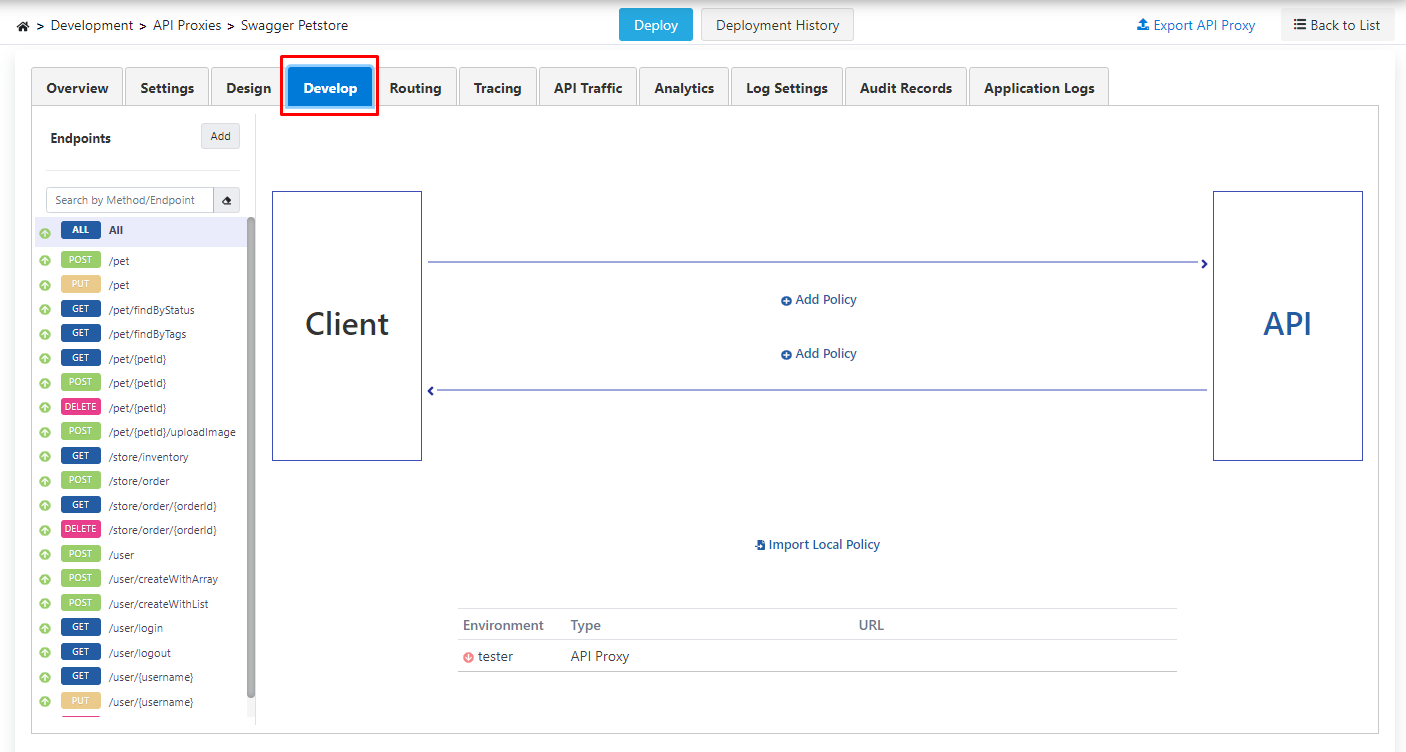
Policies to be added with the All expression above these endpoints can be applied to all endpoints.
Creating Credentials
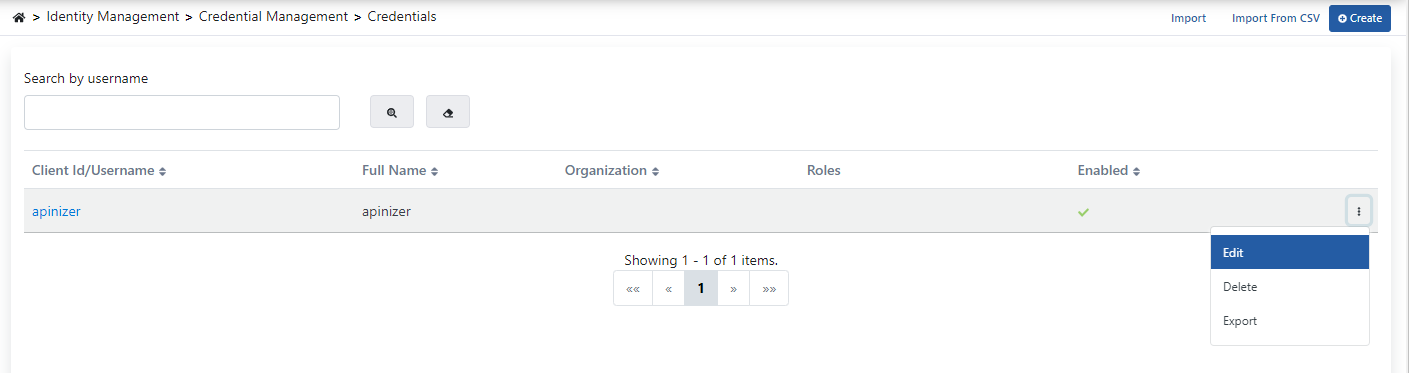
The information for the Credential to be added will be username = apinizer, password = 123123aA. For this, go to the Identity Management menu. Here, click the Credentials menu under the Credential Management menu.

Adding Authentication Policy
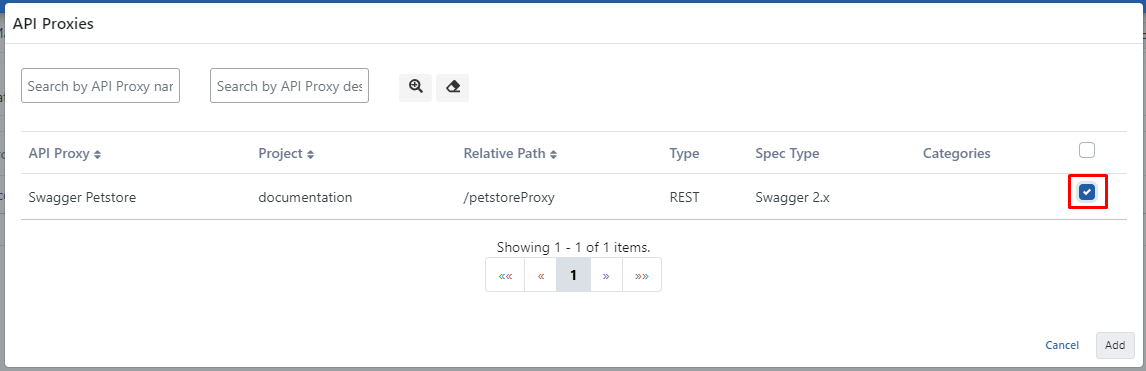
The JWT Authentication policy can now be added. Go to the page where API Proxies are listed and select the proxy named Swagger Petstore from here. Then go to the Develop tab and click the Add Policy button. On the opened page, the JWT Authentication policy is selected.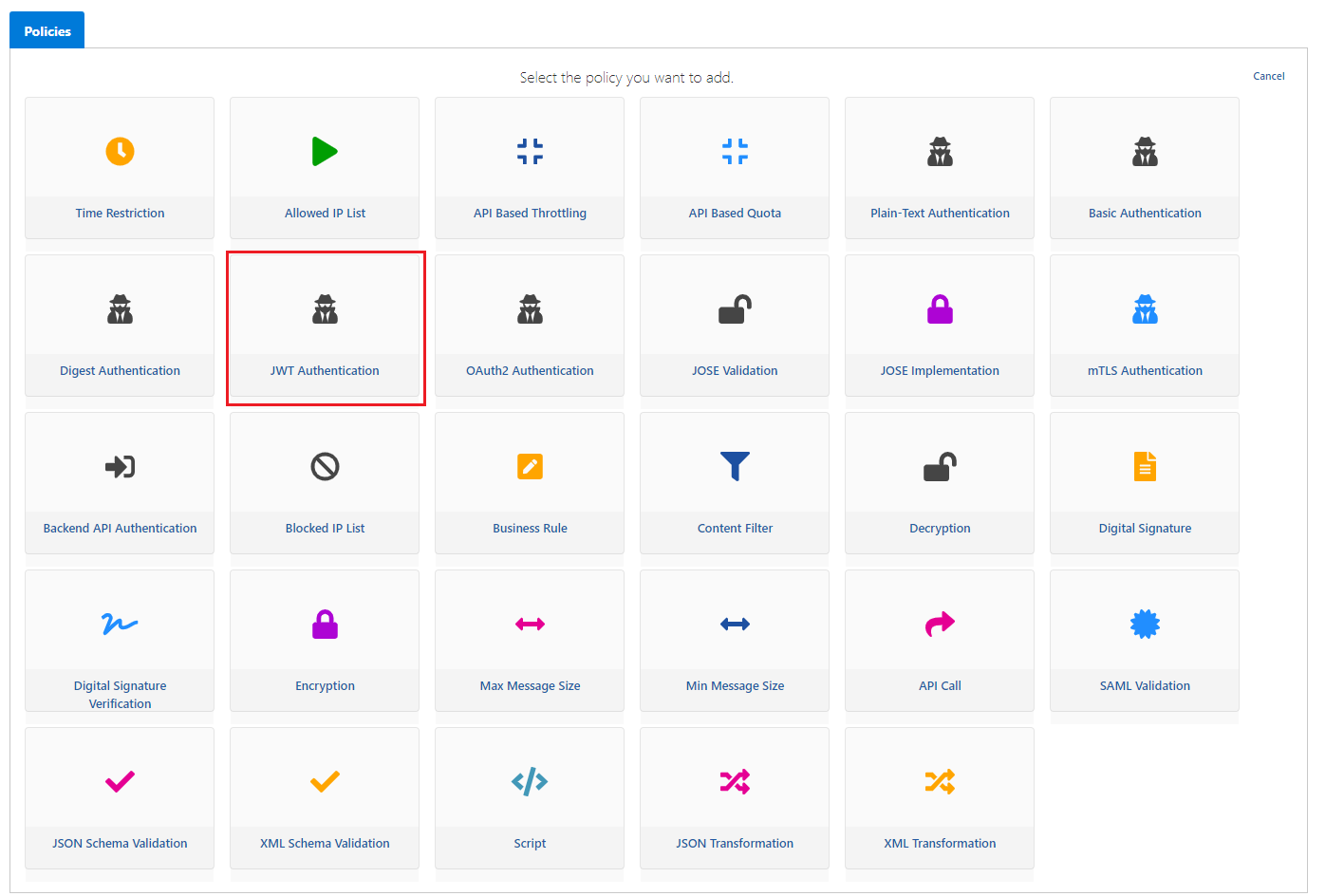
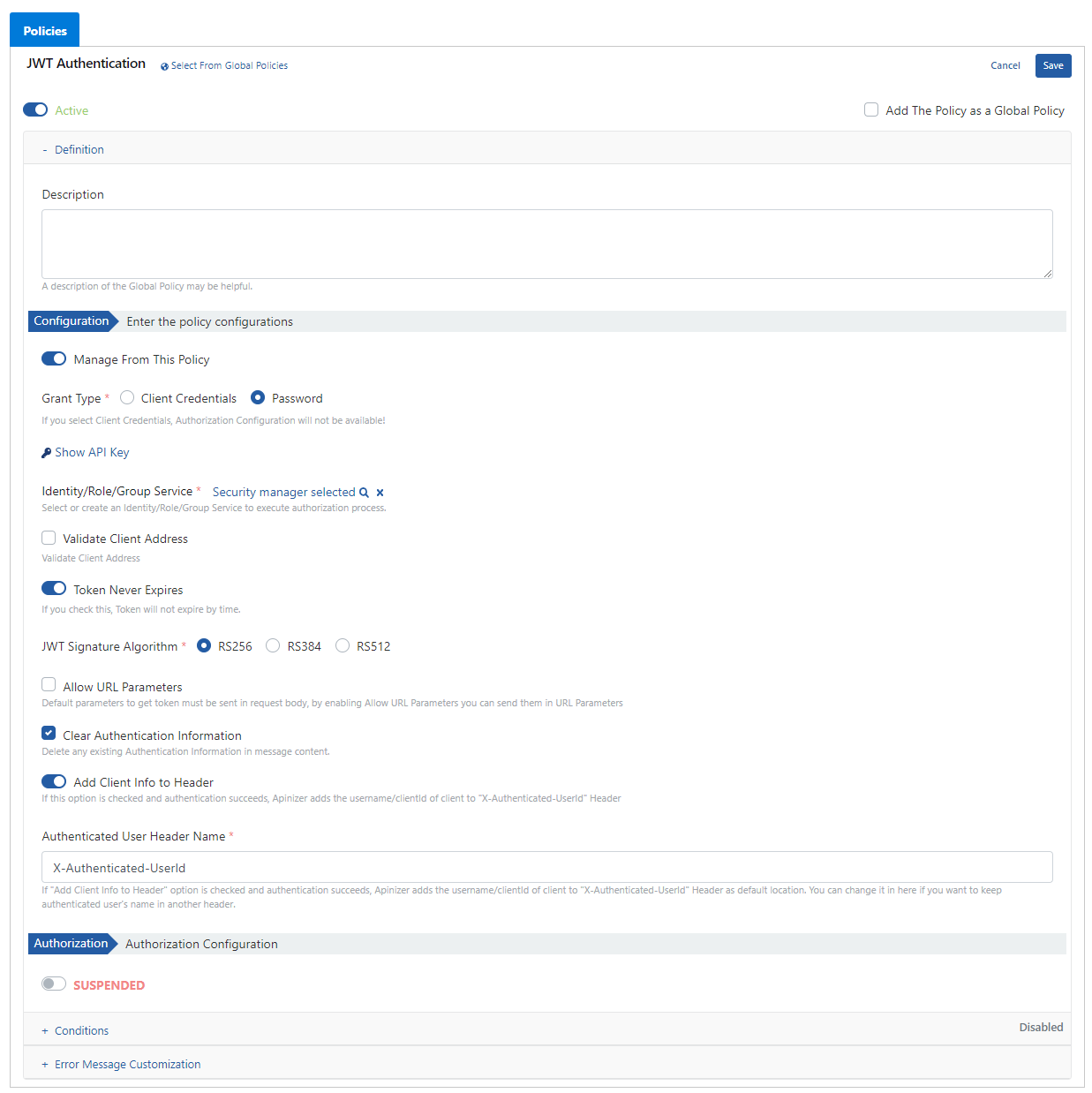
- The Grant Type field specifies how user information of the token service to be used will be verified. If the Client Credentials expression is selected, (Identity/Role/Group) Service cannot be used.
- The Show API Key field displays the API proxy key values belonging to the created proxy.
- With the Token Never Expires field, no time value is assigned to the created token and it can be used as desired. If this option is not selected, a menu appears immediately below as shown in the image below.
- The Token Expires In field specifies how long the token will be valid. This specification can be adjusted with time expressions in the dropdown menu.
- The Refresh Token Allowed field activates the renewal feature of the created token. If this option is selected, a field appears for setting how many times it can be renewed, and the image for this field is shown below.
- Refresh Token Count specifies how many times the token can be renewed.
- The Refresh Token Expires In field specifies the lifetime of the renewed token.
- The JWT Signature Algorithm field specifies which algorithm will be used to generate the token to be produced.
- The Allow URL Parameters field allows information to be sent only in the message body when a request is sent for token generation. If this information is desired to be sent as “URL Parameter”, this option must be selected, but this situation will create a security risk and is not recommended.
- With the Add Client Info to Header field, when authentication is successfully performed, it sends the authorized username to the backend API by placing it in the header. When this option is checked, an input field containing X-Authenticated-UserId appears immediately below. This field is the default name of the header information.

Creating Token for Authentication
The Public Key information belonging to the relevant proxy is obtained from the Show API Key option in the JWT Authentication policy.


- Select the method type from the Method field.
- Write the address where the token will be received in the URL field.
- Since the message content will be in the body section, select the body expression from the tab below.
- Write the values required to obtain the token here and click the Send button.


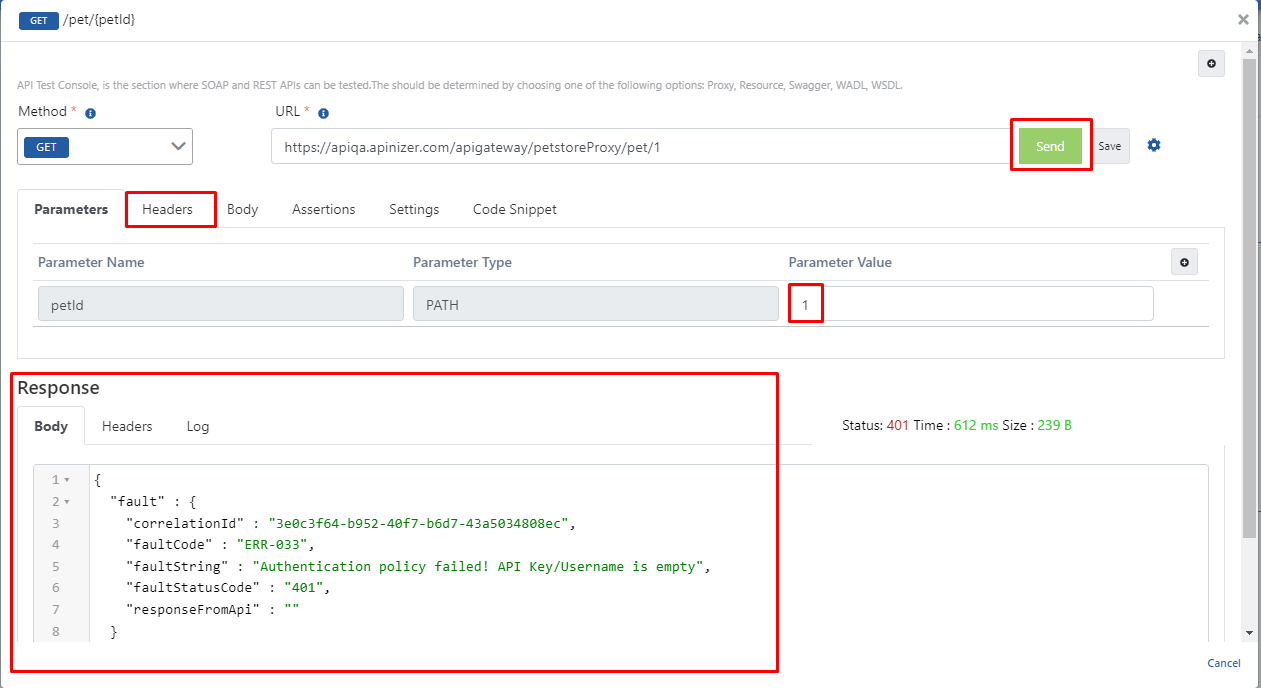
Testing the API Proxy
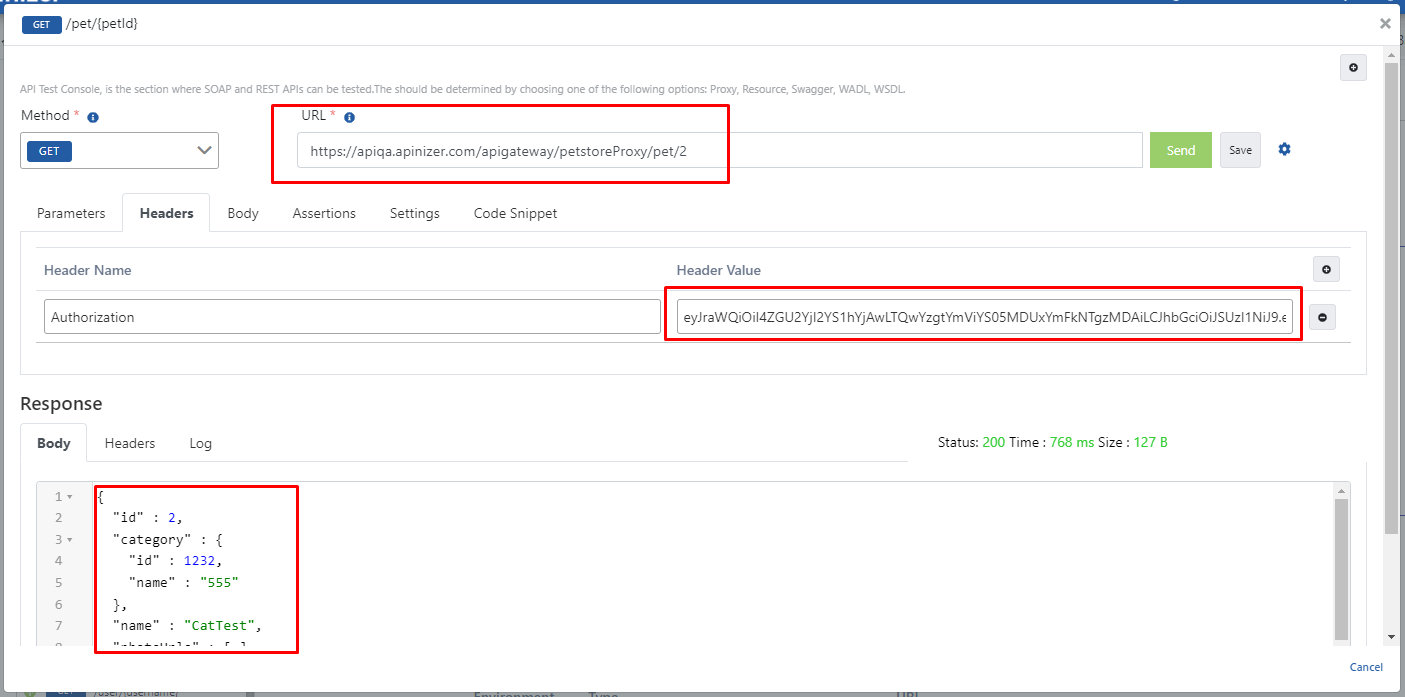
Select the proxy named Swagger Petstore. Select the endpoint named “/pet/” under the Develop tab. Click the Test Endpoint expression to test this endpoint. Enter the desired petId value as “1” in the URL, and when the Send button is pressed, it is seen that the returned response is an error message.