Overview
What is its Purpose?
What is its Purpose?
Centralized Log Collection
Disk Consumption Control
Environment-Based Separation
Security and Permission Management
Working Principle
Working Principle
Connection Initiation
Connection Pool Management
Authentication
Data Communication
Connection Management
Error Management
Use Cases
Use Cases
API Proxy Traffic Logging
Request/Response Tracking
Log Retention Policies
Security Reviews
Technical Features and Capabilities
Basic Features
Basic Features
Log Directory Management
File Naming Patterns
Storage Limit Control
Environment-Based Configuration
Enable/Disable Control
Advanced Features
Advanced Features
Instant Test Support
Name Conflict Prevention
Move to Global
Connection Test Feature
Export/Import Feature
Connection Monitoring
Connection Parameters
Required Parameters
Required Parameters
Name
Example Value:
Production_LogbackNotes: Cannot start with space, special characters should not be used
Log Path (logPath)
Example Value:
/var/log/apinizer/Notes: Worker pod must have write permission, absolute path recommended
Log File Name (logFileName)
Example Value:
ApinizerApiProxyTrafficNotes: Use of letters, numbers, and
_ recommendedLog Filename Pattern (logFilenamePattern)
Example Value:
%d{yyyy-MM-dd}.%i.logNotes: Logback patterns supported, date format required
Log Pattern (logPattern)
Example Value:
%d{yyyy-MM-dd HH:mm:ss.SSS}[%t]%nNotes: All compatible with Logback conversion patterns
Max File Size (maxFileSize)
Example Value: 25
Notes: Positive integer, 1-1024 MB range recommended
Max History (maxHistory)
Example Value: 30
Notes: 0 means unlimited but disk may grow
Total Size Cap (totalSizeCap)
Example Value: 1024
Notes: If 0, Logback does not apply total limit; >512 MB recommended for Production
Optional Parameters
Optional Parameters
Description
Default Value: ”
Recommended Value: Short description indicating function and target system
Environment (environmentId)
Default Value: null
Recommended Value: Separate value selection recommended for each environment
Log Pod Name (logPodName)
Default Value: ”
Recommended Value: Use when need to write only to target pod in multi-node clusters
Deploy To Worker (deployToWorker)
Default Value: true
Recommended Value: false if kept for test purposes only on management node
Enable Status
Default Value: true
Recommended Value: Always active in Production, can be temporarily closed while resolving issues
Timeout and Connection Pool Parameters
Connection Timeout
Default: Not applicable
Min: - | Max: -
Unit: milliseconds
Request Timeout
Default: Not applicable
Min: - | Max: -
Unit: milliseconds
Pool Size
Default: Not applicable
Min: - | Max: -
Unit: count
Flush Interval
Default: 1000
Min: 250 | Max: 5000
Unit: milliseconds
Use Cases
API Proxy Traffic Monitoring
Solution: logPath=/var/log/apinizer/proxy, maxHistory=30, totalSizeCap=2048
Expected Behavior: All calls stored with 30-day history, readable by SIEM
Security Incident Review
Solution: logFilenamePattern=
%d{yyyy-MM-dd}-security.%i.logExpected Behavior: Date-based files quickly filtered, review performed within incident period
Integration Tests
Solution: environmentId=Test, maxFileSize=10
Expected Behavior: Test logs split into small files, developers easily download
Pod-Based Separation
Solution: logPodName=gateway-worker-2
Expected Behavior: Logs taken only from relevant pod, target problem isolated
Regulatory Archiving
Solution: maxHistory=0, totalSizeCap=5120
Expected Behavior: Legal retention period provided with total quota instead of infinite cycle
Disaster Recovery
Solution: logPath=/mnt/dr/logs, Enable Export All on
Expected Behavior: All logs written to shared storage in failover scenario
Connection Configuration
Creating New Logback
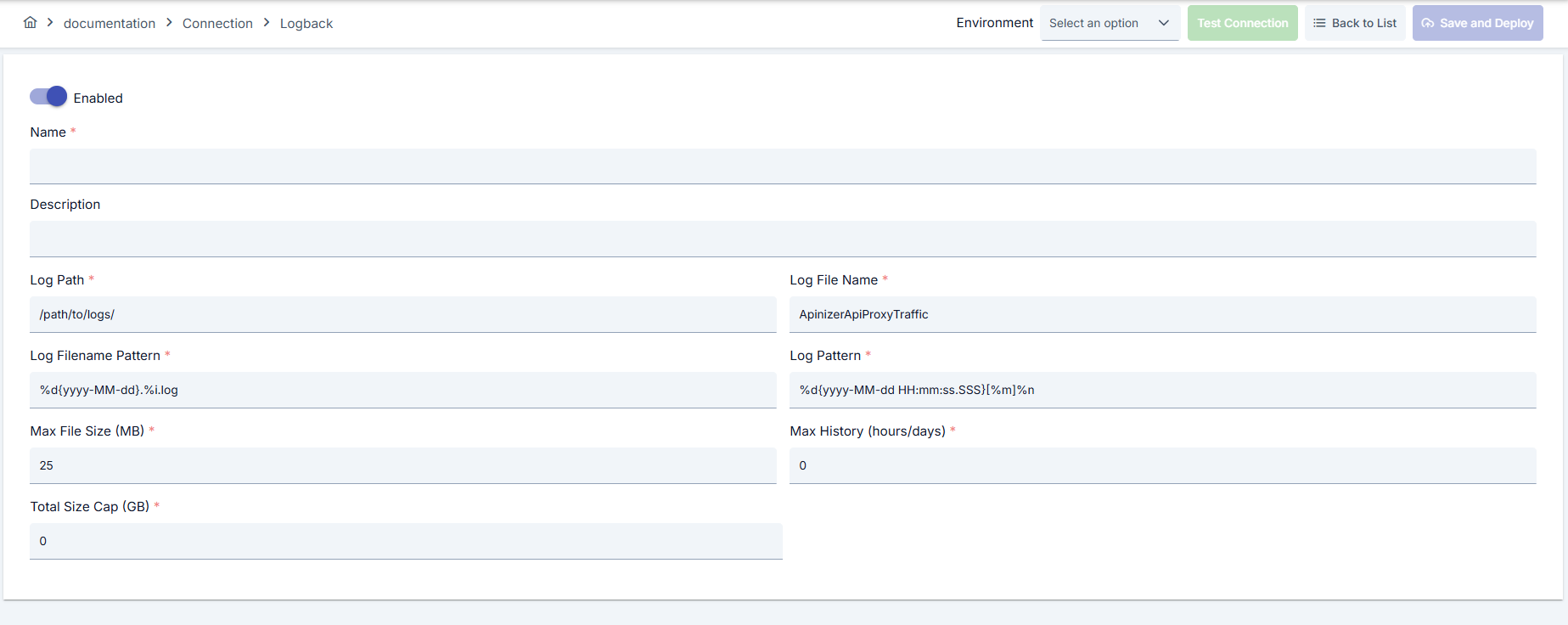
Navigate to Creation Page
- Go to Connection → Logback section from left menu.
- Click [+ Create] button at top right.
Enter Basic Information
Production_Logback- Enter unique name, cannot start with space.
- System automatically checks. Green checkmark: available. Red X: existing name.
- Max. 1000 characters.
- Describe the purpose of the Connection.
Environment Selection
- Select environment from dropdown menu: Development, Test, or Production.
- Different connection parameters can be defined for each environment.
Logback Specific Parameters - Directory and Naming
- Enter absolute directory that worker node can write to in logPath field.
- Determine RollingFileAppender file cycle with logFileName and logFilenamePattern fields; pay attention to containing date and index.
- Unauthorized directories produce errors during deployment.
Logback Specific Parameters - Content and Format
- Fill logPattern field with Logback conversion patterns, add thread name or request-id if needed.
- Use logPodName field if routing to specific pod is required.
Timeout and Connection Pool Settings
- Logback file writing has no separate timeout; if needed, update flush interval settings at JVM level through deployment descriptor.
- Set maxFileSize, maxHistory, totalSizeCap values appropriately according to operation policies for disk quotas.
Security and Authentication Settings
- Ensure worker node user account has write permission on logPath.
- Use file system ACLs or Kerberos-supported share points if needed.
- In production environment, allow only authorized service accounts to access shared directories.
Test Connection
- Click [Test Connection] button.
- Test whether connection parameters are correct.
- Success: Green confirmation message, Failed: Error details shown.
Save
- Click [Save and Deploy] button at top right.
- Connection is added to list.
- Becomes available in Integration Flow and Connector steps.
- Becomes active according to environment.
Deleting Connection
Delete Operation
Delete Tips
Alternative: Deactivate
Exporting/Importing Connection
Export
Export
Method 1
Method 2
File Format
Date-connection-Logback-export.zipExample:
13 Nov 2025-connection-Production_Logback-export.zipZIP Contents
- Connection JSON file
- Metadata information
- Dependency information (e.g., certificates, key store)
Use Cases
- Backup
- Moving between environments (Test → Prod)
- Versioning
- Team or project-based sharing
Import
Import
Import Steps
- Click [Import Logback] button on main list.
- Select downloaded ZIP file.
- System checks: Is format valid? Is there name conflict? Are dependencies present?
- Then click [Import] button.
Import Scenarios
Connection Usage Areas
Creating and Activating Connection
- Create the connection.
- Validate connection with Test Connection.
- Save and activate with Save and Deploy.
- Ensure connection is in Enabled state
Usage in Integration / Connector Steps
Scheduled Job Usage
Test Usage
Best Practices
Do's and Best Practices
Do's and Best Practices
Log Directory Selection
Good: Opening separate
/var/log/apinizer directory.Best: Granting permission only to service account on dedicated disk or mount point.
File Pattern Management
Good: Using daily dated pattern.
Best: Ensuring SIEM compatibility with pattern containing date + index and application name.
Storage Policy
Good: Setting reasonable values according to traffic.
Best: Setting automatic cleanup rules according to disk capacity, regulation, and backup processes.
Pod-Based Routing
Good: Using logPodName for problematic pods.
Best: Setting up separate directory for each pod + central collection pipeline.
Environment Management
Good: Creating separate connection for each environment.
Best: Managing all environments in single connection using Environment option, only changing environment during transitions between environments
Connection Test
Good: Validating with Test Connection before saving.
Best: Testing after every parameter change, performing full integration test in test environment before going to production
Security Best Practices
Security Best Practices
File System Access Control
Shared Storage Security
Log Content Masking
Credential Management
SSL/TLS Usage
Access Control
Don'ts
Don'ts
Writing to Shared Root Directory
Alternative: Use separately mounted log directory
Incorrect Date Pattern
Alternative: Use patterns containing
%dNot Defining Quota
Alternative: Set maxFileSize, maxHistory, and totalSizeCap values according to system capacity
Using Production Connection in Test Environment
Alternative: Create separate connection for each environment, use environment parameter, separate connection names by adding prefix according to environment (Test_, Prod_)
Very Low Timeout Values
Alternative: Adjust timeout values according to real usage scenarios, measure network latency and set timeouts accordingly
Not Using Connection Pool
Alternative: Enable connection pool, adjust pool size according to traffic volume, set up pool monitoring
Performance Tips
Performance Tips
Disk IO Optimization
noatime mount optionImpact: Write delays decrease, log recording becomes uninterrupted
Pattern Minimalism
Impact: CPU usage decreases, log throughput increases
Retention Automation
Impact: Disk fullness risks are eliminated, manual intervention need decreases
Connection Pool Optimization
Impact: Connection opening cost decreases by 80%, response times decrease, resource usage is optimized
Timeout Values Optimization
Impact: Unnecessary waits are prevented, fast fail-over is provided, user experience improves
Connection Monitoring
Impact: Problems are proactively detected, performance bottlenecks are identified early, downtime decreases
Troubleshooting
Log File Not Created
Log File Not Created
File Size Limit Exceeded
File Size Limit Exceeded
Connection Timeout
Connection Timeout
Authentication Failed
Authentication Failed
Pool Exhausted
Pool Exhausted
Connection Test Successful But Integration Flow Errors
Connection Test Successful But Integration Flow Errors
Frequently Asked Questions (FAQ)
What minimum parameters should I enter for Logback Connection?
What minimum parameters should I enter for Logback Connection?
Can I transfer logs to both file and external system simultaneously?
Can I transfer logs to both file and external system simultaneously?
What happens if I leave logPodName value empty?
What happens if I leave logPodName value empty?
If maxHistory and totalSizeCap conflict, which takes priority?
If maxHistory and totalSizeCap conflict, which takes priority?
How can I transfer logs to external SIEM tool?
How can I transfer logs to external SIEM tool?
Can I use the same connection in multiple Integration Flows?
Can I use the same connection in multiple Integration Flows?
Is using connection pool mandatory?
Is using connection pool mandatory?
Should I create different connections for Test and Production?
Should I create different connections for Test and Production?
Test Connection is successful but not working in Integration Flow, why?
Test Connection is successful but not working in Integration Flow, why?
- Connection enable toggle may be passive
- Different connection may be selected in Integration step
- Connection may not be deployed
- Integration Flow may not be redeployed yet

