When API traffic on API Proxies in Gateway Runtime environments needs to be recorded, the setting of where the relevant logs should be stored can be made with the following settings. The following connectors can be used to send API traffic in Gateway Runtime environments to other environments:
To examine the structure of the data to be sent to these connectors, you can check this document.

Common Fields in Connectors
When creating a connector, there are some input fields that are the same for each type. This information is shown in the selected fields in the image below.
| Field | Description |
|---|---|
| Configure API Proxy Traffic Log Setting Detail (Configure API Proxy Traffic Log Setting Detail) | When this setting is activated, the fields to be logged are selected. If there are long texts among the fields to be sent for logging, size limits can be set for these fields. |
| If enabled, all traffic logs of which API proxy is not found or not exists are also exported to target (If enabled, all traffic logs of which API proxy is not found or not exists are also exported to target) | With this setting, if desired, all traffic logs where the API Proxy is not found or does not exist are also exported to the target. |
| Configure API Proxy Traffic Privacy Setting (Configure API Proxy Traffic Privacy Setting) | When this setting is activated, data that is not desired to be accessed clearly within log records can be prevented from being displayed as is. Detailed information about this section is explained below. |
| If enabled, unsent requests will be sent to failover connector (If enabled, unsent requests will be sent to failover connector) | If the connector is offline or inaccessible, a new failover connection can be defined for log records that cannot be sent in this case. |
| Failover Connector Type (Failover Connector Type) | The type of the failover connector to be defined is selected. |
| Type | This field becomes active when the failover type is selected as Database (Database). Database type is selected. |
| Failover Connection (Failover Connection) | The failover connection to be defined according to the selected failover type is selected. |
| Operation (Operation) | This field becomes active when the failover type is selected as Database (Database). Operation type is selected. |
Configuring API Proxy Traffic Log Setting Details
When the “Configure API Traffic Log Setting Detail” option is enabled, you can customize how API traffic logs will be recorded. Apinizer logs are divided into four different regions according to the traffic flow in the system.API Traffic Log Regions
Apinizer logs API traffic in these four regions:- Request from Client (Request from Client)
- Request to Target (Request to Target)
- Response from Target (Response from Target)
- Response to Client (Response to Client)
For production environments, it is recommended to disable logging of elements belonging to the following regions:
- Request to Target (Request to Target)
- Response from Target (Response from Target)
Log Settings Screen
An image containing the log settings screen that appears when the “Configure API Traffic Log Setting Detail” option is enabled is shown below: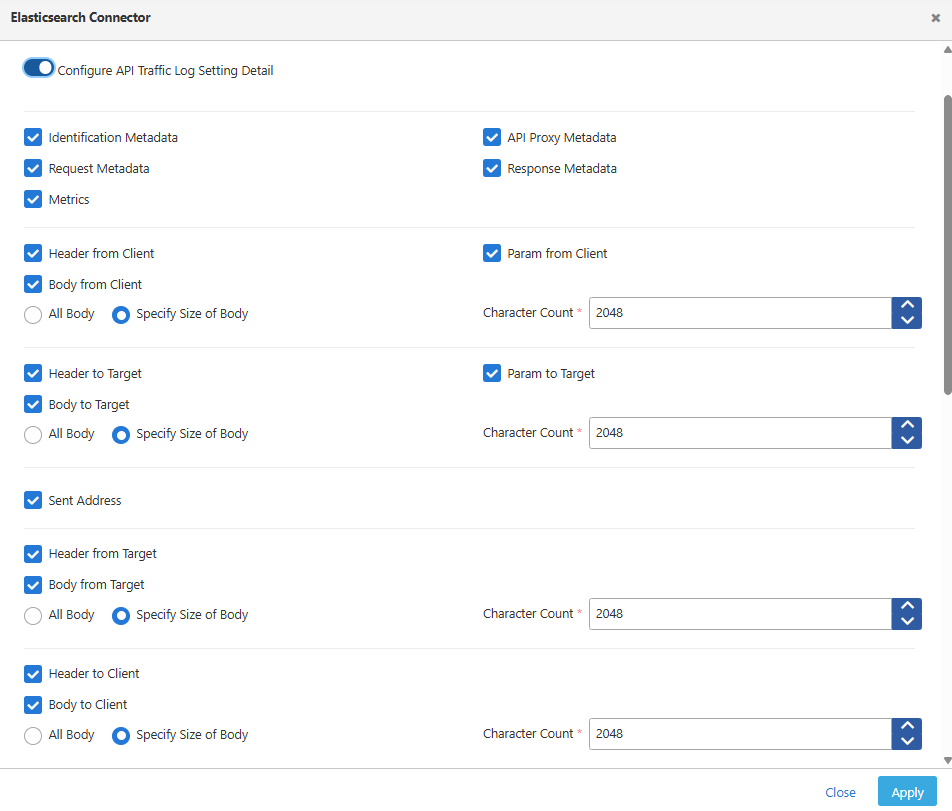
Customizable Log Fields
Fields that can be customized in API traffic log settings are given below. For each field, whether it will be logged or not can be selected, and size limits can be set for fields containing long texts.| Field | Description |
|---|---|
| Identification Metadata (Identification Metadata) | Records system identification information |
| Request Metadata (Request Metadata) | Captures request-specific metadata information |
| API Proxy Metadata (API Proxy Metadata) | Logs metadata information related to the proxy |
| Response Metadata (Response Metadata) | Records response-specific metadata information |
| Metrics (Metrics) | Captures performance and timing metrics |
| Header from Client (Header from Client) | Records all headers received from the client |
| Body from Client (Body from Client) | Captures the request body coming from the client |
| Param from Client (Param from Client) | Logs parameters received from the client |
| Header to Target (Header to Target) | Records headers sent to the backend |
| Body to Target (Body to Target) | Captures the request body sent to the backend |
| Param to Target (Param to Target) | Logs parameters sent to the backend |
| Sent Address (Sent Address) | Records address information for the request |
| Header from Target (Header from Target) | Records headers received from the backend |
| Body from Target (Body from Target) | Captures the response body coming from the backend |
| Header to Client (Header to Client) | Records headers sent to the client |
| Body to Client (Body to Client) | Captures the response body sent to the client |
Size Limits
If there are long texts among the fields to be sent for logging, size limits can be set for these fields. This way, the size of log records can be kept under control and storage space in the database or log target system can be optimized. A separate size limit can be determined for each field. When the determined limit is exceeded, the content of the relevant field is logged by truncating it or can be completely skipped.Configuring API Proxy Traffic Privacy Settings
Apinizer keeps records of message traffic (request and response) flowing through Apinizer. Sensitive or personal data such as credit card information, password, phone number may be present in any part of the messages (header, parameter, body). When it is not desired for this data to be accessed clearly within log records, Apinizer can prevent the data from being displayed as is by applying the following operations to fields carrying sensitivity/privacy within log records with “API Proxy Traffic Privacy Settings”:For API Proxy-based log settings, you can check the API Traffic Log Settings section on the API Proxy Configuration - Settings Tab page.
- Masking: A mask is applied to the field’s value with the * sign.
- Deletion: The field’s value is deleted while logging.
- Encryption: The field’s value is encrypted with a salt code generated on an application basis.
- Hashing: The field’s value is logged by hashing it.
Applying Privacy Settings
At the time of log record creation, scanning is performed on the “header, parameter, and body” fields of request and response messages with the element names defined. For found element names, the operation (masking, deletion, encryption, hashing) defined specifically for the element name is applied. For the element name to be searched on the request or response body, the body value must be XML, JSON, or Form data (form-data, x-www-form-urlencoded). If the data is XML or JSON, the “sensitive data element name” value is searched in all element names (recursively), if it is form data, it is searched in all keywords, and if found, the relevant operation (masking, deletion, encryption, hashing) is applied to the element value if XML or JSON, or to the value corresponding to the key if form data. The “-PA” suffix is also added to the end of the relevant element/key name on the data to indicate that the operation was performed. PA: Privacy Applied. For “API Proxy Traffic Privacy Settings” to be applied per defined field, scanning is performed in all of the following fields:- Header, Query Parameter, and Body of Message Coming from Client
- Header, Query Parameter, and Body of Message Going to Backend
- Header and Body of Message Returning from Backend
- Header and Body of Message Returning to Client
Definitions Screen
The Activate option must be active to activate “API Proxy Traffic Privacy Settings”. An image containing the screen that appears when API Proxy Traffic Privacy Settings is activated is shown below:
If an API Proxy does not exist, all definitions are applied to incoming requests.

